Security Weaknesses in OAuth Put Grammarly, Vidio, and Bukalapak User Accounts in Jeopardy

In recent findings, critical security vulnerabilities have been disclosed within the OAuth implementations of well-known online services, including Grammarly, Vidio, and Bukalapak. These discoveries build upon earlier shortcomings identified in Booking.com and Expo. While the respective companies have since addressed these issues following responsible disclosure between February and April 2023, the vulnerabilities had the potential to allow malicious actors to obtain access tokens and potentially hijack user accounts.
OAuth, a standard often used to facilitate cross-application access, provides websites or applications with access to user data on other platforms (such as Facebook) without exposing user passwords. When OAuth is used for service authentication, any security breach in its implementation can lead to identity theft, financial fraud, and unauthorized access to personal information, including credit card details, private messages, and health records.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The problem discovered in Vidio’s OAuth implementation lies in the absence of token verification. This flaw allowed an attacker to use an access token generated for another App ID (a unique identifier created by Facebook for each registered application or website) in an attack scenario. By creating a rogue website offering Facebook sign-in, the attacker could collect access tokens and use them against Vidio.com. This would enable a full takeover of user accounts.
A similar issue related to token verification was found in Bukalapak.com’s Facebook login, potentially resulting in unauthorized access to user accounts.
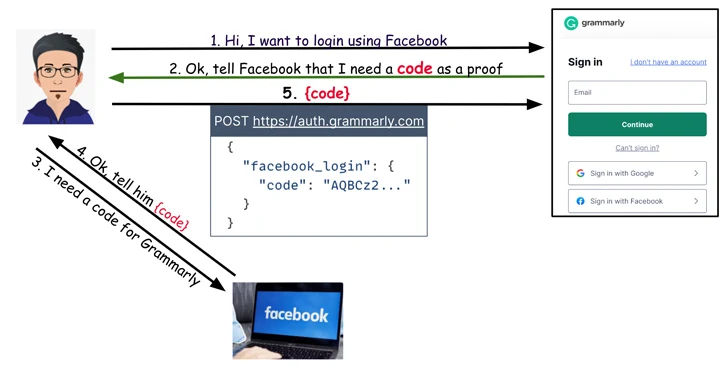
Grammarly’s vulnerability differed in its implementation. When users attempted to log in using the “Sign in with Facebook” option, an HTTP POST request was sent to auth.grammarly.com for authentication via a secret code. While Grammarly was not susceptible to token reuse attacks like Vidio and Bukalapak, it was vulnerable to a different problem. Attackers could alter the POST request to replace the secret code with an access token obtained from a malicious website, granting unauthorized access to the account. As with the other cases, Grammarly’s implementation lacked proper token verification.
Trending: Offensive Security Tool: o365sprayer
These findings highlight the risks associated with OAuth implementations in popular online services and the importance of robust security measures to protect user accounts and sensitive data. The responsible disclosure of these vulnerabilities and their subsequent remediation serve as a critical reminder of the ongoing efforts to maintain the security and integrity of online platforms.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












