Russian Cyber Onslaught: Unraveling the Largest-Ever Attack on Denmark’s Critical Infrastructure

Russian threat actors are potentially tied to what Danish authorities are labeling the “largest cyber attack against Danish critical infrastructure.” This sophisticated assault, which unfolded in May 2023, targeted 22 companies integral to the operation of Denmark’s energy sector.
SektorCERT, Denmark’s cybersecurity agency, revealed that these cyberattacks were anything but ordinary, emphasizing that the assailants displayed an uncanny precision, hitting all their targets with unerring accuracy.
The agency discovered compelling evidence linking one or more of these attacks to Russia’s GRU military intelligence agency, also known as Sandworm, a notorious entity with a history of orchestrating disruptive cyber assaults, especially on industrial control systems.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The meticulously coordinated cyber onslaught occurred on May 11, leveraging CVE-2023-28771, a critical command injection flaw affecting Zyxel firewalls, disclosed just a month prior. The attacks aimed at 11 companies successfully infiltrated these systems, executing malicious code to meticulously survey firewall configurations and plan subsequent actions.
SektorCERT’s detailed timeline of events highlighted the rarity and effectiveness of such coordination, emphasizing that simultaneous attacks leave no room for information sharing and warnings. A second wave of attacks occurred from May 22 to 25, introducing previously unseen cyber weapons, raising questions about the involvement of multiple threat actors.
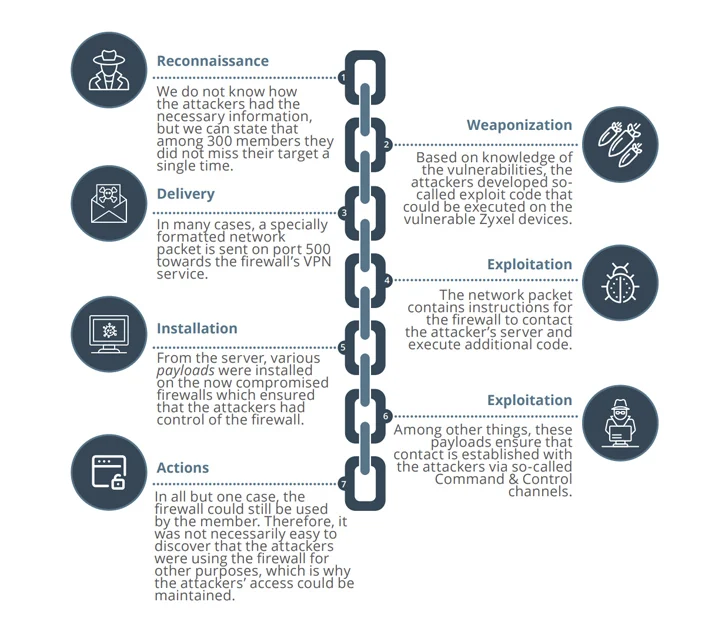
The attackers potentially exploited two additional critical vulnerabilities in Zyxel gear (CVE-2023-33009 and CVE-2023-33010) as zero-days, turning the firewalls into Mirai and MooBot botnets. The compromised devices, in some instances, were then utilized for distributed denial-of-service (DDoS) attacks against unspecified companies in the U.S. and Hong Kong.
Trending: Jeff Foley – OWASP Amass Founder
Trending: Offensive Security Tool: Ghauri
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













