Pumakit: A Stealthy Linux Rootkit Targeting Pre-5.7 Kernels

Pumakit: A New Linux Rootkit with Advanced Stealth and Privilege Escalation
A newly identified Linux rootkit malware, named Pumakit, has been discovered leveraging stealthy techniques and advanced privilege escalation methods to evade detection and compromise systems. This sophisticated malware consists of multiple components, including a dropper, memory-resident executables, a kernel module rootkit, and a shared object (SO) userland rootkit.
Discovery and Attribution
Elastic Security identified Pumakit from a suspicious binary named ‘cron’ uploaded to VirusTotal on September 4, 2024. While details about its deployment or specific targets remain unclear, such tools are commonly used by advanced threat actors aiming at critical infrastructure and enterprise systems for espionage, financial theft, and operational disruption.
The Pumakit Malware Architecture
Multi-Stage Infection Process
Dropper Execution: The infection begins with the execution of a dropper called ‘cron,’ which runs embedded payloads (‘/memfd:tgt’ and ‘/memfd:wpn’) entirely from memory.
Kernel Module Deployment: The ‘/memfd:wpn’ payload conducts environment checks and kernel image manipulation before deploying the LKM rootkit module (‘puma.ko’) into the system kernel.
Userland Rootkit Injection: The LKM rootkit embeds the Kitsune SO (‘lib64/libs.so’) userland rootkit. Kitsune uses the
LD_PRELOADmechanism to intercept and manipulate system calls at the user level.
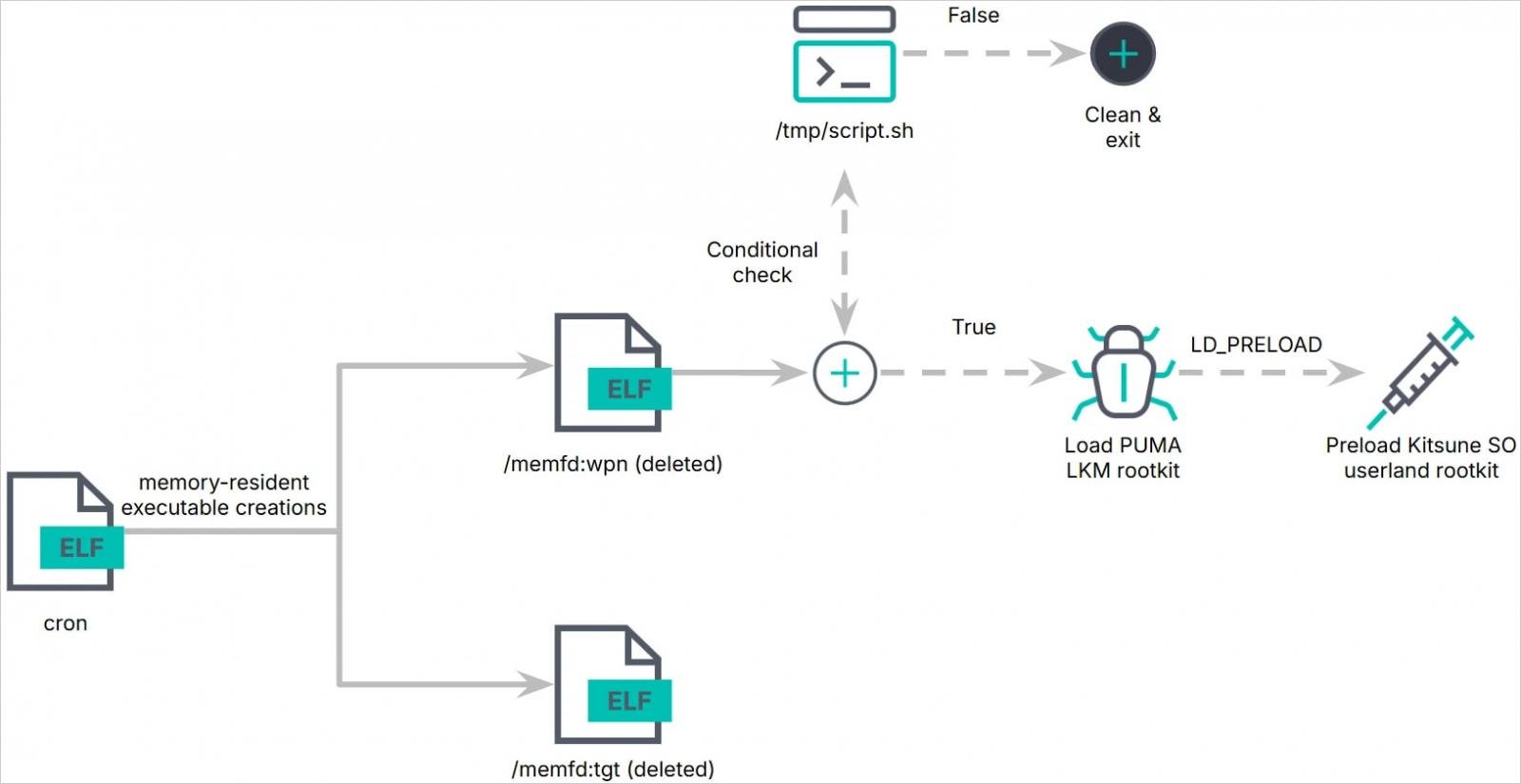 Pumakit infection chain
Pumakit infection chain
Source: Elastic Security
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Privilege Escalation and System Manipulation
Pumakit uses the following advanced techniques:
Kernel Symbol Checks: It verifies kernel symbols and secure boot status, ensuring it activates only in suitable environments.
Syscall Table Manipulation: The rootkit hooks 18 syscalls and several kernel functions using the
ftraceinterface.Privilege Escalation: By abusing kernel functions like
prepare_credsandcommit_creds, the rootkit modifies process credentials to grant root privileges.Self-Persistence: Pumakit automatically reinitializes its hooks if interrupted, ensuring its malicious modifications remain active and preventing module unloading.
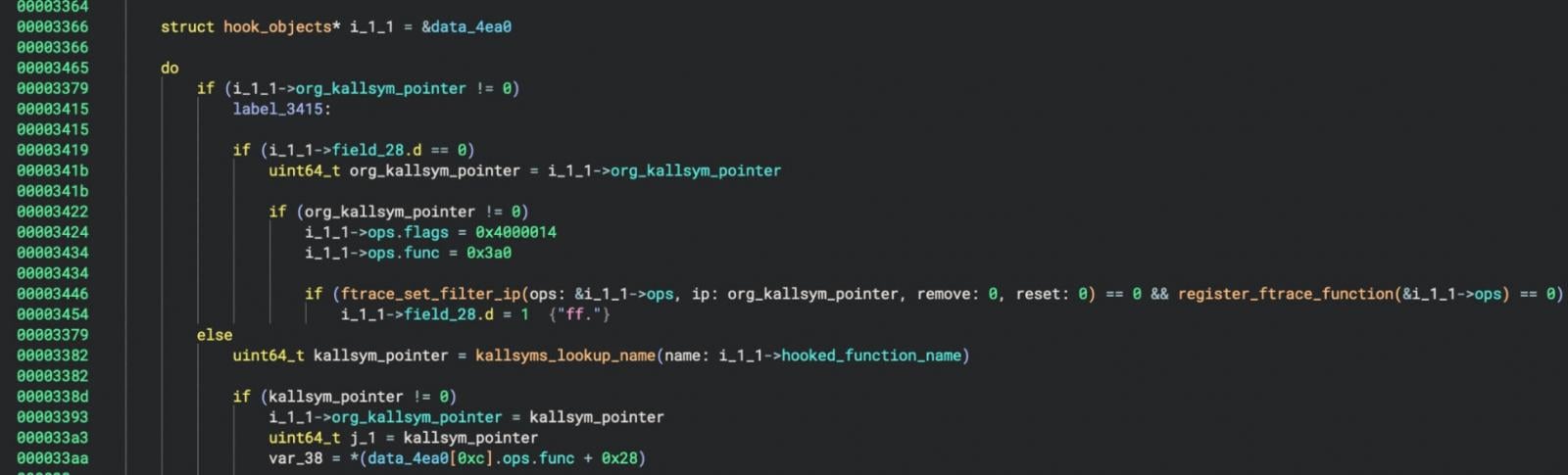 Using ftrace to hook syscalls
Using ftrace to hook syscalls
Source: Elastic Security
Hiding Mechanisms
Kernel-Level Obfuscation: Pumakit hides its presence from system logs, tools, and antivirus programs.
Userland Stealth: Kitsune SO intercepts user-level system calls and alters the behavior of commands such as
ls,ps,netstat,top,htop, andcatto conceal files, processes, and network connections related to the rootkit.Dynamic File Hiding: Attackers can dynamically configure hidden files, directories, and binaries, making them invisible to system administrators.
Command and Control (C2)
Kitsune SO manages communication with the command and control (C2) server. It relays commands to the LKM rootkit and transmits configuration details and system information back to the operators. This tight integration allows the malware to maintain control over compromised systems effectively.
Trending: Recon Tool: Argus
Detection and Mitigation
Pumakit’s use of stealthy, memory-resident techniques makes it challenging to detect. However, Elastic Security has published file hashes and a YARA rule to assist Linux administrators in identifying Pumakit infections. Recommended actions include:
Inspect for Suspicious Files: Look for hidden files and directories manipulated by the rootkit.
Monitor System Behavior: Pay attention to unusual system behavior, such as unexplained privilege escalations or concealed processes.
Update Kernel Versions: Since Pumakit targets kernels before version 5.7, updating to a more recent kernel version can prevent exploitation of
kallsyms_lookup_name().Apply YARA Rules: Utilize the provided YARA rules to detect Pumakit artifacts on systems
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













