Rising Threat: Rhysida Ransomware Sets Sights on Healthcare Sector

The Rhysida ransomware operation has garnered significant attention following a series of attacks on healthcare institutions, prompting government agencies and cybersecurity firms to closely monitor its activities. Acknowledging the growing threat, the U.S. Department of Health and Human Services (HHS) issued a security bulletin, with CheckPoint, Cisco Talos, and Trend Micro subsequently publishing reports that delve into different aspects of the threat actor’s operations.
Rhysida first came into the spotlight in June when it leaked documents stolen from the Chilean Army (Ejército de Chile) on its data leak site. A preliminary analysis by SentinelOne at the time indicated that the ransomware was still in early development, lacking certain standard features typically seen in ransomware strains, such as persistence mechanisms, Volume Shadow Copy wiping, and process termination.
The Rhysida ransom note reads, “This is an automated alert from cybersecurity team Rhysida. An unfortunate situation has arisen – your digital ecosystem has been compromised, and a substantial amount of confidential data has been exfiltrated from your network.”
 Rhysida ransom note
Rhysida ransom note
Source: BleepingComputer
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Unlike some ransomware operations that disavow targeting healthcare organizations, Rhysida appears to differ. Its dark web data leak site specifically mentions a healthcare organization in Australia, giving them a week to pay the ransom before leaked data becomes public.
 Rhysida dark web data leak site
Rhysida dark web data leak site
Source: BleepingComputer
The U.S. Department of Health and Human Services (HHS) bulletin highlighted that Rhysida’s activities have expanded to a concerning level. While the ransomware’s mechanisms are still relatively basic, its focus has shifted towards the healthcare and public sectors. The bulletin stated that victims span Western Europe, North and South America, and Australia, with sectors such as education, government, manufacturing, technology, and managed service providers being targeted. However, recent attacks have extended to the Healthcare and Public Health (HPH) sector.
Reports have linked Rhysida to a cyberattack on Prospect Medical Holdings (PMH), which has suffered a system-wide outage impacting numerous medical facilities across the United States. Although Rhysida has not claimed responsibility for the attack, PMH has not officially commented on the ransomware gang’s involvement.
According to a Trend Micro report, Rhysida employs a common attack chain, leveraging phishing emails for initial access, followed by the deployment of Cobalt Strike and PowerShell scripts, ultimately leading to the deployment of the locker. Notably, the researchers observed that Rhysida’s operators actively develop the locker, demonstrated by the use of external scripts for tasks typically handled by the ransomware encryptor itself.
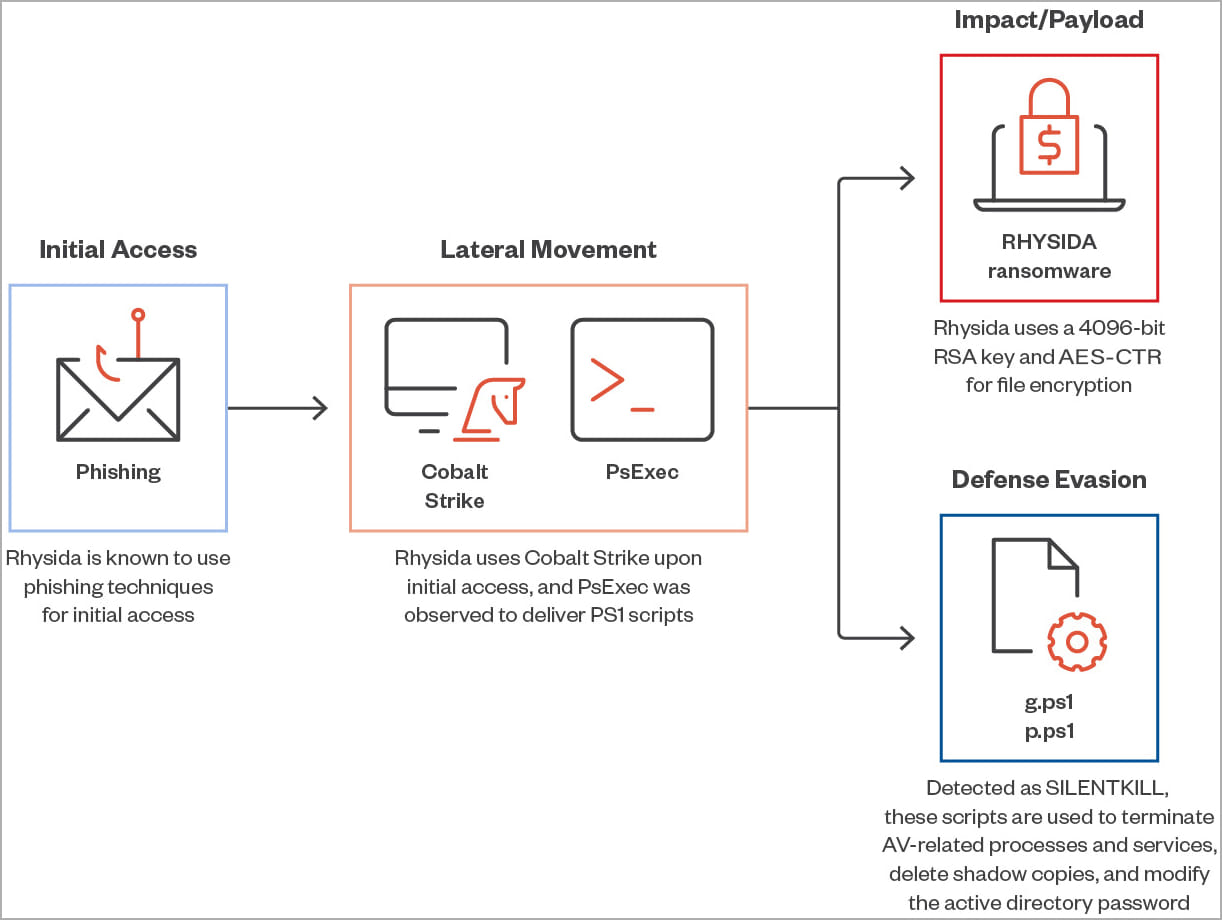 Rhysida’s latest attack chain (Trend Micro)
Rhysida’s latest attack chain (Trend Micro)
Trending: Recon Tool: RecoX
Cisco Talos confirmed that the latest iteration of Rhysida employs a 4096-bit RSA key with the ChaCha20 algorithm for file encryption. The ransomware now excludes specific directories and the following file types from encryption:
.bat .bin .cab .cmd .com .cur .diagcab .diagcfg, .diagpkg .drv .dll .exe .hlp .hta .ico .lnk .msi .ocx .ps1 .psm1 .scr .sys .ini thumbs .db .url .iso and .cab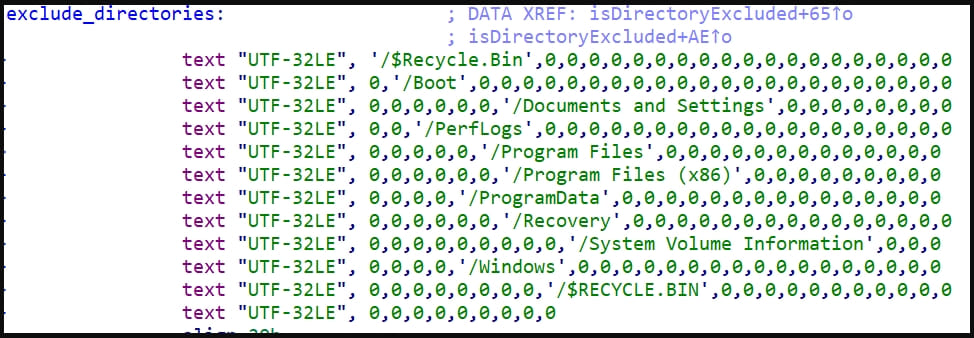
Source: Cisco
In a comprehensive analysis, CheckPoint even identified connections between Rhysida and the defunct Vice Society ransomware operation, based on victim publishing times and targeting patterns.
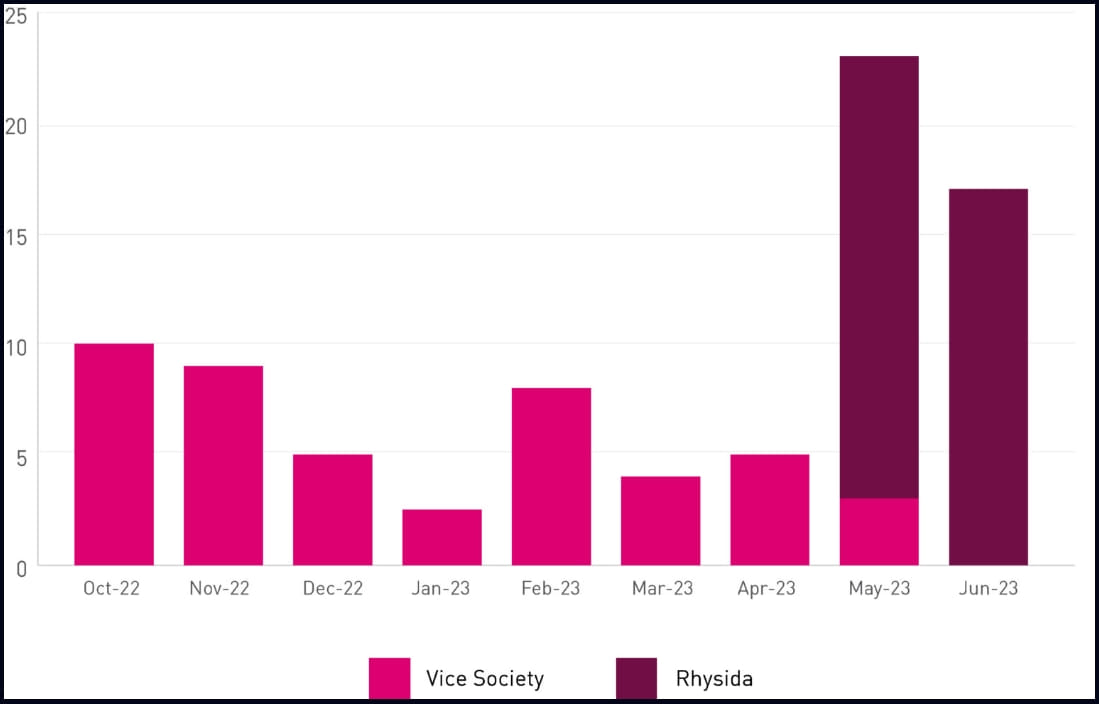 Comparison of activity change in Vice Society and Rhysida (CheckPoint)
Comparison of activity change in Vice Society and Rhysida (CheckPoint)
In conclusion, Rhysida has rapidly established itself in the ransomware landscape, particularly focusing on healthcare institutions. While its technical aspects initially lagged behind, the group’s operations are catching up, and the threat to various sectors, especially healthcare, remains concerning.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












