Pwn2Own Vancouver 2024: Security Researchers Rack Up $1.13M with 29 Zero-Day Exploits

The Pwn2Own Vancouver 2024 concluded with a remarkable showcase of cybersecurity prowess, as participating security researchers amassed a staggering $1,132,500 in prize money by uncovering 29 zero-day exploits (alongside some bug collisions).
Spanning two intense days, the event witnessed targeted attacks on a diverse array of software and products encompassing categories such as web browsers, cloud-native/container systems, virtualization platforms, enterprise applications, servers, local escalation of privilege (EoP), enterprise communications, and automotive technologies. Notably, all targets were up-to-date and operating in their default configurations.
With a total prize pool exceeding $1.3 million in cash rewards and a coveted Tesla Model 3, the competition kicked off with a significant win by Team Synacktiv, securing the Tesla car on the inaugural day.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Throughout the event, competitors demonstrated their prowess by achieving code execution and escalating privileges on fully patched systems. Notable targets included Windows 11, Ubuntu Desktop, VMware Workstation, Oracle VirtualBox, as well as popular web browsers such as Apple Safari, Google Chrome, and Microsoft Edge. Even the Tesla Model 3 fell victim to successful exploitation.
However, vendors are now on the clock, having 90 days to release security fixes for the zero-day vulnerabilities reported during Pwn2Own contests before TrendMicro’s Zero Day Initiative discloses them publicly.
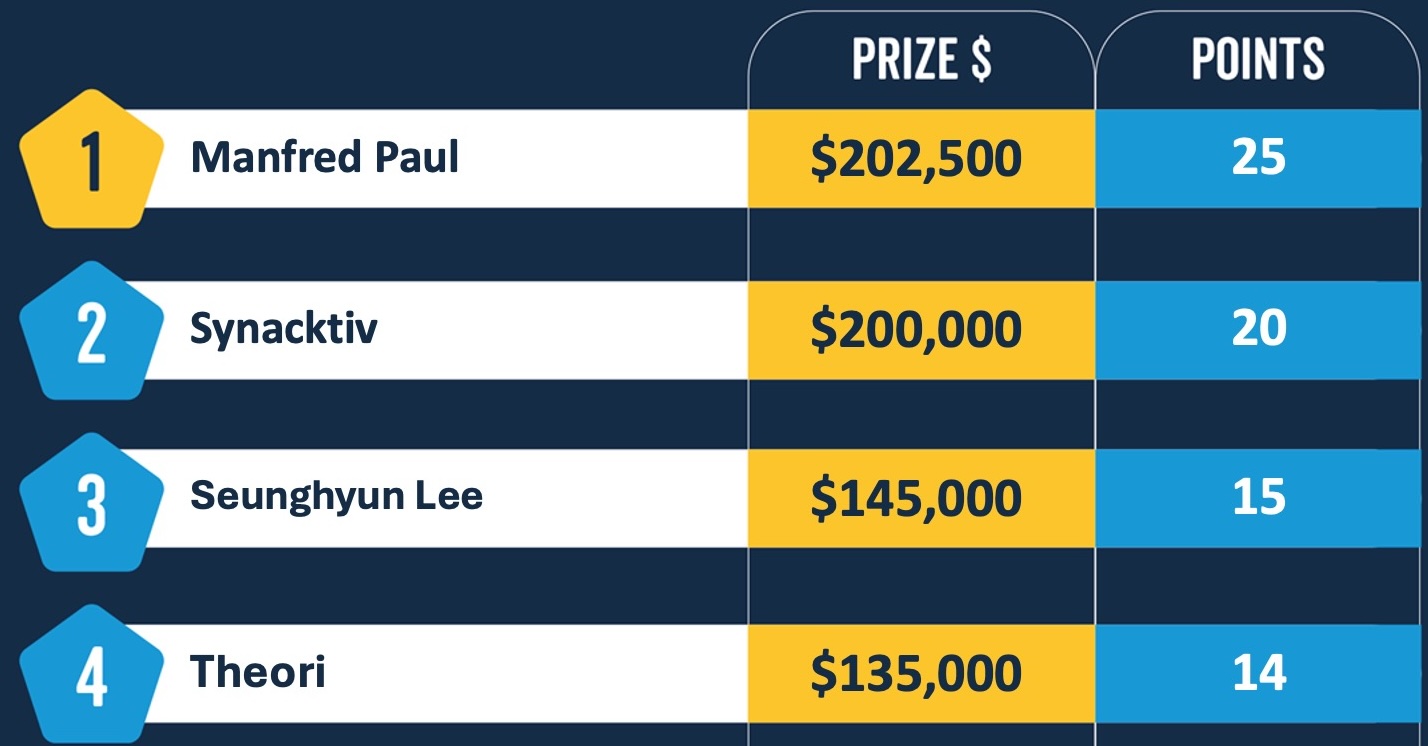 Pwn2Own Vancouver 2024 leaderboard (ZDI)
Pwn2Own Vancouver 2024 leaderboard (ZDI)
The standout performer of this year’s edition was Manfred Paul, clinching victory with 25 Master of Pwn points and a substantial $202,500 in earnings. Paul’s exploits included hacking into Apple Safari, Google Chrome, and Microsoft Edge web browsers, demonstrating a mastery of diverse attack techniques.
Among the highlights of Day 1 was Synacktiv’s remarkable achievement of securing a Tesla Model 3 and $200,000 after successfully hacking the Tesla ECU using an integer overflow exploit within a mere 30 seconds.
Trending: Major Cyber Attacks that shaped 2023
Trending: Recon Tool: SiCat


