Rocke Group’s Malware Now Has Worm Capabilities

Reading Time: 1 Minute
The Pro-Ocean cryptojacking malware now comes with the ability to spread like a worm, as well as harboring new detection-evasion tactics.
Researchers have identified an updated malware variant used by the cybercrime gang Rocke Group that targets cloud infrastructures with crypto-jacking attacks.
The malware is called Pro-Ocean, which was first discovered in 2019, and has now been beefed-up with “worm” capabilities and rootkit detection-evasion features.
“This malware is an example that demonstrates that cloud providers’ agent-based security solutions may not be enough to prevent evasive malware targeted at public cloud infrastructure,” said Aviv Sasson with Palo Alto Networks on Thursday. “As we saw, this sample has the capability to delete some cloud providers’ agents and evade their detection.”
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
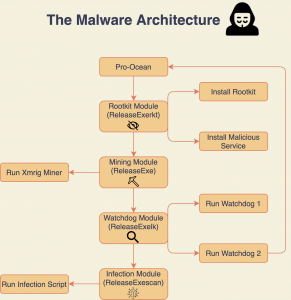
Pro-Ocean Malware
Pro-Ocean uses a variety of known vulnerabilities to target cloud applications. These include a critical flaw in Apache ActiveMQ (CVE-2016-3088) and a high-severity vulnerability in Oracle WebLogic (CVE-2017-10271). The malware has also been spotted targeting unsecure instances of Redis.
Once downloaded, the malware attempts to remove other malware and cryptominers, including Luoxk, BillGates, XMRig and Hashfish. It then kills any processes using the CPU heavily, so that its XMRig miner can utilize 100 percent of the CPU juice needed to sow Monero.
The malware is made up of four components: A rootkit module that installs a rootkit and other various malicious services; a mining module that runs the XMRig miner; a Watchdog module that executes two Bash scripts (these check that the malware is running and search any processes using CPU heavily); and an infection module that contains “worm” capabilities.
See Also: Offensive Security Tool: Shad0w
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
New Features
The latter “worm” feature is a new add for Pro-Ocean, which previously only infected victims manually. The malware now uses a Python infection script to retrieve the public IP address of the victim’s machine. It does so by accessing an online service with the address “ident.me,” which scopes out IP addresses for various web servers. Then, the script tries to infect all the machines in the same 16-bit subnet (e.g. 10.0.X.X).
“It does this by blindly executing public exploits one after the other in the hope of finding unpatched software it can exploit,” said Sasson.
Other threat groups have previously adopted worm-like functionality into their Monero-chugging malware. TeamTNT’s cryptomining worm, for instance, was found spreading through the Amazon Web Services (AWS) cloud and collecting credentials in August.
The Pro-Ocean malware has also added mew rootkit capabilities that cloak its malicious activity.
These updated features exist in Libprocesshider, a library for hiding processes used by the malware. This library was utilized by previous versions of Pro-Ocean – however, in the new version, the developer of the code has added several new code snippets to the library for further functionalities.
For example, before calling the libc function open (libc is a library of standard functions that can be used by all C programs), a malicious function determines whether the file needs to be hidden to obfuscate malicious activities.
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
“If it determines that the file needs to be hidden, the malicious function will return a ‘No such file or directory’ error, as if the file in question does not exist,” said Sasson.
Researchers said they believe that the Rocke Group will continue to actively update its malware, particularly as the cloud grows as a lucrative target for attackers.
“Cryptojacking malware targeting the cloud is evolving as attackers understand the potential of that environment to mine for crypto coins. We previously saw simpler attacks by the Rocke Group, but it seems this group presents an ongoing, growing threat. This cloud-targeted malware is not something ordinary since it has worm and rootkit capabilities. We can assume that the growing trend of sophisticated attacks on the cloud will continue.”
style=”display:block” data-ad-client=”ca-pub-6620833063853657″ data-ad-slot=”8337846400″ data-ad-format=”auto” data-full-width-responsive=”true”>
Source: www.threatpost.com
(Click Link)