StripedFly Malware: A Five-Year Undetected Threat to Windows and Linux Systems

Researchers at Kaspersky recently uncovered a highly sophisticated cross-platform malware platform named “StripedFly” that managed to operate under the radar for five years. During this time, StripedFly stealthily infected over a million Windows and Linux systems.
The true nature of this malicious framework was discovered last year, with its activity dating back to 2017, although it had initially been misclassified as a mere Monero cryptocurrency miner.
Kaspersky’s analysts have described StripedFly as nothing short of impressive, with its advanced features such as TOR-based traffic concealment, automated updates from trusted platforms, worm-like spreading capabilities, and even a custom EternalBlue SMBv1 exploit developed before the flaw was publicly disclosed.
While it remains unclear whether StripedFly was employed for revenue generation or cyber espionage, its extraordinary sophistication strongly suggests it falls into the category of APT (Advanced Persistent Threat) malware.
Based on the compiler timestamp for the malware, the earliest known version featuring an EternalBlue exploit dates back to April 2016, while the public leak of this exploit occurred in August 2016.
Infecting over a million systems
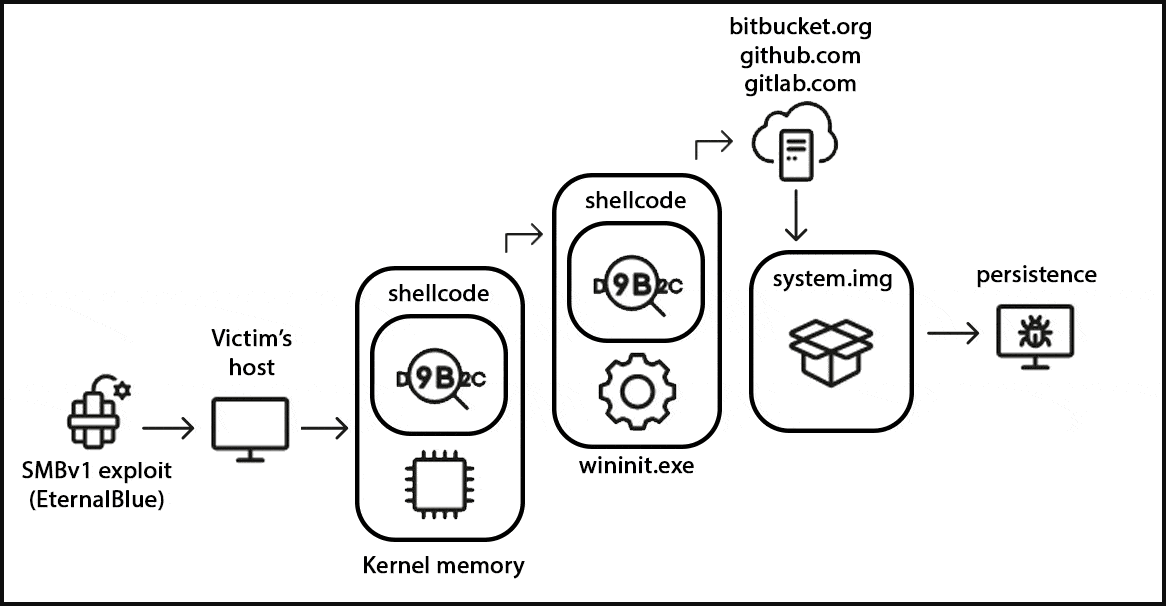
StripedFly was initially discovered after Kaspersky detected its shellcode injected into the legitimate WININIT.EXE process, responsible for initializing various subsystems in the Windows operating system. Upon closer investigation, it became apparent that StripedFly downloaded and executed additional files, including PowerShell scripts, from reputable hosting services like Bitbucket, GitHub, and GitLab.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Further analysis revealed that compromised devices were likely first breached using a custom EternalBlue SMBv1 exploit, specifically targeting internet-exposed computers.
StripedFly’s final payload featured a customized lightweight TOR network client to secure its network communications from interception, the ability to disable the SMBv1 protocol, and the capacity to spread to other Windows and Linux devices on the network using SSH and EternalBlue.
 StripedFly’s infection chain (Kaspersky)
StripedFly’s infection chain (Kaspersky)
For persistence on Windows systems, StripedFly adapted its behavior according to the privilege level it ran with and the presence of PowerShell. Without PowerShell, it generated a hidden file in the %APPDATA% directory. In cases where PowerShell was available, it executed scripts for creating scheduled tasks or modifying Windows Registry keys.
On Linux systems, the malware assumed the name ‘sd-pam’ and achieved persistence using systemd services, autostarting .desktop files, or by modifying various profile and startup files.
One striking revelation was that between April 2023 and September 2023, nearly 60,000 systems had been infected by StripedFly via a Bitbucket repository delivering the final stage payload on Windows devices. It is estimated that StripedFly had infected at least 220,000 Windows systems since February 2022, although statistics from before that date are unavailable.
 Payload download count since April 2023 (Kaspersky)
Payload download count since April 2023 (Kaspersky)
Kaspersky’s estimate suggests that over one million devices fell victim to the StripedFly framework.
StripedFly is unique in that it operates as a monolithic binary executable with pluggable modules, providing an operational versatility typically associated with APT operations. These modules include:
- configuration storage
- upgrade/uninstall management
- a reverse proxy, miscellaneous command handling
- credential harvesting, repeatable tasks execution
- a reconnaissance module
- an SSH infector, an SMBv1 infector
- Monero mining module
Trending: Offensive Security Tool: o365sprayer
The presence of the Monero crypto miner is considered a diversion attempt, with the primary objectives of the threat actors being data theft and system exploitation facilitated by the other modules. This multifaceted approach allowed StripedFly to evade detection for an extended period.
Kaspersky experts also identified links to the ransomware variant ThunderCrypt, indicating a possible interest in revenue generation for certain victims. StripedFly represents a significant discovery in the realm of cybersecurity, shedding light on the ever-evolving sophistication of cyber threats in the digital landscape.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












