SSH-Snake: The Advanced Tactics of an Evolved SSH Worm

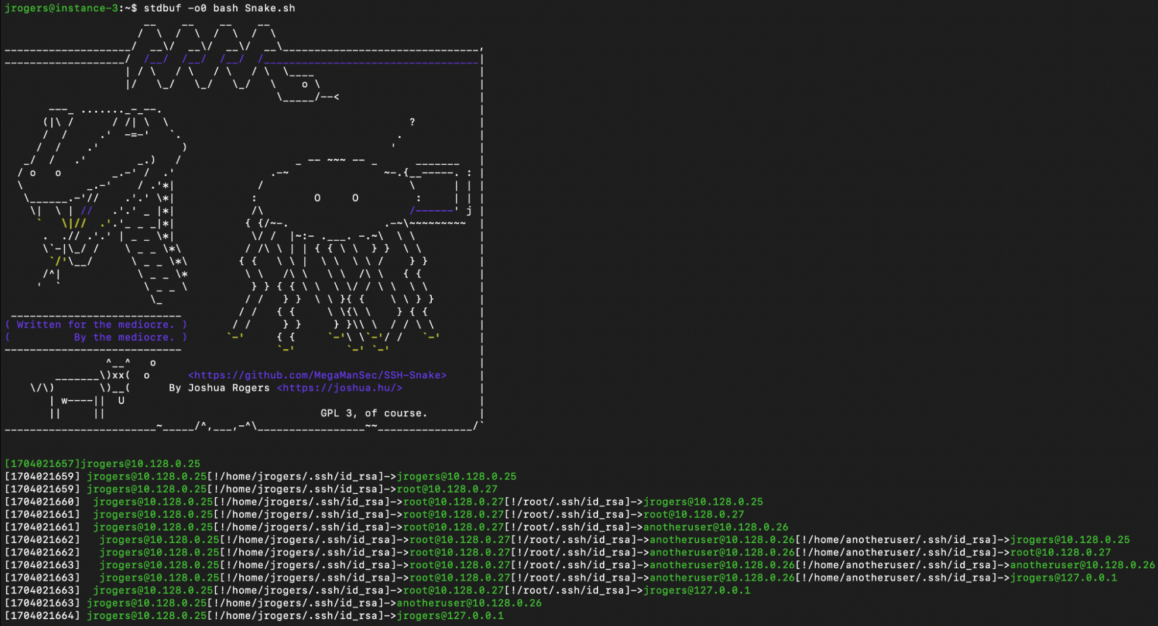
A threat actor is leveraging an open-source network mapping tool known as SSH-Snake to stealthy hunt for private keys and move laterally on victim’s infrastructure. Discovered by the Sysdig Threat Research Team (TRT), SSH-Snake represents a significant departure from conventional SSH worms, employing sophisticated techniques to evade detection while orchestrating lateral movement within compromised networks.
Unlike its predecessors, SSH-Snake operates as a “self-modifying worm,” a term coined by TRT to underscore its adaptive nature. By deviating from the recognizable patterns associated with scripted attacks, SSH-Snake achieves a level of stealth and flexibility previously unseen in SSH-based exploits. Its primary objective: to meticulously search for private keys across diverse locations within breached systems, enabling seamless propagation across network boundaries.
Released on January 4, 2024, SSH-Snake is a bash shell script engineered to autonomously scour compromised systems for SSH credentials, subsequently utilizing them to expand its foothold within the network. Notably, SSH-Snake possesses the unique capability to self-modify, streamlining its execution by eliminating extraneous code elements such as comments, redundant functions, and whitespace.
 The SSH-Snake script (Sysdig)
The SSH-Snake script (Sysdig)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
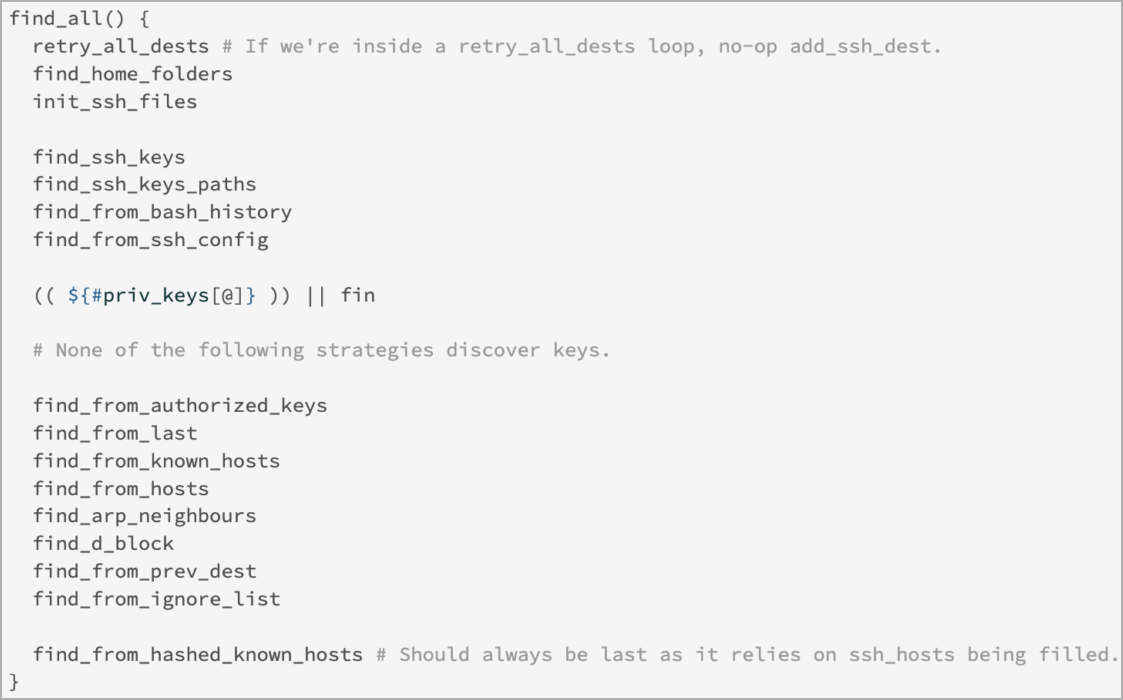
Distinguished by its adaptability, SSH-Snake offers a plug-and-play framework while accommodating customization to suit specific operational requirements. Its comprehensive credential discovery capabilities surpass those of traditional SSH worms, thanks to a multifaceted approach that encompasses both direct and indirect methods.
Among SSH-Snake’s arsenal of techniques are:
- Probing common directories and files where SSH keys and credentials are conventionally stored, including .ssh directories and configuration files.
- Parsing shell history files to uncover commands associated with SSH operations, such as ssh, scp, and rsync, which may contain references to private keys.
- Leveraging the ‘find_from_bash_history’ feature to extract SSH-related commands from bash history files, aiding in the identification of private key locations and associated credentials.
- Scrutinizing system logs and network cache to glean insights into potential targets and indirectly uncover private keys.
 Searching for SSH keys (Sysdig)
Searching for SSH keys (Sysdig)
Trending: Major Cyber Attacks that shaped 2023
Trending: Offensive Security Tool: SmuggleFuzz


