Operation Triangulation: Leveraged by Exploiting an Undocumented Hardware Feature in iOS Devices
Reading Time: 3 Minutes
A recent discovery by experts has revealed that the Operation Triangulation cyberespionage campaign, targeting Apple iOS devices, exploited an undocumented hardware feature. Researchers from the Russian cybersecurity firm Kaspersky uncovered this revelation, shedding light on the sophisticated tactics employed by threat actors to target iOS devices.
The campaign, which began at least in 2019 and is still ongoing, was uncovered by Kaspersky while monitoring network traffic on their corporate Wi-Fi network dedicated to mobile devices using the Kaspersky Unified Monitoring and Analysis Platform (KUMA).
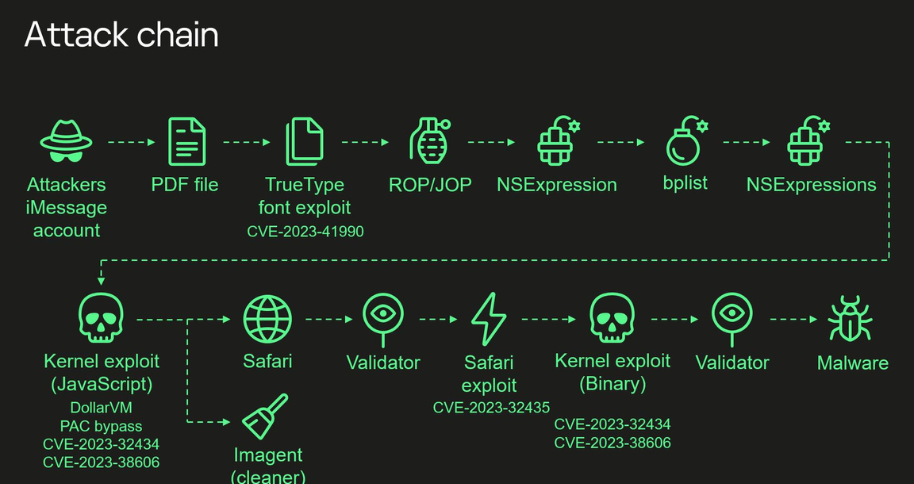
Operation Triangulation utilized zero-click exploits, with the attack chain commencing through a message sent via the iMessage service to an iOS device. This message contained an attachment that triggered a remote code execution vulnerability without any user interaction.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Following Kaspersky’s disclosure, Russia’s FSB accused US intelligence of orchestrating the attacks against iPhones, targeting thousands of iOS devices belonging to domestic subscribers, diplomatic missions, and embassies as part of Operation Triangulation. The operations aimed at gathering intelligence from diplomats of various countries.
The attack chain relied on the exploitation of four zero-day vulnerabilities impacting iOS versions up to iOS 16.2, allowing threat actors to gain root privileges on the target iOS device and install the spyware implant, tracked as TriangleDB. The implant, directly deployed in memory, uninstalls itself after 30 days if the system is not rebooted, although attackers can extend this period.
The researchers also discovered that the attackers exploited an undocumented, Apple-only ADJUST TrueType font instruction, as well as an integer overflow vulnerability and a bypass of the Page Protection Layer (PPL) to execute a shellcode and another kernel exploit.

Notably, the attackers abused a hardware feature of Apple-designed SoCs to bypass hardware-based security protections, raising questions about the origin and purpose of this unknown hardware feature.
Trending: OSINT Tool: sn0int
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: securityaffairs.com













