Russian State Alleges Apple’s Involvement in iPhone iOS Zero-Click Attacks

Kaspersky Reveals Ongoing iPhone Hacking Campaign Exploiting iMessage Vulnerabilities
Russian cybersecurity firm Kaspersky has made a startling revelation regarding a persistent iPhone hacking campaign that exploits vulnerabilities in iMessage. The attack, involving zero-click exploits, enables hackers to install malware on iPhones without any user interaction.
The malicious message delivery takes advantage of a vulnerability that allows code execution, leading to the download of additional malware from the attackers’ server. While the message and attachment are subsequently wiped from the device, the malicious payload remains, running with root privileges. This grants the attackers access to system and user information, as well as the ability to execute commands.
Dubbed “Operation Triangulation” by Kaspersky, the campaign began in 2019 and is still ongoing. The cybersecurity firm is urging anyone with information about the campaign to come forward and share it.
Malware Analysis
To analyze the malware, Kaspersky used the Mobile Verification Toolkit to create filesystem backups of the infected iPhones. Despite the malware’s attempts to erase traces of the attack, signs of infection such as system file modifications, abnormal data usage, and the injection of deprecated libraries were discovered.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Kaspersky’s analysis indicates that the earliest signs of infection occurred in 2019, and the most recent version of iOS affected by the malicious toolset is 15.7. However, it should be noted that the latest major iOS release, version 16.5, may have already addressed the vulnerability exploited by the malware.
 Malicious encrypted attachment (Kaspersky)
Malicious encrypted attachment (Kaspersky)
The exploit, delivered via iMessage, triggers an unknown vulnerability in iOS, allowing for code execution and the fetching of subsequent stages from the attackers’ server. This includes privilege escalation exploits.
Kaspersky has shared a list of 15 domains associated with this malicious activity, enabling security administrators to check historical DNS logs for any potential signs of exploitation on their devices.
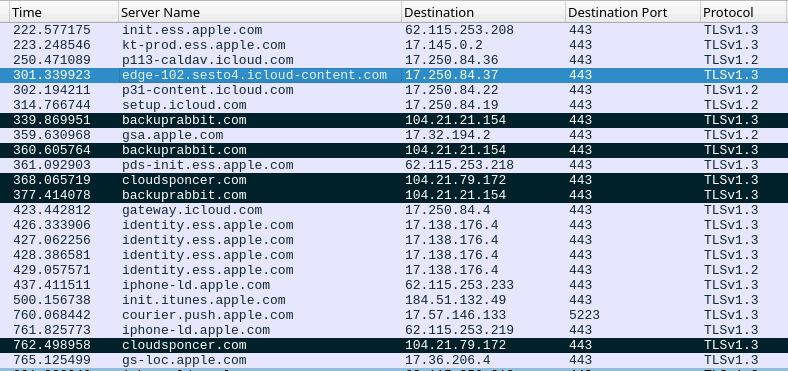 Network exploitation sequence (Kaspersky)
Network exploitation sequence (Kaspersky)
Once the malware achieves root privilege escalation, it downloads a fully-featured toolset that executes commands to gather system and user information. Additionally, it can download additional modules from the command and control (C2) server.
Notably, the APT toolset dropped on the device lacks persistence mechanisms, meaning a simple reboot would effectively halt its operations.
While Kaspersky has shared some details about the malware’s functions, the analysis of the final payload is still underway, limiting the available information.
Russia accusations
In a coinciding statement, Russia’s FSB intelligence and security agency accused Apple of deliberately providing the NSA with a backdoor that enables the infection of iPhones in Russia with spyware. The FSB alleges that thousands of iPhones belonging to officials within the Russian government and staff from various embassies have been infected with malware.
Trending: Recon Tool: Sniffer
Despite the seriousness of the allegations, the FSB has yet to provide any concrete evidence to support its claims. Previously, the Russian state had recommended its employees to switch away from using Apple iPhones and, if possible, avoid American-made technology altogether.
Kaspersky confirmed that its headquarters office in Moscow and employees in other countries were affected by the attack. However, the company stated that it cannot verify a direct link between its findings and the FSB’s report, as it lacks the technical details of the government’s investigation.
Apple responded to the allegations, categorically denying any collaboration with governments to insert backdoors into their products. The company stated that it has never engaged in such activities and has no intention of doing so in the future.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












