PIXHELL: New Acoustic Attack Leaks Data from Air-Gapped Systems via LCD Screens

A novel acoustic attack called PIXHELL can exfiltrate sensitive data from air-gapped and audio-gapped systems by exploiting the LCD monitors connected to them.
Attack Methodology
The PIXHELL attack works by modulating pixel patterns on the screen to generate acoustic noise in the 0-22 kHz frequency range, which carries encoded signals. Nearby devices, such as smartphones or compromised laptops, can capture these signals and decode them.
 PIXHELL attack setting
PIXHELL attack setting
Source: Arxiv.org
Tests have shown that the attack can transmit data at a rate of 20 bits per second (bps) over a maximum distance of 2 meters (6.5 ft). While this data rate is slow, it is sufficient for real-time keylogging and small text file exfiltration, including passwords and encryption keys.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Covert Audio Channel Exploitation
PIXHELL was developed by Dr. Mordechai Guri from Ben-Gurion University of the Negev, known for his research into data exfiltration from air-gapped systems. The method capitalizes on unintended acoustic emissions from LCD screens, caused by coil whine, capacitor noise, or intrinsic vibrations.
Attackers can use malware to encode data into the acoustic signals using modulation schemes such as:
- On-Off Keying (OOK): Data is encoded by turning sound on and off.
- Frequency Shift Keying (FSK): Data is encoded by switching between frequencies.
- Amplitude Shift Keying (ASK): Data is encoded by altering the sound’s amplitude (volume).
 Modulating acoustic signals at various frequences
Modulating acoustic signals at various frequences
Source: Arxiv.org
These signals are transmitted through the LCD screen by changing pixel patterns, which generates the necessary sound. A nearby microphone-equipped device can capture these signals for later transmission to an attacker for decoding.
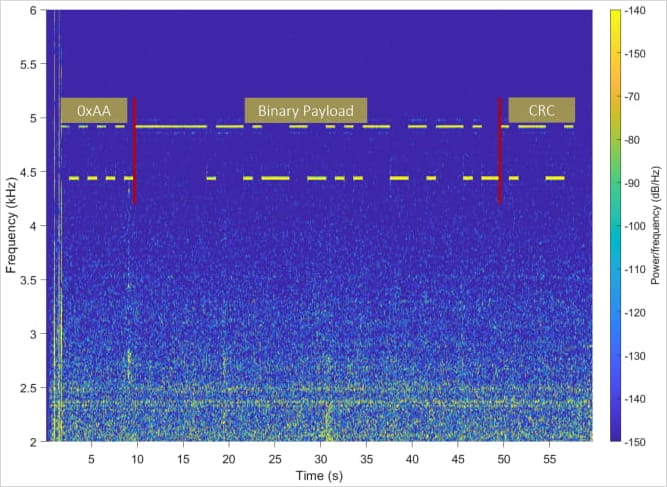 Spectrogram of acoustic signal received by a nearby microphone
Spectrogram of acoustic signal received by a nearby microphone
Source: Arxiv.org
Stealthy and Efficient
The frequencies used in PIXHELL attacks are typically in the 0-22 kHz range, which is mostly inaudible to humans. At the same time, the pixel patterns used in the attack are low-brightness or invisible to the user, making the attack extremely stealthy.
In a setting with multiple infected air-gapped systems, PIXHELL can exfiltrate data from all of them simultaneously.
Trending: Recon Tool: FinalRecon
Mitigation Strategies
Several defense mechanisms can be employed against PIXHELL and other acoustic-based side-channel attacks, such as:
- Banning microphones in sensitive areas to prevent data capture.
- Jamming or introducing background noise to disrupt acoustic signals.
- Monitoring screen buffers with a camera to detect unusual pixel activity.
Complete technical details of the PIXHELL attack and suggested countermeasures are available in the research paper titled “PIXHELL Attack: Leaking Sensitive Information from Air-Gap Computers via ‘Singing Pixels’.”
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













