Researchers Unearth Security Flaws in TP-Link Smart Bulb and App, Warning of WiFi Password Exposure

Researchers hailing from Italy and the UK have uncovered a set of four vulnerabilities in TP-Link’s Tapo L530E smart bulb and the associated Tapo app, potentially providing attackers with the means to pilfer victims’ WiFi passwords.
 The Tapo L530E (TP-Link)
The Tapo L530E (TP-Link)
The TP-Link Tapo L530E smart bulb is a widely popular product, available on numerous platforms, including Amazon. The Tapo app, on the other hand, boasts over 10 million installations on Google Play, making it a prevalent choice for managing smart devices.
Experts from the Universita di Catania and the University of London opted to examine this product due to its popularity. However, their primary objective in publishing their findings is to draw attention to security risks present in the vast array of smart Internet of Things (IoT) devices that consumers use. Many of these devices exhibit risky data transmission practices and lack sufficient authentication safeguards.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Outlined Vulnerabilities:
- Improper Authentication: The first vulnerability centers on improper authentication within the Tapo L503E, allowing attackers to mimic the device during the session key exchange process. This high-severity vulnerability (CVSS v3.1 score: 8.8) permits nearby attackers to obtain Tapo user passwords and manipulate Tapo devices.
- Hard-Coded Checksum Shared Secret: Another high-severity flaw (CVSS v3.1 score: 7.6) results from a hard-coded short checksum shared secret. Attackers can acquire this secret through brute-forcing or by decompiling the Tapo app.
- Predictable Symmetric Encryption: A medium-severity vulnerability pertains to a lack of randomness in symmetric encryption, rendering the cryptographic scheme predictable.
- Message Freshness Checks Absence: The fourth issue arises due to the absence of checks for the freshness of received messages, allowing session keys to remain valid for 24 hours. This permits attackers to replay messages within this timeframe.
Attack Scenarios:
The most concerning attack scenario involves bulb impersonation and subsequent theft of Tapo user account information by exploiting vulnerabilities 1 and 2. Subsequently, by gaining access to the Tapo app, attackers can extract the victim’s WiFi SSID and password, enabling access to all devices linked to the same network.
The target device must be in setup mode for this attack to succeed. However, attackers can deauthenticate the bulb, forcing the user to perform the setup process again to restore its functionality.
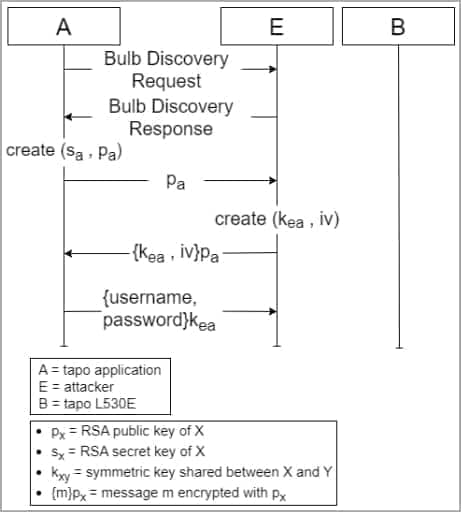 Bulb impersonation diagram (arxiv.org)
Bulb impersonation diagram (arxiv.org)
Researchers also explored the possibility of Man-In-The-Middle (MITM) attacks with a configured Tapo L530E device. By leveraging vulnerability 1, attackers can intercept and manipulate communication between the app and the bulb, capturing RSA encryption keys used for subsequent data exchange.
MITM attacks are also feasible with unconfigured Tapo devices using vulnerability 1, wherein attackers bridge two networks during setup, facilitating the retrieval of Tapo passwords, SSIDs, and WiFi passwords in easily decipherable base64 encoded form.
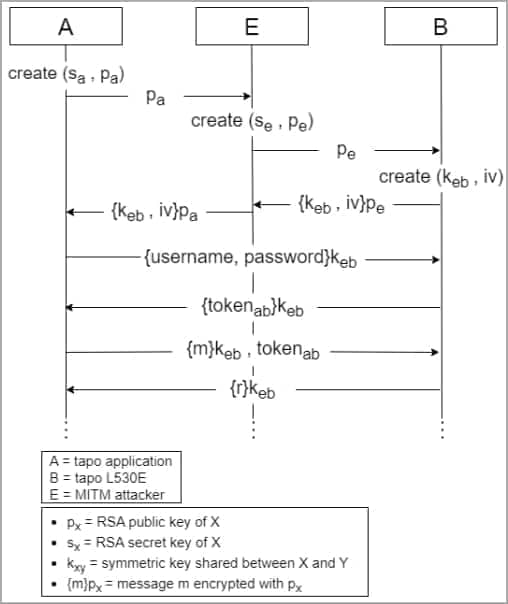 MITM attack diagram (arxiv.org)
MITM attack diagram (arxiv.org)
Lastly, vulnerability 4 permits replay attacks, allowing attackers to replicate previously sniffed messages to effect functional changes in the device.
Trending: Recon Tool: RecoX
Disclosure and Remediation:
The research team responsibly shared their findings with TP-Link, and the company acknowledged the vulnerabilities. TP-Link committed to implementing fixes for both the app and the bulb’s firmware in the near future.
The paper, however, does not provide specific details about the availability of these fixes or the versions that remain susceptible to attacks.
As a general rule for IoT security, experts recommend isolating such devices from critical networks, keeping firmware and app versions up to date, and securing accounts with strong passwords and multi-factor authentication (MFA).
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












