Russian APT29 use WinRAR Vulnerability and Ngrok in Recent Embassy Cyberattacks
The state-sponsored Russian hacker group APT29, also known as Cozy Bear, has strategically exploited the CVE-2023-38831 vulnerability in WinRAR. Following in the footsteps of Sandworm and APT28, APT29, infamous for its various aliases, including NobleBaron and SolarStorm, has orchestrated targeted attacks on embassy entities, cleverly using a BMW car sale lure. The CVE-2023-38831 flaw, affecting WinRAR versions prior to 6.23, permits the creation of archives executing background code for malicious purposes. This zero-day vulnerability has been actively exploited since April, primarily targeting cryptocurrency and stock trading forums.
According to a report by the Ukrainian National Security and Defense Council (NDSC), APT29’s latest campaign involves a malicious ZIP archive masquerading as a PDF titled “DIPLOMATIC-CAR-FOR-SALE-BMW.pdf.” This lure has been strategically deployed across multiple European countries, including Azerbaijan, Greece, Romania, and Italy. APT29’s intricate tactics include running a script in the background, displaying the PDF lure, and initiating the download of PowerShell code that executes a payload.
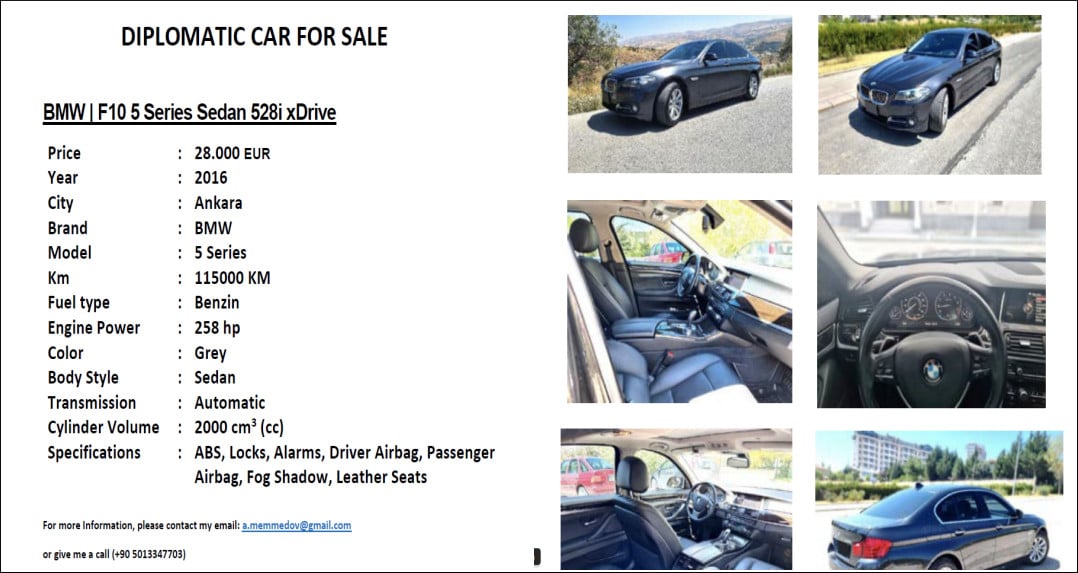 Russian APT29 hackers use WinRAR bug in BMW car ad for diplomats
Russian APT29 hackers use WinRAR bug in BMW car ad for diplomats
source: Ukrainian National Security and Defense Council
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
What makes this campaign stand out is the fusion of old and new techniques. APT29 has resurrected its BMW car ad phishing lure, previously seen in a May campaign targeting diplomats in Ukraine, combining it with a sophisticated method to communicate with a malicious server. Notably, the Russian hackers utilized Ngrok’s free static domain feature to access the command and control (C2) server hosted on their Ngrok instance, providing discrete rendezvous points for their malicious payloads. This technique enhances their ability to remain undetected while communicating with compromised systems.
This cyber onslaught, as observed by the Ukrainian agency, marks a significant evolution in APT29’s playbook. The WinRAR vulnerability, flagged by cybersecurity experts as a zero-day risk, has become a preferred tool for advanced threat actors.
Trending: Recon Tool: subby
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com



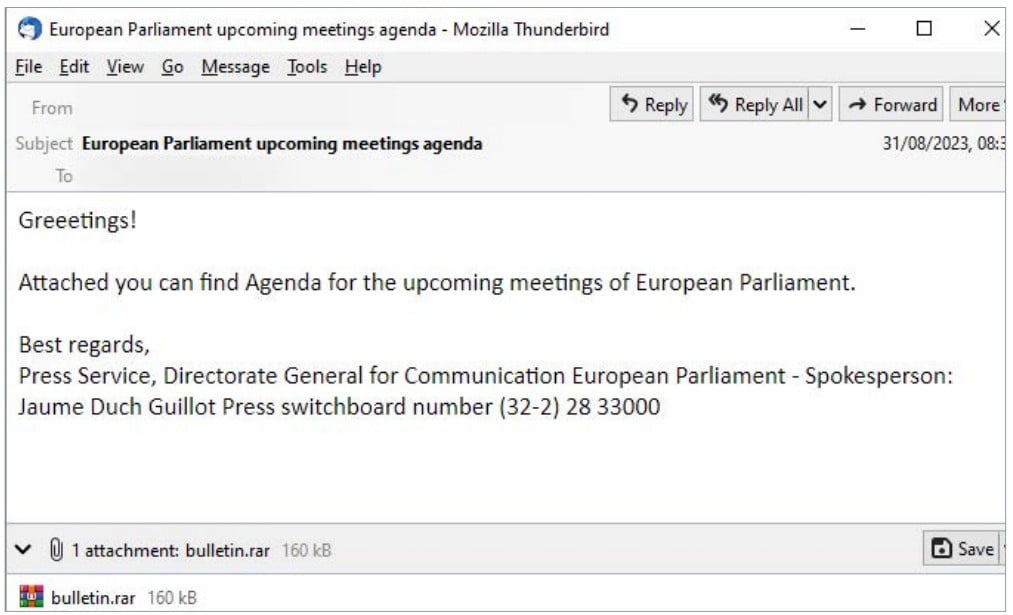 Lure from Russian APT28 hackers with WinRAR exploit to target political entities
Lure from Russian APT28 hackers with WinRAR exploit to target political entities









