SLUBStick: A Novel Linux Kernel Cross-Cache Attack

SLUBStick is a newly discovered cross-cache attack targeting the Linux kernel, capable of converting limited heap vulnerabilities into arbitrary memory read-and-write capabilities with a 99% success rate. This attack enables threat actors to elevate privileges or escape containers, posing significant security risks.
Discovery and Demonstration
Researchers from Graz University of Technology have uncovered this exploit, demonstrating its effectiveness on Linux kernel versions 5.9 and 6.2 using nine existing CVEs on both 32-bit and 64-bit systems. Impressively, SLUBStick remains effective even with modern kernel defenses such as Supervisor Mode Execution Prevention (SMEP), Supervisor Mode Access Prevention (SMAP), and Kernel Address Space Layout Randomization (KASLR) enabled.
Technical Presentation
The SLUBStick attack will be presented at the Usenix Security Symposium, showcasing its ability to achieve privilege escalation and container escape on the latest Linux systems with state-of-the-art defenses. The detailed technical paper outlining the attack and potential exploitation scenarios has been published and is available for further study.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Understanding SLUBStick
SLUBStick manipulates the memory allocation process in the Linux kernel, targeting slabs used for different data structures. Here’s a breakdown of the attack:
1. Exploiting Heap Vulnerabilities:
- SLUBStick leverages heap vulnerabilities like double-free, use-after-free, or out-of-bounds write to manipulate the memory allocation process.
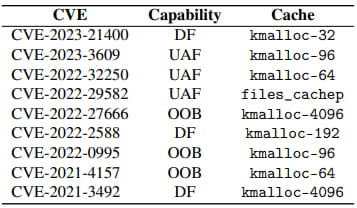 CVEs successfully used in the researchers’ experiments
CVEs successfully used in the researchers’ experiments
Source: stefangast.eu
2. Timing Side Channel:
- The attack employs a timing side channel to monitor memory chunk allocation and deallocation. This precise timing information allows attackers to predict and control memory reuse accurately.
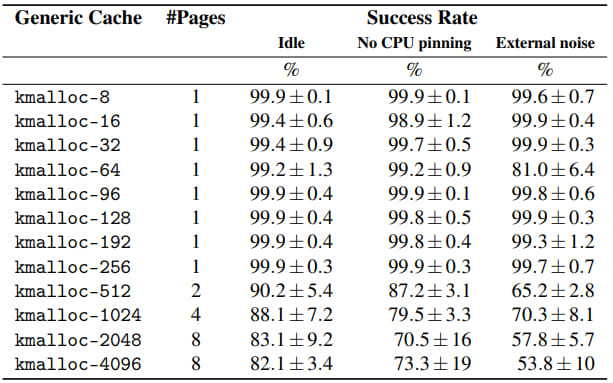 Measured success rates
Measured success rates
Source: stefangast.eu
3. Steps to Achieve Memory Read-Write:
- Free Specific Chunks: The attacker frees specific memory chunks and waits for the kernel to reuse them.
- Controlled Reallocation: The freed chunks are reallocated in a controlled manner, repurposing them for critical data structures like page tables.
- Overwrite Page Tables: Once reclaimed, the attacker overwrites the page table entries, gaining the ability to read and write any memory location.
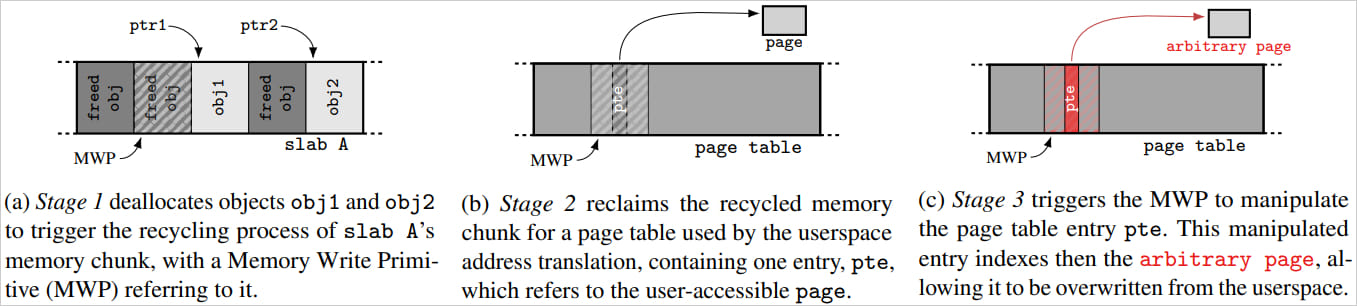 SLUBStick overview
SLUBStick overview
Source: stefangast.eu
Real-World Impact
While SLUBStick requires local access and code execution capabilities on the target machine, its implications are substantial:
- Privilege Escalation: Attackers can elevate privileges to root, allowing unrestricted operations.
- Container Escape: The attack can break out of sandboxed environments, providing access to the host system.
- Post-Exploitation: SLUBStick can modify kernel structures or hooks to maintain persistence, making malware harder to detect.
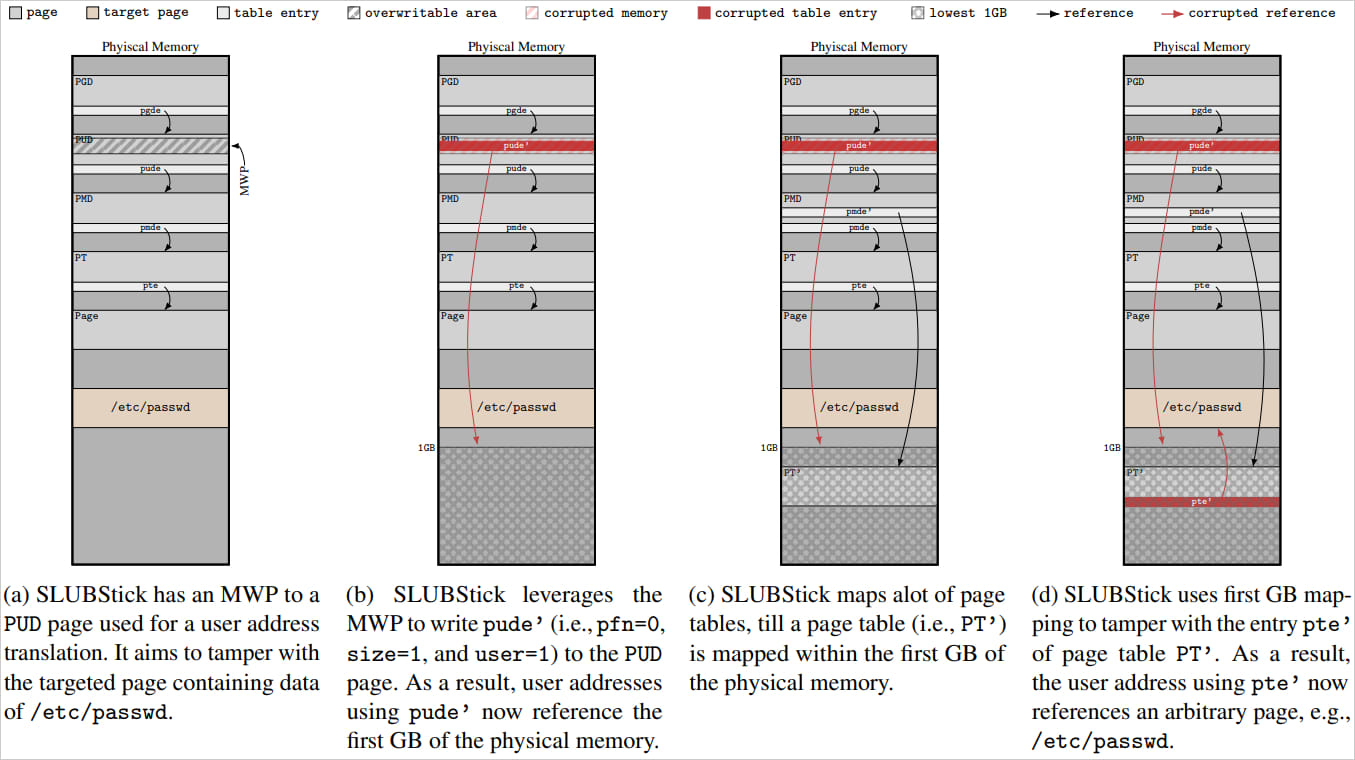 Tampering with ‘/etc/passwd’ data
Tampering with ‘/etc/passwd’ data
Source: stefangast.eu
Trending: Deep Dive to Fuzzing for Maximum Impact
Trending: Offensive Security Tool: DDoSlayer
Practical Use and Mitigation
The attack’s high success rate and ability to bypass advanced defenses make it a potent tool for threat actors. To explore SLUBStick further or experiment with the exploits, researchers have made the details available on their GitHub repository.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













