Sharp Panda Strikes Again: Advanced Tactics in Latest Espionage Campaign

Chinese Hackers Targeting Southeast Asian Governments with New ‘Soul’ Malware
Sharp Panda, a notorious Chinese cyber-espionage hacking group, has been targeting high-profile government entities in Vietnam, Thailand, and Indonesia with a new version of the ‘Soul’ malware framework. Check Point, a leading cybersecurity company, identified the new campaign in late 2022 and found that it continues to operate in 2023, using spear-phishing attacks for initial compromise.
The malware was previously used in espionage campaigns targeting critical Southeast Asian organizations, which were attributed to various Chinese APTs. The latest operation by Sharp Panda employs the use of the RoyalRoad RTF kit, C2 server addresses, and specific working hours to evade detection and blend in with general network traffic.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Sharp Panda’s new campaign employs custom C2 protocols and ‘radio silence’ mode
The infection chain of the new campaign involves spear-phishing emails with malicious DOCX file attachments that deploy the RoyalRoad RTF kit to exploit older vulnerabilities and drop malware on the host. The malware downloader then fetches and executes a second DLL from the C2 server, the SoulSearcher loader. This second DLL loads the Soul modular backdoor into memory, which helps evade detection from antivirus tools running on the breached system.
Once executed, the main module of the Soul malware establishes a connection with the C2 and waits for additional modules to extend its functionality. The new version analyzed by Check Point features a “radio silence” mode that allows threat actors to specify the specific hours of the week that the backdoor should not communicate with the C2 server.
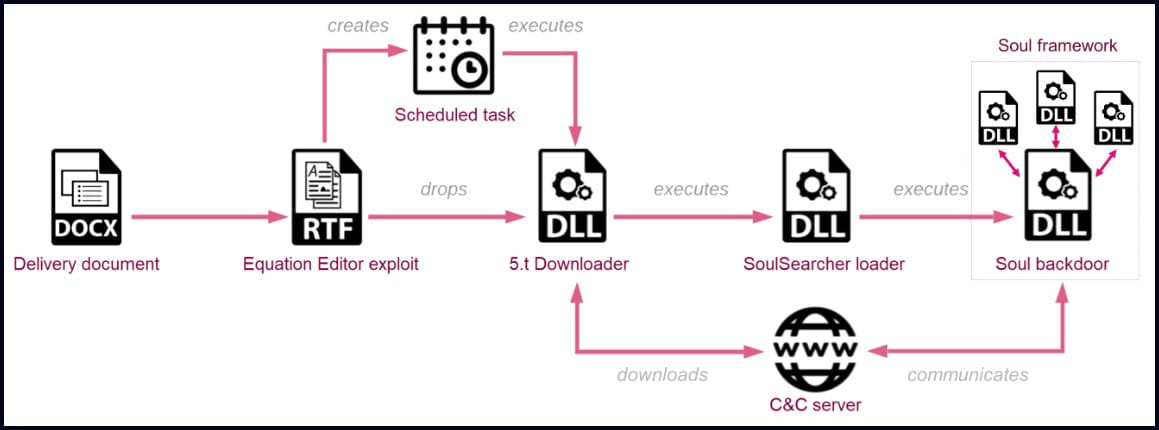 Infection chain (Check Point)
Infection chain (Check Point)
Trending: Offensive Security Tool: SecretOpt1c
Soul details
Once executed, the main module of the Soul malware establishes a connection with the C2 and waits for additional modules to extend its functionality. The new version analyzed by Check Point features a “radio silence” mode that allows threat actors to specify the specific hours of the week that the backdoor should not communicate with the C2 server.
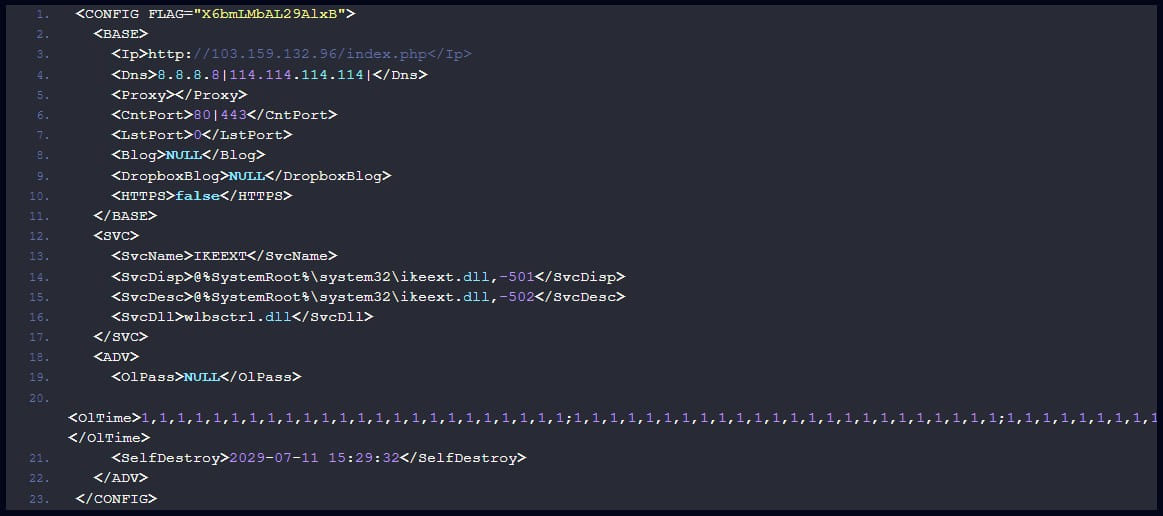 Main backdoor configuration (Check Point)
Main backdoor configuration (Check Point)
The custom C2 communication protocol implemented by the new variant uses various HTTP request methods, giving the malware flexibility to retrieve and submit data. Soul communicates with the C2 by registering itself and sending victim fingerprinting data, after which it enters an infinite C2 contacting loop. The commands it may receive concern loading additional modules, collecting and resending enumeration data, restarting the C2 communication, or exiting its process.
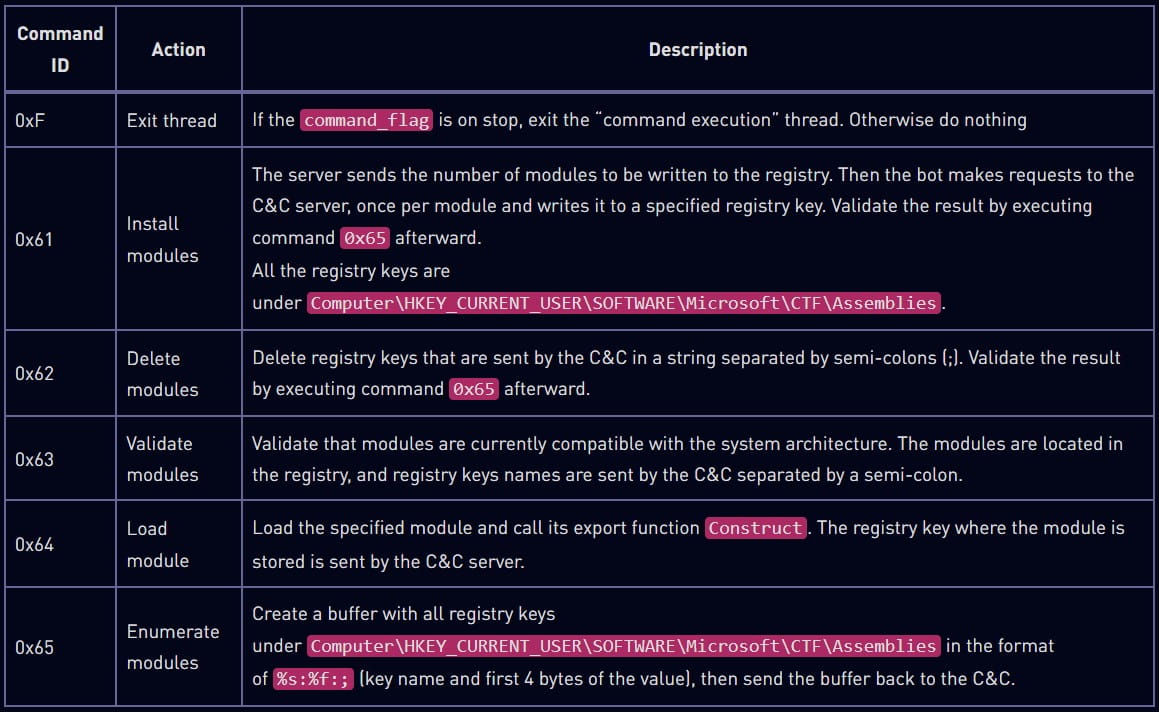 Commands supported by Soul (Check Point)
Commands supported by Soul (Check Point)
Despite being first seen in 2017 and subsequently tracked throughout 2019 in Chinese espionage campaigns by threat actors with no apparent links to Sharp Panda, Check Point’s recent findings show that the Soul framework is still under active development and deployment.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












