Signal Enhances Desktop Client Security After Six-Year Delay on Encryption Key Issue

Signal has finally addressed a critical security flaw in its desktop application, which involved storing encryption keys in plain text, making encrypted databases vulnerable. The issue, initially reported in 2018, resurfaced recently, prompting Signal to implement a fix using Electron’s SafeStorage API
Background on the Issue
In 2018, BleepingComputer highlighted a significant security flaw in Signal’s desktop application for Windows and Mac, where the encryption key for the user’s message database was stored in plain text. This database, an encrypted SQLite file, was designed to protect user messages. However, storing the encryption key as plain text in local files (%AppData%\Signal\config.json on Windows and ~/Library/Application Support/Signal/config.json on Mac) rendered this protection ineffective. Any user or program on the computer could access this key, undermining the encryption.
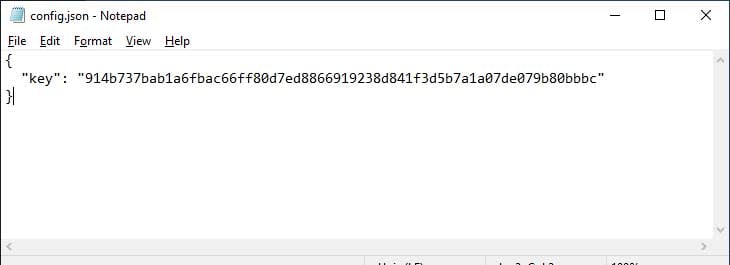 Decryption key in Signal’s config.json on Windows
Decryption key in Signal’s config.json on Windows
Source: BleepingComputer
Initial Response from Signal
At the time, Signal dismissed the issue, asserting that the database key was never intended to be a secret and that at-rest encryption was not a claimed feature of Signal Desktop. This stance contrasted sharply with Signal’s reputation for security and privacy, drawing criticism for not addressing the flaw.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Reemergence of the Issue
The topic resurfaced when Elon Musk tweeted about unaddressed vulnerabilities in Signal, sparking renewed attention. Mobile security researchers Talal Haj Bakry and Tommy Mysk from Mysk Inc reiterated the issue, demonstrating that Signal Desktop still stored encryption keys in plain text, exposing users to potential data exfiltration.
https://x.com/mysk_co/status/1809287118235070662
Signal’s Response to Renewed Criticism
Signal President Meredith Whittaker acknowledged the flaw but downplayed its impact, noting that it required full device access by an attacker. Despite this, Whittaker’s stance seemed inconsistent with her critiques of similar security issues in other software.
The Move to Enhance Security
Amidst this renewed scrutiny, an independent developer, Tom Plant, proposed a fix using Electron’s SafeStorage API to secure the encryption key with platform-specific APIs, such as DPAPI on Windows and Keychain on macOS. Initially ignored, this proposal gained traction after the public outcry on social media.
Trending: Digital Forensics Tool: MalStatWare
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com