PDF Feature ‘Certified’ Widely Vulnerable to Attack

Reading Time: 1 Minute
Certified portable document format (PDF) files are used to securely sign agreements between two parties while keeping the contents’ integrity protected, but a new report found the security protections on most certified PDF applications were inadequate and left organizations exposed to a number of attacks.
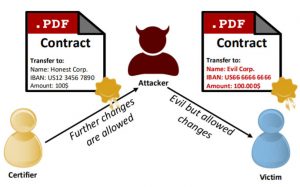
Researchers from Ruhr University Bochum explained certified PDFs use two specific signatures to authenticate the document, an Approval signature and a Certification signature. Certification signatures are the more flexible and made to handle complicated agreements between multiple parties and allow some changes to the document within a set of parameters while still maintaining its validity.
Unsurprisingly, Certified signatures are where the team found vulnerabilities to two specific novel attacks they dubbed, “Evil Annotation” (EAA) and “Sneaky Signature” (SSA). Both allow an attacker to overlay malicious content (PDF) on top of the certified information without showing any signs it was altered.
Novel Certified PDF Attacks
EAAs display malicious content in the document’s annotations and then sends it on with its digital signature intact. SSAs add malicious content over legitimate content in the PDF itself.
The team said the results of its evaluation of the 26 most popular PDF applications were “alarming.”
See Also: Pulse Secure VPNs Get Quick Fix for Critical RCE
“In only 2 cases, we could not find a vulnerability; 15 viewers were vulnerable to EAA, 8 to SSA, including Adobe, Foxit, and LibreOffice,” the report said. “We additionally analyzed the standard-compliant implementation of PDF certification applications and found issues in 11 of them.”
Adobe had an additional flaw that allowed certified documents to execute JavaScript code, opening these users to code in injection attacks.
 “For example, a high-level JavaScript can call an arbitrary URL without user confirmation to deanonymize a user. Our research reveals that such code is also executed if it is added as an allowed incremental update. We are the first to reveal that this behavior allows attackers to directly embed malicious code into a certified document.
“For example, a high-level JavaScript can call an arbitrary URL without user confirmation to deanonymize a user. Our research reveals that such code is also executed if it is added as an allowed incremental update. We are the first to reveal that this behavior allows attackers to directly embed malicious code into a certified document.
The team said it disclosed their findings to the appropriate vendors and provided a comprehensive vulnerability report, including exploits, to CERT-Bund (BSI). The report also lists the specific certified PDF security flaws found in each application.
“Adobe, Foxit, and LibreOffice responded quickly and provided patches for late 2020 (CVE-2020-35931) or early 2021 (CVE2021-28545, CVE-2021-28546),” the report said. “Adobe fixed the code injection vulnerability in early Nov. 2020 within a patch outside the regular update cycle (CVE-2020-24432). Currently, we participate in the standardization process via the German National Organization for Standardization (DIN) and the International Organization for Standardization (ISO) to address the reported attacks in the next PDF specification.”
See Also: Offensive Security Tool: Snallygaster
Stopping Certified PDF Attacks
To fend off Evil Annotation Attacks, the researchers recommend admins prohibit three particularly risky annotations that allow text or images to be added to a certified PDF, “FreeText, Stamp and Redact.”
Sneaky Signatures can be blocked by reducing permissions, but that is not a guarantee SSAs won’t get through. Defined signature fields offer an additional layer of protection, the report said.
“Signature fields must be set up at defined locations in the PDF document before the document is certified,” the report explained. “A subsequent addition of signature fields must be penalized with an invalid certification status. Otherwise, it can always be used to add text or images included in the signature at any position.”
Adobe JavaScript code injections are trickier since in most cases the execution starts the moment the document is opened. “The only requirement is that the victim fully trusts the certificate used to certify the PDF document,” the report said.
See Also: Hacking Stories: Xbox Underground
Earlier this month Adobe Acrobat issued a patch for a zero-day bug targeting Windows users. Just days later, researchers at Microsoft Security Intelligence (MSI) found PDFs were being used by attackers to deliver StrRAT Java-based remote access tool (RAT) used to steal credentials, log keystrokes and take remote control over infected systems.
The flexibility offered by Certified signatures presents a massive, potentially catastrophic, security risk for many organizations and the report urges PDF applications to work quickly to come up with wide-scale fixes.
“The research community has struggled with similar problems on other data formats, such as XML or Email, without finding a satisfying solution so far,” they said. “In the case of PDF, the specification must be updated to address these issues.”
Source: threatpost.com



