Sniper Dz: The PhaaS Platform Behind 140,000+ Phishing Sites Exposed

A phishing-as-a-service (PhaaS) platform named Sniper Dz has been linked to more than 140,000 phishing websites over the past year, demonstrating its widespread use by cybercriminals to steal credentials.
Free Phishing Kits with Double Theft Capabilities
Researchers from Palo Alto Networks Unit 42 have reported that Sniper Dz provides an online admin panel featuring phishing templates for a variety of websites, such as X (Twitter), Facebook, Instagram, Netflix, PayPal, and many more. While these phishing kits are available for free, the credentials harvested by cybercriminals are also exfiltrated to the Sniper Dz operators—a tactic known as double theft.
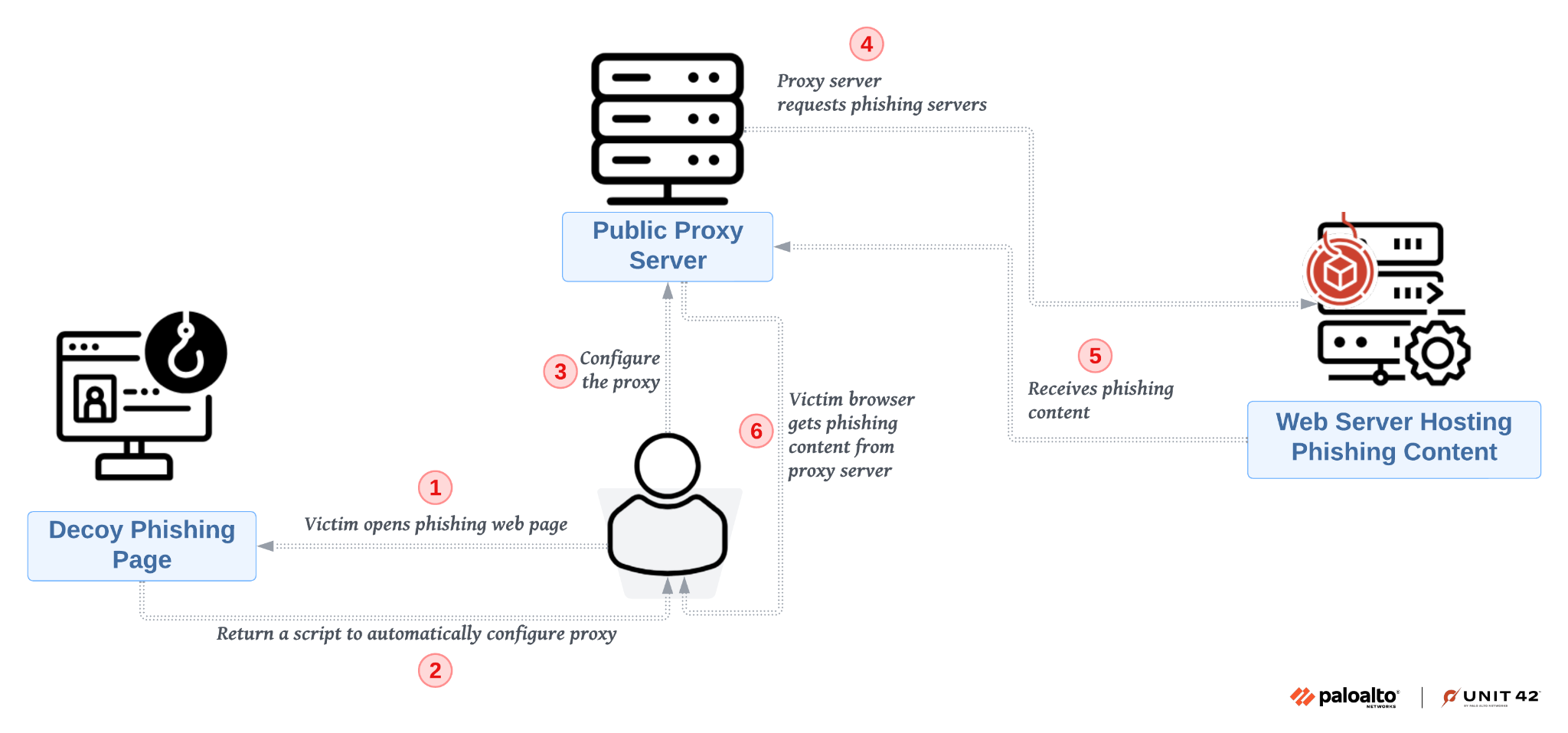 Workflow of hiding phishing content behind a public proxy server.
Workflow of hiding phishing content behind a public proxy server.
Telegram Channel with Over 7,000 Subscribers
Sniper Dz maintains an active presence on Telegram, with a channel boasting over 7,170 subscribers as of October 1, 2024. Interestingly, a day after the release of Unit 42’s report, the platform’s operators activated auto-delete for posts after one month, possibly as an attempt to cover their tracks.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Hosting Options and Proxy Masking for Phishing Pages
Sniper Dz allows phishers to either host phishing pages on Sniper Dz-owned infrastructure or download phishing templates for use on other servers. Additionally, these phishing pages are often hidden behind a proxy server (proxymesh[.]com), preventing detection by security crawlers.
 List of downloadable phishing template pages from the Sniper Dz site.
List of downloadable phishing template pages from the Sniper Dz site.
Trending: OSINT Tool: Pytster
Growing Threat to U.S. Web Users
A surge in phishing activity targeting U.S. users was observed starting in July 2024, with Unit 42 attributing the rise to Sniper Dz. The phishing pages exfiltrate credentials and track victims through a centralized platform, potentially allowing Sniper Dz to collect credentials harvested by its users.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com













