Ransomware Breach at Stanford University in September Exposed the Personal Information of 27,000 Individuals

Stanford University has revealed that the personal data of 27,000 individuals was pilfered in a ransomware attack targeting its Department of Public Safety (SUDPS) network.
The attack was uncovered on September 27, with the university publicly acknowledging the incident a month later while commencing a thorough investigation into the cybersecurity breach impacting SUDPS systems.
In a recent update, Stanford clarified that the attackers managed to breach solely the Department of Public Safety’s network, without accessing other university systems.
“The investigation determined that an unauthorized individual(s) gained access to the Department of Public Safety’s network between May 12, 2023, and Sept. 27, 2023,” the university stated.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Data breach notifications submitted to Maine’s Attorney General revealed that the attackers exfiltrated documents containing personally identifiable information (PII) of the 27,000 individuals affected.
“The compromised personal information may include varying details such as date of birth, Social Security number, government ID, passport number, driver’s license number, and other data collected by the Department of Public Safety in its operations,” Stanford elaborated.
“For a select few individuals, the stolen information might also encompass biometric data, health/medical records, email addresses with passwords, usernames with passwords, security Q&A, digital signatures, and credit card data with security codes.”
While Stanford hasn’t directly attributed the September incident to a specific ransomware group, the Akira ransomware gang claimed responsibility in October, asserting to have absconded with 430GB of files from the university’s systems.
The cybercriminals have subsequently released the pilfered data on their dark web leak site, enabling access via BitTorrent downloads.
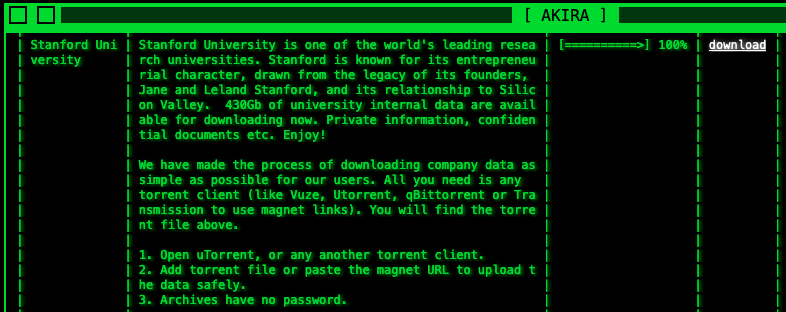 Akira Stanford data leak (BleepingComputer)
Akira Stanford data leak (BleepingComputer)
Trending: Offensive Security Tool: SmuggleFuzz


