Outlook – Microsoft Patches Critical Flaw Leaking NTLM Passwords

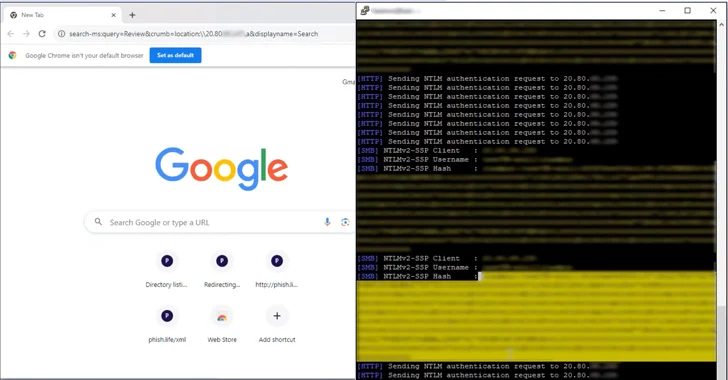
A recently addressed security flaw in Microsoft Outlook posed a potential risk of unauthorized access to NT LAN Manager (NTLM) v2 hashed passwords. Tracked as CVE-2023-35636 with a CVSS score of 6.5, Microsoft resolved the issue as part of its December 2023 Patch Tuesday updates.
Exploitation of this vulnerability involves the calendar-sharing function in Outlook. In a scenario where an attacker could convince a user to open a specifically crafted file, the flaw could be triggered, potentially exposing NTLM v2 hashed passwords. This could occur through phishing emails containing malicious links or deceptive instant messages.
varonis.com
The vulnerability, reported by Varonis security researcher Dolev Taler, involves the insertion of two headers, “Content-Class” and “x-sharing-config-url,” with carefully crafted values in a malicious email message. When a victim opens this manipulated file, their NTLM hash becomes susceptible during authentication.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
It’s noteworthy that the disclosed flaw has additional dimensions, with potential NTLM hash leaks through the Windows Performance Analyzer (WPA) and Windows File Explorer. While the primary vulnerability is patched, these attack vectors remain unaddressed.
Of particular interest is Taler’s revelation that WPA attempts to authenticate using NTLM v2 over the open web. Ordinarily, NTLM v2 should be confined to internal IP-address-based services. However, when this hash traverses the open internet, it becomes vulnerable to relay and offline brute-force attacks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













