Several PoC exploits targeting the recent critical Jenkins vulnerability CVE-2024-23897 have been made public

Researchers caution that multiple proof-of-concept (PoC) exploits, aimed at the recently revealed critical Jenkins vulnerability CVE-2024-23897, have been disclosed to the public.
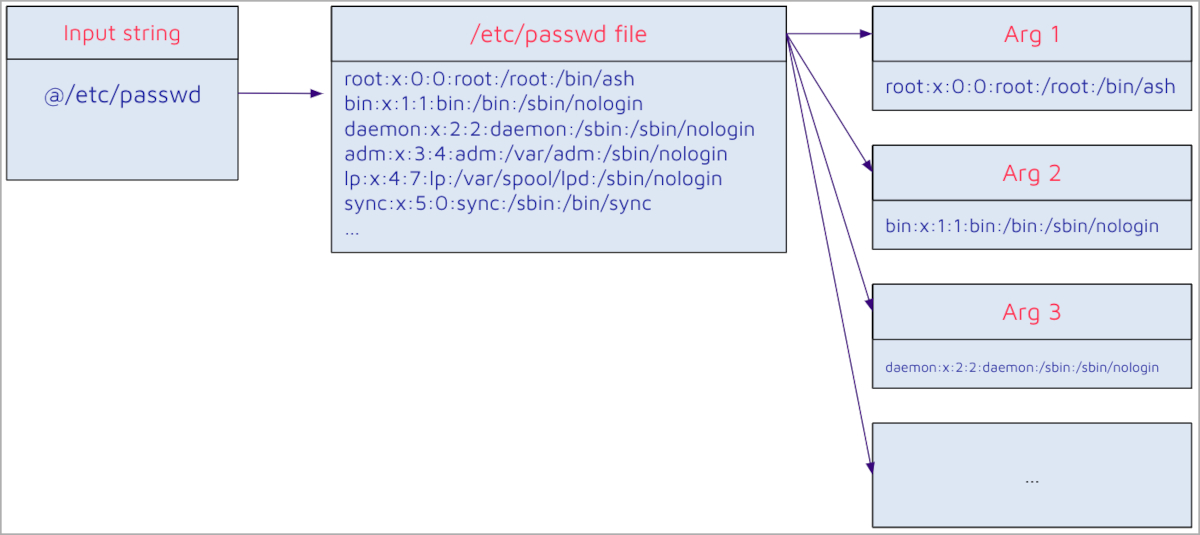
The revelations follow the discovery of two flaws by SonarSource researchers, with the first flaw (CVE-2024-23897) deemed critical, allowing unauthenticated attackers with ‘overall/read’ permissions to read data from arbitrary files on Jenkins servers. Unauthorized access to sensitive information and potential admin privilege escalation are among the risks associated with this flaw.
 Exploitation diagram (SonarSource)
Exploitation diagram (SonarSource)
The second flaw, identified as CVE-2024-23898, introduces a cross-site WebSocket hijacking issue, creating a pathway for attackers to execute arbitrary CLI commands by manipulating users into clicking malicious links. Although existing protective policies in web browsers are designed to mitigate this risk, inconsistent enforcement may leave certain vulnerabilities unaddressed.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
SonarSource reported the identified flaws to the Jenkins security team in November 2023, and fixes were released on January 24, 2024, with Jenkins versions 2.442 and LTS 2.426.3. Despite the prompt release of security updates, the public availability of detailed information and PoC exploits has raised concerns, with reports indicating that attackers may have already initiated exploitation attempts in the wild.
This vulnerability in #Jenkins is serious CVE-2024-23897
POCs have been published https://t.co/nGtbf8fehdhttps://t.co/pzY0NSL5bA
report by @SonarSource https://t.co/VNAUg2PDN8 pic.twitter.com/vbiWGmj47M
— Florian Roth (@cyb3rops) January 26, 2024
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













