S1deload Stealer: The New Malware Threat Targeting Social Media Accounts

Reading Time: 3 Minutes
Bitdefender Discovers New Malware Targeting YouTube and Facebook Users
Security researchers with Bitdefender’s Advanced Threat Control (ATC) team have identified a new malware campaign that is targeting YouTube and Facebook users. Dubbed S1deload Stealer, the malware infects victims’ computers by tricking them into downloading executable files from adult-themed archives on social media platforms. Once installed, the malware can be controlled remotely to perform a variety of malicious tasks, including stealing saved credentials and cookies from the victim’s browser, mining for cryptocurrency, and artificially boosting view counts on YouTube and Facebook.
The Stealthy Nature of S1deload Stealer
The name S1deload Stealer is derived from the malware’s extensive use of DLL sideloading, which allows it to evade detection by security software. According to Bitdefender researcher Dávid Ács, the company’s products detected more than 600 unique users infected with the malware between July and December 2022. Victims are lured into downloading the malware through social engineering techniques and comments on Facebook pages that push adult-themed archives. If the user downloads one of these archives, they will instead receive an executable file containing the malware.
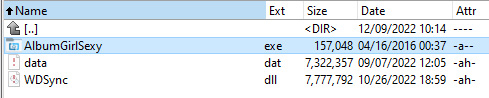 S1deload Stealer lure archive contents (Bitdefender)
S1deload Stealer lure archive contents (Bitdefender)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The Malware’s Capabilities
Once installed on a victim’s device, S1deload Stealer can be instructed by its operators to perform a range of tasks, including downloading and running additional components, deploying a stealer that exfiltrates saved credentials and cookies, or deploying a cryptojacker to mine BEAM cryptocurrency. If the malware manages to steal a Facebook account, it will attempt to estimate the account’s value by leveraging the Facebook Graph API. The malware author can then use the stolen credentials to spam on social media and infect more machines.
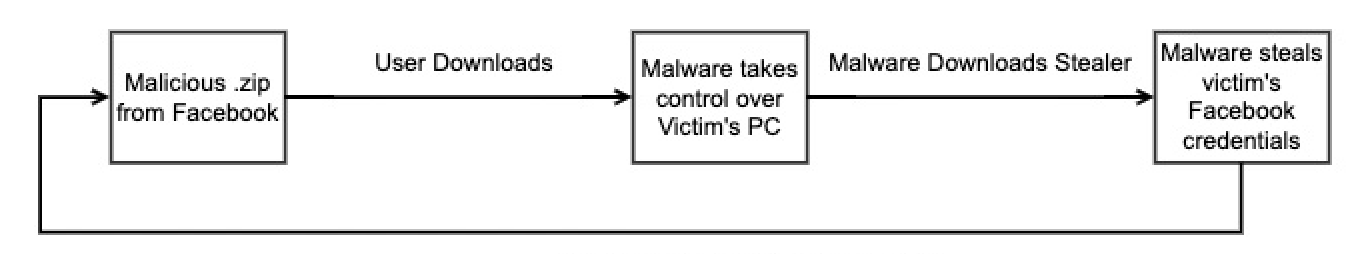 S1deload Stealer’s Facebook propagation (Bitdefender)
S1deload Stealer’s Facebook propagation (Bitdefender)
Protecting Yourself from S1deload Stealer
To avoid becoming a victim of S1deload Stealer, it is crucial never to run executables from unknown sources and keep anti-malware software up to date. Indicators of compromise (IOCs) and YARA rules linked to this malware campaign are available at the end of Bitdefender’s whitepaper (PDF).
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: TerminatorZ
The Rise of Information Stealer Malwares
Threat intelligence company SEKOIA has also identified a new information stealer strain known as Stealc, which is advertised on the dark web and hacking forums as featuring an easy-to-use administration panel and extensive data-stealing capabilities. Unlike S1deload Stealer, the Stealc malware is distributed via fake cracked software, a popular tactic also used to push other info stealers such as Vidar, Redline, Raccoon, and Mars. As the threat of malware campaigns targeting social media users continues to rise, it is more important than ever to remain vigilant and take the necessary precautions to protect yourself online.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












