Silent Intruder: The Undetected Krasue RAT Malware Targeting Linux Systems Since 2021

A recently discovered remote access trojan (RAT) named Krasue has set its sights on Linux systems within the telecommunications sector, eluding detection since 2021.
Researchers from cybersecurity company Group-IB unraveled Krasue’s tactics, revealing its binary’s incorporation of seven rootkit variants compatible with multiple Linux kernel versions. This trojan, employing code derived from three open-source projects, primarily serves to sustain access to the host, hinting at potential deployment through a botnet or via initial access brokers for threat actors seeking specific targets.
While the distribution method remains unclear, possibilities include exploitation of vulnerabilities, credential brute force attacks, or even downloads from untrusted sources disguised as legitimate products.
 Threat actor’s profile (Group-IB)
Threat actor’s profile (Group-IB)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The targeted scope of Krasue appears confined to telecommunications companies in Thailand.
Analysis by Group-IB disclosed that the rootkit embedded in Krasue RAT’s binary operates as a Linux Kernel Module (LKM), masquerading as an unsigned VMware driver upon execution. Operating at the kernel level, rootkits of this nature pose challenges in detection and removal, as they function at the same security level as the operating system.
The rootkit accommodates Linux Kernel versions 2.6x/3.10.x, exploiting the limited Endpoint Detection and Response coverage of older Linux servers. All seven rootkit versions share system call and function call hooking capabilities, adopting the common guise of “VMware User Mode Helper.”
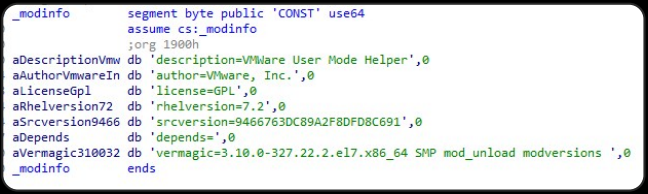 Rootkit’s metadata (Group-IB)
Rootkit’s metadata (Group-IB)
Upon scrutiny of the code, researchers identified the rootkit’s foundation in three open-source LKM rootkits: Diamorphine, Suterusu, and Rooty, all in circulation since at least 2017.
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: Offensive Security Tool: ThreatMapper
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













