Stealthy Linux Malware ‘Sedexp’ Evades Detection with New Persistence Technique

A newly discovered Linux malware named ‘sedexp’ has been silently operating since 2022, evading detection by using a persistence technique that is not yet recognized in the MITRE ATT&CK framework. Identified by cybersecurity experts from Stroz Friedberg, an Aon Insurance company, sedexp is a sophisticated threat that allows attackers to establish reverse shells for remote access, potentially leading to further system compromises.
Undocumented Persistence via Udev Rules
Sedexp’s persistence method revolves around exploiting ‘udev,’ a device management system integral to the Linux kernel. Udev manages device nodes in the /dev directory, which represents the hardware components on a system, such as storage drives and network interfaces. These nodes are dynamically created and removed as devices are connected or disconnected.
The persistence is achieved by manipulating udev rules, which are configuration files located in /etc/udev/rules.d/ or /lib/udev/rules.d/. These rules define how udev should handle certain devices or events, with parameters specifying the conditions and the script to be executed.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Sedexp introduces the following rule into the compromised system:
ACTION=="add", ENV{MAJOR}=="1", ENV{MINOR}=="8", RUN+="asedexpb run:+"
This rule triggers whenever a new device is added, specifically checking if its major and minor numbers match those of /dev/random, a critical system component loaded at boot time. /dev/random is used as a random number generator by various applications and processes, making it an ideal candidate for frequent triggering without raising suspicion.
The rule’s final component, RUN+="asedexpb run:+", executes the malware’s script whenever /dev/random is involved, ensuring the malware runs consistently and evades detection by leveraging a commonly trusted system component.
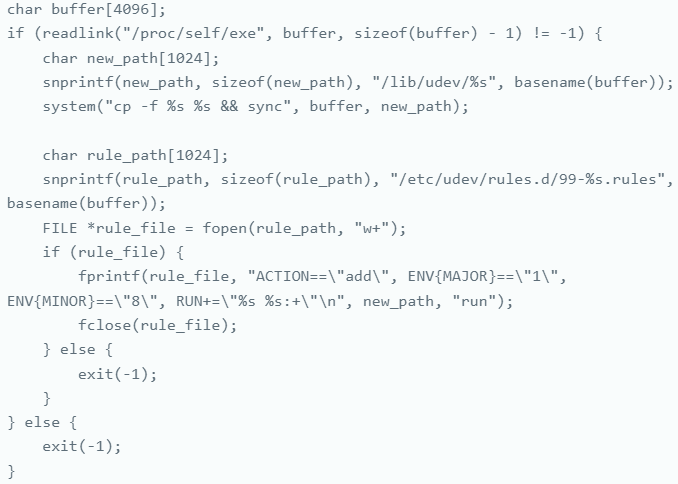 Establishing persistence on the system
Establishing persistence on the system
Source: Aon
Advanced Operational Capabilities
Sedexp further disguises itself by naming its process ‘kdevtmpfs,’ mimicking a legitimate system process. This naming convention allows it to blend seamlessly with other system activities, making it difficult to identify through conventional monitoring tools.
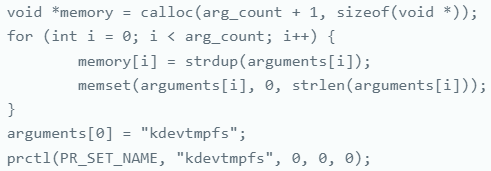 Process naming to blend with system operations
Process naming to blend with system operations
Source: Aon
The malware is designed to set up a reverse shell on the infected device, using either forkpty or pipes combined with a forked process. This reverse shell provides attackers with remote access to the compromised system.
Sedexp employs advanced memory manipulation techniques to conceal its presence. It hides files containing the string “sedexp” from being displayed in standard commands like ls or find, preventing easy detection. Additionally, it can modify memory contents to inject malicious code or alter the behavior of existing applications and system processes.
Trending: Digital Forensics Tool: Horus
Detection and Impact
Sedexp has been active since at least 2022, remaining undetected in many instances. Researchers found it in multiple online sandboxes and noted that it was flagged as malicious by only two antivirus engines on VirusTotal. The malware has been linked to financially motivated attacks, particularly in hiding credit card scraping code on compromised web servers.
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













