Over 1.3 Million Android Devices Infected: Vo1d Malware Campaign Exposed

Massive Malware Campaign Targets Over 1.3 Million Android Streaming Devices Researchers have uncovered a widespread malware campaign that has infected over 1.3 million Android TV streaming boxes across more than 200 countries. The malware, dubbed Vo1d, allows threat actors to take full control of infected devices, posing a serious security risk. Targeted countries include Brazil, Pakistan, Saudi Arabia, Russia, and more.
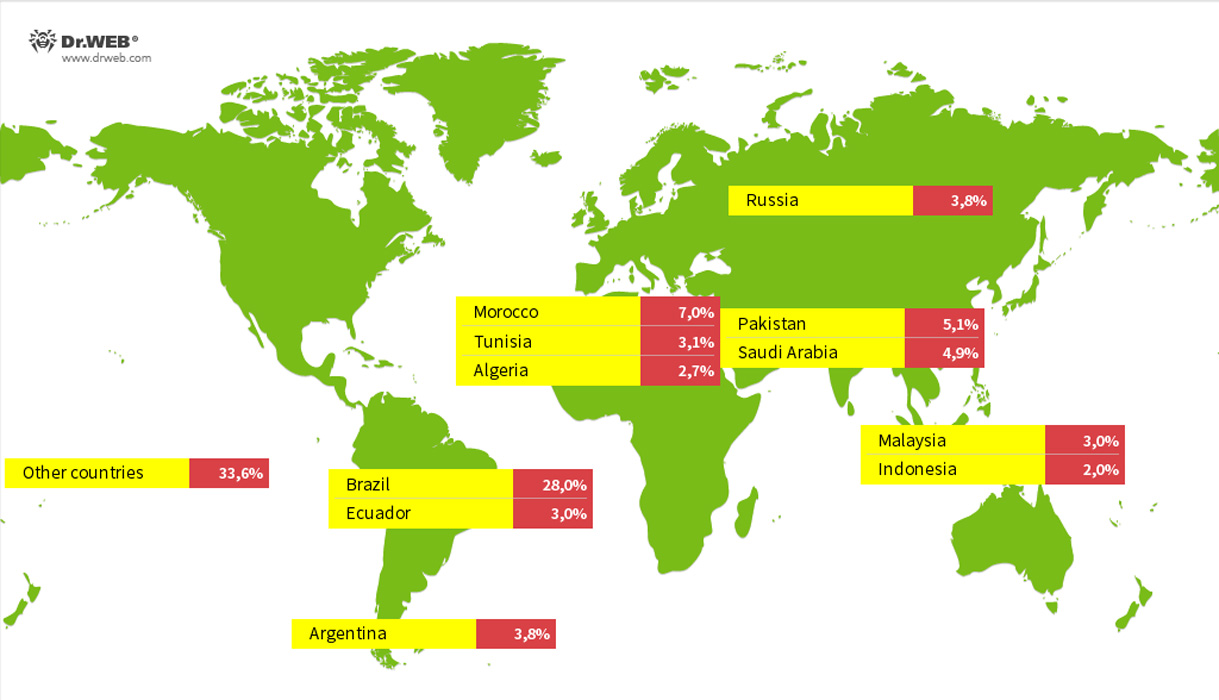 Geographic distribution of Vo1d-infected TV boxes
Geographic distribution of Vo1d-infected TV boxes
Source: Dr.Web
Infection Process
The infection typically occurs due to several key factors, including outdated software, unofficial firmware, and weak network security. Here’s how these devices are compromised:
- Exploiting Outdated Android Firmware: Many of the targeted devices are running older versions of Android firmware, such as Android 7.1.2, Android 10.1, and Android 12.1. These versions often contain unpatched vulnerabilities, which cybercriminals exploit to gain root privileges on the device. Root access provides attackers with full administrative control, allowing them to install malware, modify system files, and bypass any built-in security mechanisms.
- Unofficial Firmware with Built-in Root Access: Another key factor in the infection is the use of unofficial firmware versions on these devices. Some off-brand TV streaming boxes come preloaded with firmware that includes built-in root access. This makes it much easier for attackers to deploy malware, as they don’t need to find a vulnerability to gain administrative privileges—root access is already available. This leaves the devices highly vulnerable to malware attacks, including the Vo1d backdoor.
- Installation of Malicious APKs: One of the most common ways the malware is introduced is through the installation of malicious APK files (Android Package Kit). Users often download APKs from unverified third-party sites, believing them to be legitimate apps. However, these APKs can carry malware, like Vo1d, which exploits system vulnerabilities. Once installed, the malware gains a foothold and takes advantage of the system’s weaknesses to escalate its control over the device.
- Network Vulnerabilities and Exposed Services: Many of these streaming devices lack proper security configurations and are exposed to the internet with open services or weak firewalls. This allows attackers to remotely exploit these vulnerabilities, gaining unauthorized access without any direct interaction from the user. In such cases, attackers may launch targeted attacks to install the malware, even if the user has not downloaded any malicious apps.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How the Vo1d Malware Works
Once the malware infects a device, it employs several sophisticated techniques to maintain persistence, execute malicious actions, and allow attackers to control the device remotely.
- Modifying Android System Files for Persistence: Vo1d malware modifies critical Android system startup scripts to ensure it runs automatically every time the device is restarted. The specific files that are altered include:
- install-recovery.sh
- daemonsu
- debuggerd
These scripts are responsible for managing processes that start when the device boots up. By modifying them, Vo1d ensures that it is launched every time the device powers on, maintaining persistence even after reboots. This makes it challenging to remove the malware without a complete system wipe.

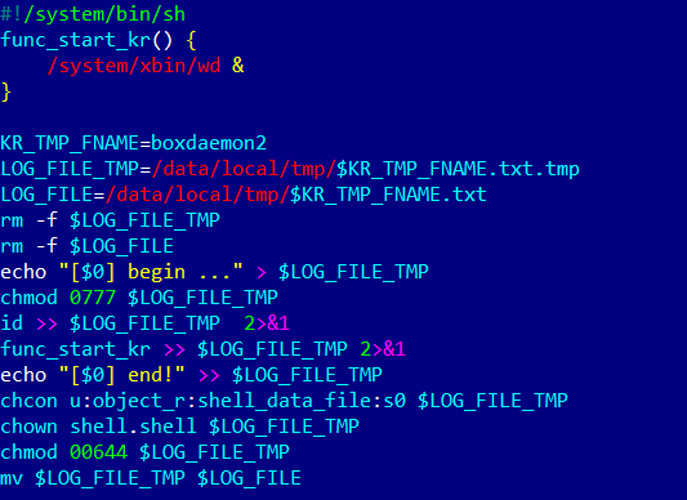
Modified install-recovery.sh file
Source: Dr.Web - Main Components of Vo1d Malware: The malware operates using two key components that work in tandem:
- Android.Vo1d.1: This is the primary module responsible for controlling the malware’s operations. It ensures the malware remains active by restarting processes if they stop and can download and execute additional malicious payloads. It also communicates with the Command and Control (C&C) server, receiving instructions and downloading new malware updates or executables as directed.
- Android.Vo1d.3: This component installs and launches an encrypted daemon known as Android.Vo1d.5, which runs covertly on the device. It also monitors specific directories on the device, searching for APK files. If it finds any, it automatically installs them, allowing the attackers to deploy more malware or spy apps without the user’s knowledge.
- Remote Control via C&C Server: One of the most dangerous aspects of Vo1d is its connection to a Command and Control (C&C) server, which gives attackers remote access to the compromised device. Through this server, attackers can:
- Execute commands on the device.
- Download and install additional malware.
- Steal sensitive data or spy on the user’s activity.
- Launch attacks on other devices connected to the same network.
This remote control capability means that once a device is infected, it can be used for a variety of malicious activities, including turning the device into part of a botnet or using it to launch attacks on other systems.
- Hidden and Covert Operations: Vo1d operates covertly, making it difficult for users to detect. The altered system files and persistent startup scripts enable the malware to remain active without causing noticeable disruption to the device’s primary functions. Users are often unaware their device has been compromised until it begins exhibiting unusual behavior, such as slowing down, crashing, or running unexpected applications.
Trending: Recon Tool: FinalRecon
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com