Over 178,000 SonicWall Firewalls Exposed to DoS and Remote Code Execution Threats

Security researchers have identified a substantial security risk involving more than 178,000 SonicWall next-generation firewalls (NGFW) with exposed online management interfaces. These devices are vulnerable to denial-of-service (DoS) attacks and potential remote code execution (RCE).
The affected appliances are at the mercy of two DoS security flaws, namely CVE-2022-22274 and CVE-2023-0656. The former not only facilitates DoS attacks but also opens the door for attackers to achieve remote code execution.
Jon Williams, a Senior Security Engineer at Bishop Fox, shared insights on the extensive attack surface: “Using BinaryEdge source data, we scanned SonicWall firewalls with management interfaces exposed to the internet and found that 76% (178,637 of 233,984) are vulnerable to one or both issues.”
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Despite both vulnerabilities stemming from the same vulnerable code pattern, they exploit different HTTP URI paths. Bishop Fox, the entity discovering this massive attack surface, clarified this distinction.
Williams noted, “Our initial research confirmed the vendor’s assertion that no exploit was available; however, once we identified the vulnerable code, we discovered it was the same issue announced a year later as CVE-2023-0656.”
Even if attackers can’t execute code, they can force targeted appliances into maintenance mode, necessitating administrator intervention to restore normal functionality. While the extent of remote code execution is undetermined, these vulnerabilities empower attackers to disable edge firewalls and associated VPN access to corporate networks.
With over 500,000 SonicWall firewalls currently exposed online, including 328,000 in the United States, administrators are urged to secure their SonicWall NGFW appliances by ensuring the management interface is not exposed online and promptly upgrading to the latest firmware versions.
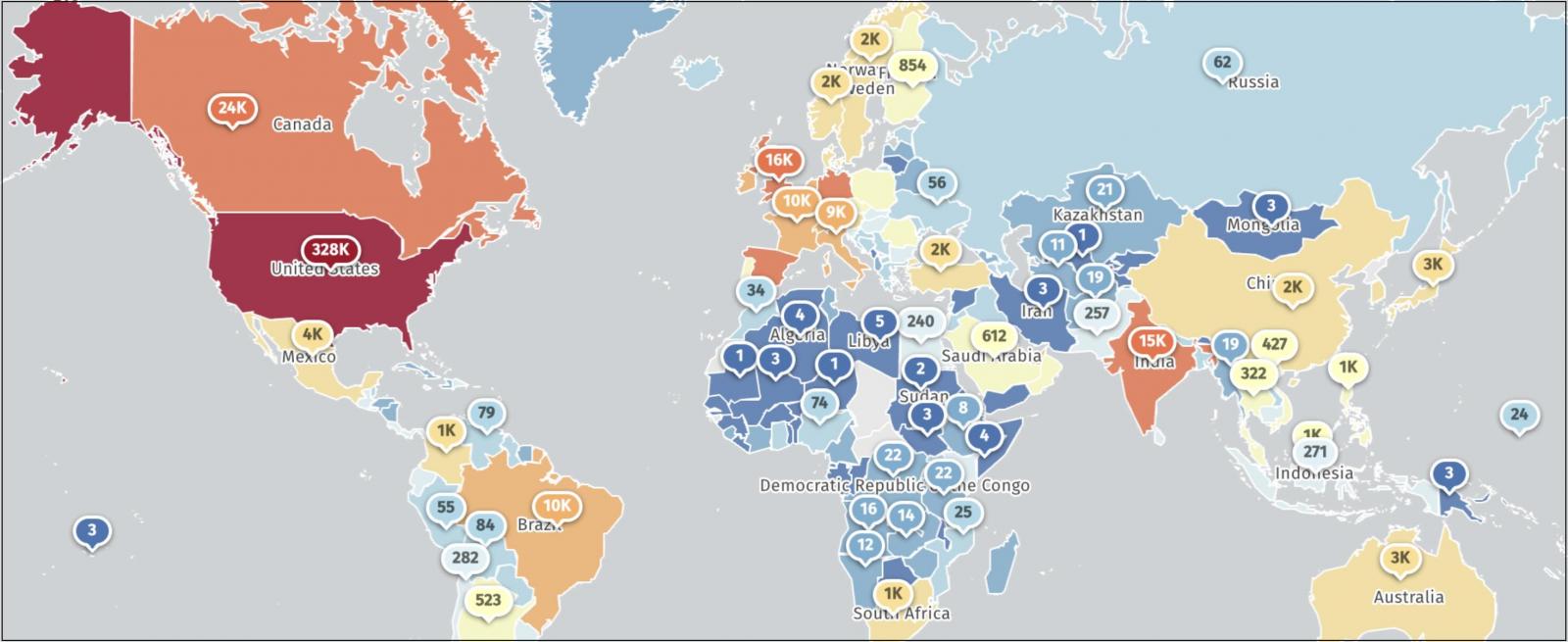 Internet-exposed SonicWall firewalls (ShadowServer)
Internet-exposed SonicWall firewalls (ShadowServer)
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













