Red-Team Tool “EDRSilencer” Used in Attacks to Bypass Security Alerts

A newly surfaced red-team tool known as EDRSilencer has been observed in real-world cyberattacks, where threat actors are using it to identify and neutralize security tools on compromised systems. Originally designed for penetration testing and red-team operations, EDRSilencer has now been repurposed by attackers to mute alerts generated by Endpoint Detection and Response (EDR) tools, significantly enhancing their ability to carry out undetected attacks.
EDR Tools: The Target of Advanced Evasion Techniques
EDR tools play a critical role in defending against cyber threats by continuously monitoring endpoints for suspicious activity, automatically blocking threats, and sending detailed reports to a central management server. These reports contain valuable insights into the origin, behavior, and spread of cyber threats within an organization.
EDRSilencer disrupts this process by detecting running EDR processes and using the Windows Filtering Platform (WFP) to filter, block, or modify the network traffic between the EDR agents and their management consoles. By cutting off this communication, attackers can prevent alerts from being sent to security teams, effectively blinding defenders to the malicious activity happening on the compromised system.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
How EDRSilencer Works
The latest version of EDRSilencer detects and blocks up to 16 modern EDR tools, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
The tool works by setting persistent filters in WFP, which is commonly used by security products like firewalls and antivirus solutions. These custom rules allow attackers to intercept and block the network traffic that would otherwise alert the EDR management server to suspicious activities.
.jpg) Blocking the traffic of hardcoded executables
Blocking the traffic of hardcoded executables
Source: Trend Micro
By blocking telemetry data and security alerts, EDRSilencer enables attackers to conduct unauthorized activities—such as deploying malware, escalating privileges, or exfiltrating data—without raising alarms. This capability makes it a powerful tool in advanced persistent threat (APT) campaigns and financially motivated cyberattacks.
Customizing EDRSilencer for Specific Attacks
In addition to its hardcoded list of 16 EDR tools, EDRSilencer allows attackers to customize its behavior by adding filters for specific processes or EDR components. By providing the file paths of additional security tools, attackers can expand the list of targets beyond those included by default. This customization ensures that even partially blocked EDR solutions can be fully neutralized in targeted attacks.
Trend Micro‘s testing has shown that, when used in this way, EDRSilencer can effectively stop security tools from sending logs or alerts, confirming its ability to bypass detection in even the most secure environments.
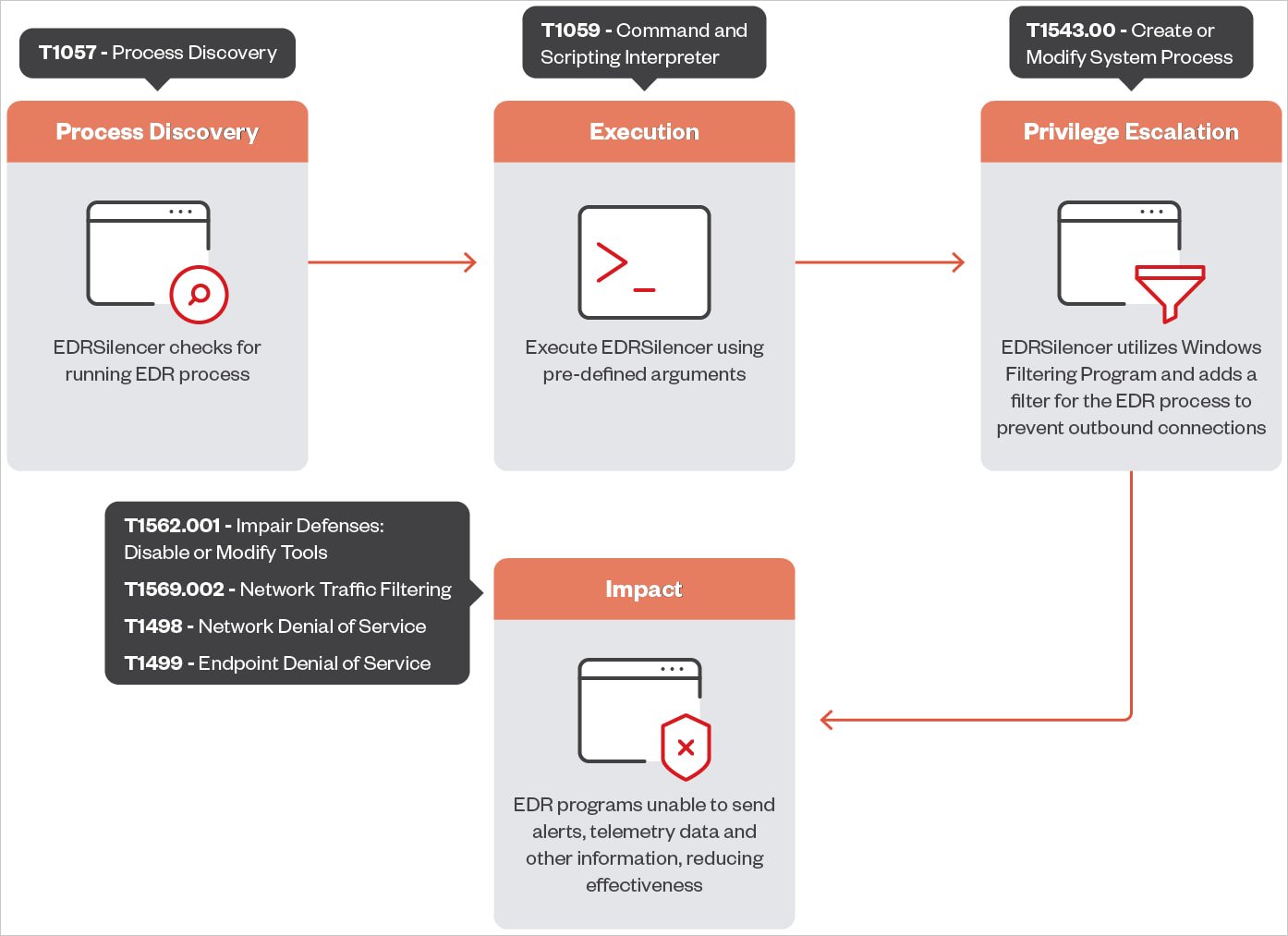 EDRSilencer attack chain
EDRSilencer attack chain
Source: Trend Micro
Trending: OSINT Tool: cloud_enum
Implications for Cyber Defenders
The use of EDRSilencer in real-world attacks poses a significant challenge for security teams. Without alerts or telemetry reports, defenders may be unaware that their systems have been compromised, allowing attackers to remain hidden for extended periods. This increases the likelihood of successful attacks, as threat actors can freely deploy ransomware, conduct data exfiltration, or engage in lateral movement within the network.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













