Qlocker ransomware returns – targets QNAP NAS devices worldwide

Reading Time: 1 Minute
Threat actors behind the Qlocker ransomware are once again targeting Internet-exposed QNAP Network Attached Storage (NAS) devices worldwide.
Qlocker has previously targeted QNAP customers in a massive ransomware campaign that started during the week of April 19, moving victims’ files within password-protected 7-zip archives with the .7z extension after breaching their NAS devices.
QNAP warned that the attackers were exploiting the CVE-2021-28799 hard-coded credentials vulnerability in the HBS 3 Hybrid Backup Sync app to hack into users’ devices and lock their files.
However, for some QNAP customers targeted in last year’s Qlocker ransomware campaign, the warning came way too late after the attackers extorted hundreds of QNAP users.
In total, affected QNAP users lost roughly $350,000 within a single month after paying ransoms of 0.01 bitcoins (worth approximately $500 at the time) to get the password needed to recover their data.
Qlocker returns in new 2022 campaign
The new Qlocker ransomware campaign began on January 6 and it drops ransom notes named !!!READ_ME.txt on compromised devices.
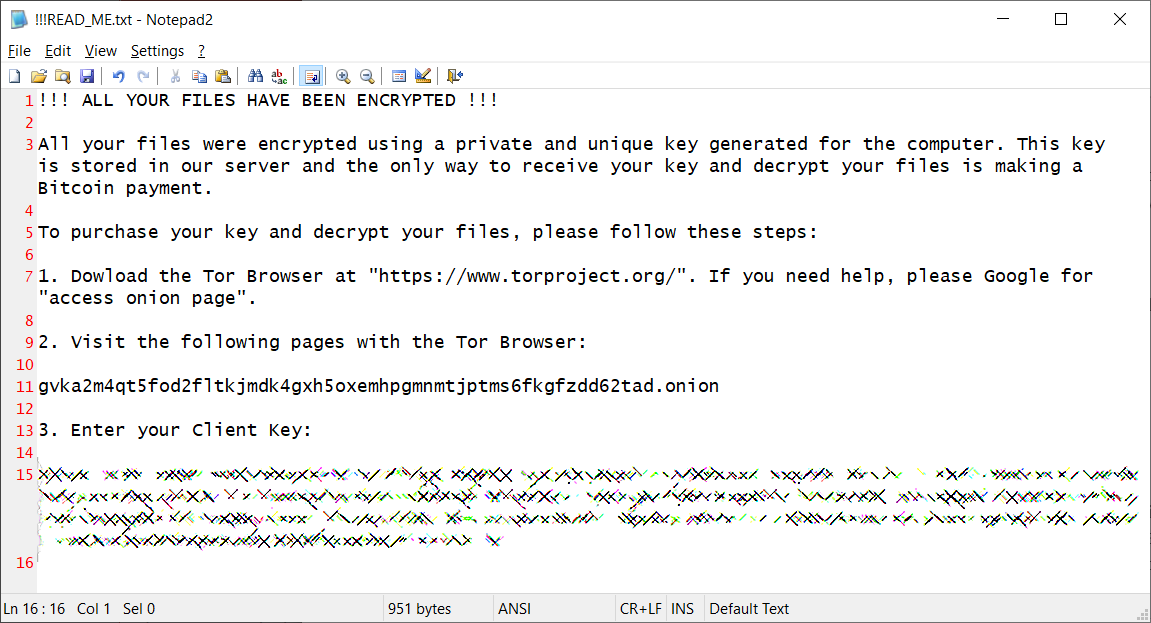
These ransom notes also include the Tor site address (gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion) the victims are prompted to visit to gain more information on how much they will have to pay to regain access to their files.
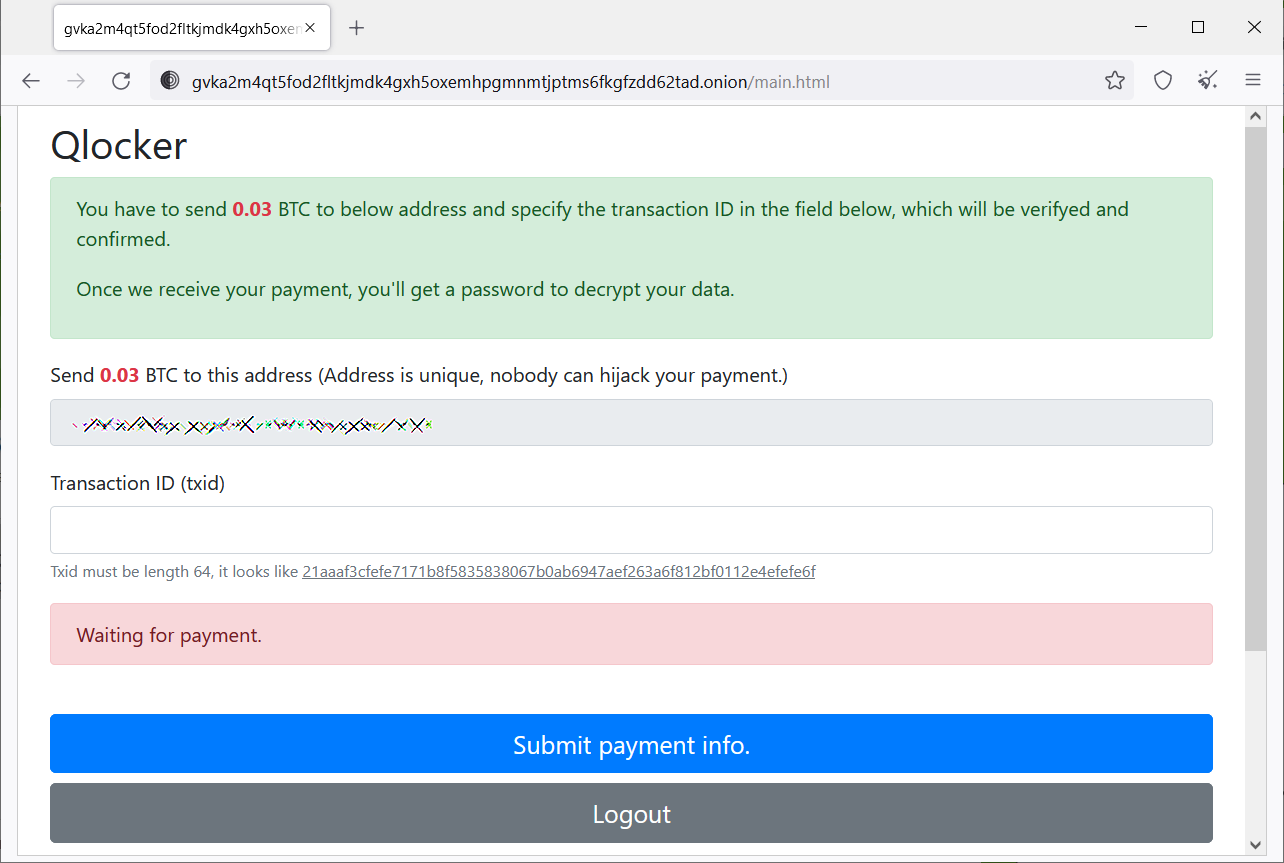
Tor victim pages seen by BleepingComputer since this new series of Qlocker attacks started display ransom demands ranging between 0.02 and 0.03 bitcoins.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
More information on what to do if the QLocker2 ransomware campaign has hit you can be found in this support topic (the topic for the 2021 Qlocker campaign can be found here).
You can also check out the old guide on how to recover data from NAS devices compromised in last year’s Qlocker ransomware attacks.
Since Qlocker returned on January 6, dozens of ransom notes and encrypted files have been submitted to the ID-Ransomware service by affected QNAP users.
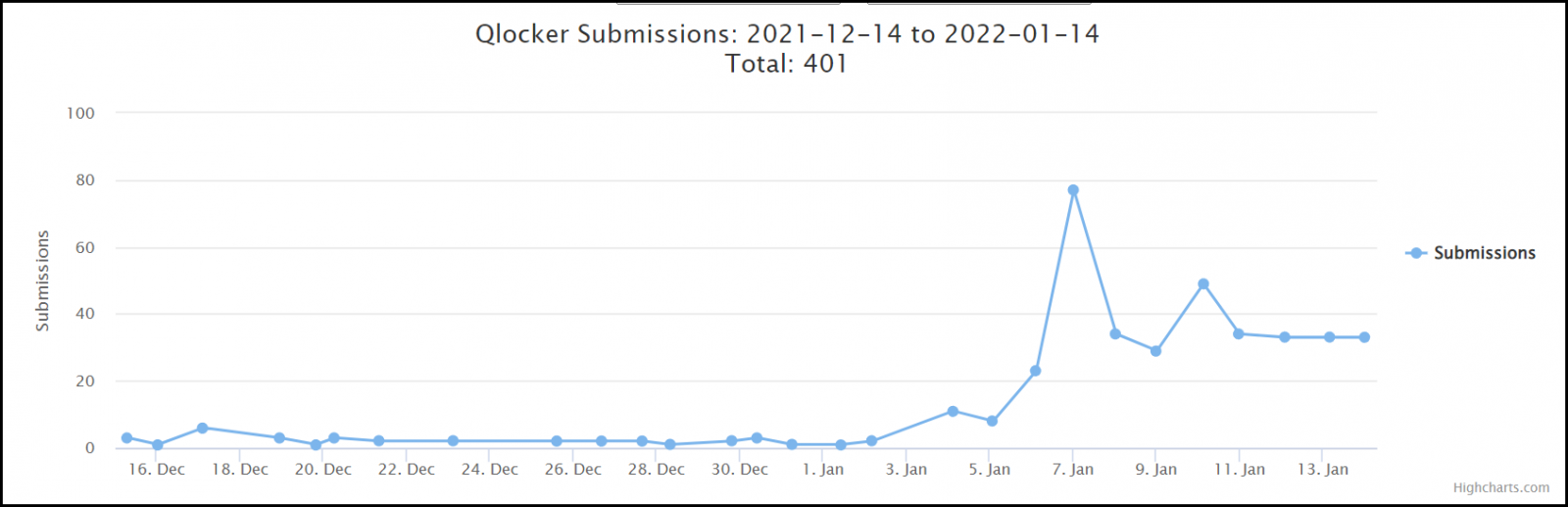
Unfortunately, Qlocker is not the only ransomware targeting QNAP NAS devices, as shown by a surge of ech0raix ransomware attacks that started right before Christmas.
See Also: Offensive Security Tool: Ivy
Earlier this month, the company also warned its customers to secure Internet-exposed NAS devices from ongoing ransomware and brute-force attacks by disabling Port Forwarding on their routers and their devices’ UPnP function.
QNAP also notified customers last year to secure their devices against incoming attacks, including Agelocker and eCh0raix ransomware campaigns.
The NAS maker recommends implementing the following best practices if you want to secure your QNAP device from further attacks.
See Also: Hacking stories – Rafael Núñez (aka RaFa), hacking NASA with the hacking group: World of Hell
Source: www.bleepingcomputer.com
(Click Link)












