‘Operation Triangulation’ Malware Strikes iOS Devices Worldwide

Cybersecurity firm Kaspersky has taken a significant step in the battle against a new form of malware called ‘Triangulation’ that specifically targets Apple iPhones and other iOS devices. Discovered within their own network, Kaspersky detected infections across their global premises, dating back to at least 2019.
Operating under the campaign name ‘Operation Triangulation,’ this malware utilizes an undisclosed zero-day exploit in Apple’s iMessage platform, enabling it to execute code without user interaction or elevated privileges. Once infiltrated, the malware proceeds to download additional malicious payloads to the compromised device, allowing for further command execution and data collection.
What’s particularly concerning is the apparent connection between the ‘Triangulation’ malware and the Russian intelligence and security service known as the FSB. According to Kaspersky, high-ranking government officials and foreign diplomats have fallen victim to this insidious campaign.
The Triangle iOS Scanner
Initially, Kaspersky provided manual instructions on how to check iOS device backups for signs of compromise using their Mobile Verification Toolkit (MVT). However, they have now released a more user-friendly solution—a sophisticated automated scanner called Triangle. This powerful tool is available for both Windows and Linux operating systems.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
To analyze an iOS backup, as live system analysis is prevented by Apple’s robust security mechanisms, users are required to follow specific steps based on their operating system.
Windows
For Windows users, the device should be connected to a computer with iTunes installed. After confirming trust between the device and the computer, the user can create a backup by right-clicking on the device within iTunes and selecting “Back Up.” The backup will then be saved in the %appdata%\Apple Computer\MobileSync\Backup directory.
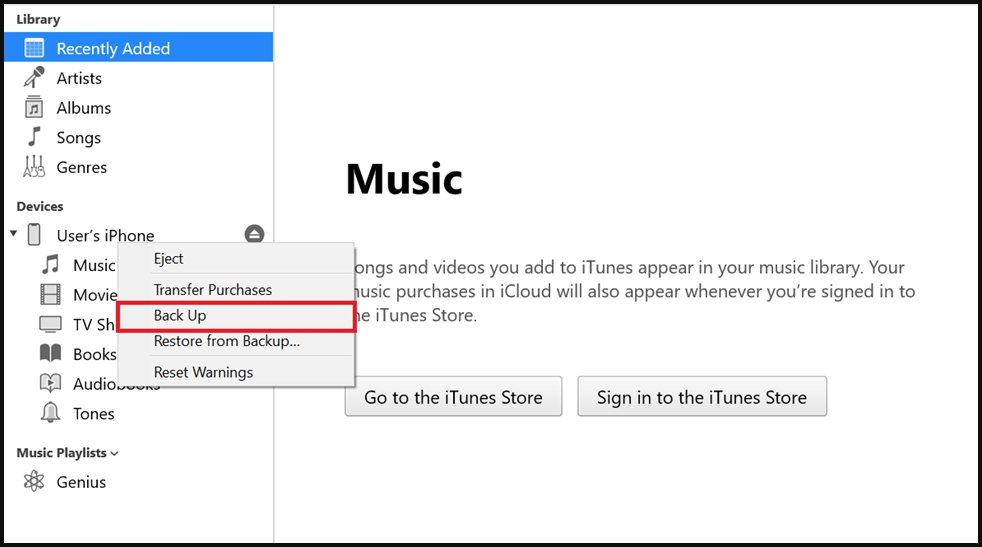 Creating an iOS backup through iTunes (Kaspersky)
Creating an iOS backup through iTunes (Kaspersky)
macOS
On macOS, the process involves connecting the device to the computer, confirming trust, and selecting the device in Finder. From there, users can click “Create a backup” to generate the backup file, which will be saved in the ~/Library/Application Support/MobileSync/Backup/ directory.
Linux
Linux users need to install the “libimobiledevice” library and connect the device to the computer. Using the “idevicebackup2 backup –full” command, a backup can be created while entering the device passcode as requested.
Kaspersky’s Triangle scanner is available as a Python package on PyPI or as binary builds for Windows and Linux on their public GitHub repository. By following the provided instructions, users can launch the tool and point it to the location of the iOS backup for analysis.
Upon launching Triangle and scanning the iOS backup, the tool will produce one of three possible results: “DETECTED” indicates a confirmed infection of the “Operation Triangulation” malware, “SUSPICION” suggests potential indicators of compromise, but not enough evidence for a conclusive result, and “No traces of compromise were identified” signifies no signs of compromise related to this specific malware family.
However, it’s essential to note that even negative results may not guarantee absolute device cleanliness, as ongoing analysis of the malware may uncover additional indicators of compromise or newer variants targeting recent iOS releases.
Trending: Offensive Security Tool: Pyramid
Malware Campaign
Typically, malware campaigns like “Operation Triangulation” are aimed at specific individuals or organizations rather than the general public. However, Kaspersky’s Triangle tool can provide valuable assistance to those in critical roles within important organizations, individuals at higher risk of state-sponsored espionage, and employees of companies or services acting as information hubs.
While the exact origins and orchestrators of Operation Triangulation remain unknown, the campaign’s targeting scope and victimology have yet to be determined, heightening the need for vigilance and proactive measures to safeguard iOS devices.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












