Reptile: Open-Source Rootkit Targets Linux Systems in South Korea

A sophisticated cyber threat has emerged, targeting Linux systems in South Korea through the use of an open-source rootkit known as Reptile. In a recent report, the AhnLab Security Emergency Response Center (ASEC) shed light on this alarming development, highlighting that Reptile differentiates itself from conventional rootkit malware by offering a reverse shell functionality, allowing malicious actors to effortlessly assume control over compromised systems.
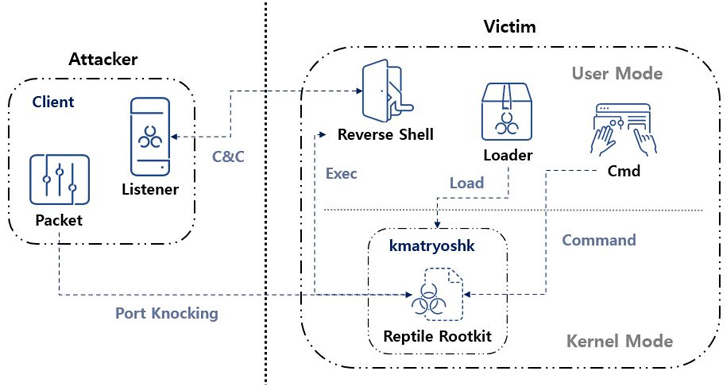
The rootkit employs a technique called “port knocking,” wherein the malware opens a specific port on an infected system and awaits activation. Upon receiving a distinct “magic packet” from the threat actor, a connection with a command and control (C&C) server is established, granting the attacker unfettered control over the compromised system’s operations.
A rootkit is a type of malicious software designed to clandestinely provide unauthorized access to a computer system at a privileged level while evading detection. Reptile has been linked to at least four distinct campaigns since 2022, indicating its growing prevalence in cyber attacks.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
This new breed of rootkit first surfaced in May 2022 when Trend Micro uncovered its use in connection with an intrusion set named Earth Berberoka. It was subsequently deployed to conceal connections and processes related to a cross-platform Python trojan called Pupy RAT, which was used in attacks targeting gambling sites in China.
In March 2023, Mandiant, a subsidiary of Google, revealed that a suspected China-linked threat actor named UNC3886 leveraged Reptile in a series of attacks that exploited zero-day vulnerabilities in Fortinet appliances. Moreover, Chinese hacking groups have utilized a Linux malware named Mélofée, based on Reptile, to further their activities.
The rootkit’s inner workings have been meticulously analyzed, exposing its use of a loader known as kmatryoshka. This loader decrypts and loads the rootkit’s kernel module into memory, followed by the opening of a designated port. The attacker then transmits a magic packet over various protocols like TCP, UDP, or ICMP. Upon receipt, a reverse shell connection is established with the C&C server.
Trending: Recon Tool: RecoX
The alarming aspect of this tactic is that it leverages “magic packets,” a technique previously associated with another rootkit named Syslogk, as documented by Avast in the past.
South Korean cybersecurity firm ASEC has also noted an attack case involving Reptile, demonstrating its real-world impact. The firm emphasizes that while Reptile indeed provides a concealment feature for files, directories, processes, and network communications, it also introduces a critical vulnerability by offering a reverse shell, potentially allowing malicious actors to compromise systems.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com