Super Admin Privilege Vulnerability Plagues MikroTik Routers

A critical vulnerability dubbed CVE-2023-30799 has put over 900,000 MikroTik RouterOS routers at severe risk, allowing attackers to gain “super-admin” privileges and take full control of the devices without detection.
Discovered by renowned Google security researcher Tavis Ormandy, the flaw enables remote attackers with an existing admin account to elevate their privileges through the Winbox or HTTP interface. Although exploitation requires an admin account, the presence of a well-known default “admin” user in the Mikrotik RouterOS operating system makes this a significant concern.
While the vulnerability was initially disclosed without an identifier in June 2022, MikroTik patched the issue in October 2022 for RouterOS stable (v6.49.7) and recently, on July 19, 2023, for RouterOS Long-term (v6.49.8).
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Problem of scale
VulnCheck, a cybersecurity firm, reports that the impact of the flaw is far-reaching, with 474,000 vulnerable devices remotely exposing the web-based management page. However, when accounting for the exploit’s potential over Winbox, a Mikrotek management client, the number of devices exposing this management port balloons to 926,000, making the impact significantly larger.
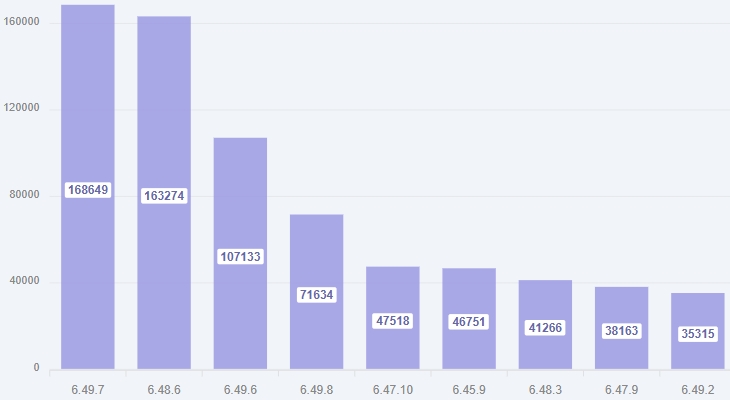 Detected RouterOS versions (VulnCheck)
Detected RouterOS versions (VulnCheck)
CVE-2023-30799
CVE-2023-30799 grants attackers “Super Admin” privileges, offering unrestricted access to the RouterOS operating system. By leveraging this privilege elevation, attackers can manipulate function calls, enabling them to control the underlying software and evade detection.
VulnCheck’s analysts developed an exploit for the flaw using Margin Research’s FOISted remote RouterOS jailbreak exploit, allowing for root shell access on MIPS-based MikroTik devices. This new exploit bypasses FTP interface exposure requirements and remains unaffected by bindshell blocking or filtering, utilizing the RouterOS web interface to upload files.
MikroTik’s default admin user, which is often not removed as recommended, remains a vulnerability point. Additionally, the lack of admin password strengthening requirements exposes users to brute-force attacks, with MikroTik offering no protection except on the SSH interface.
Trending: Digital Forensics Tool: ScrapPy
Update your MikroTik devices
MikroTik users must take immediate action to patch the flaw by applying the latest RouterOS update. To enhance security, users should remove administrative interfaces from the internet, restrict login IP addresses to an allow-list, disable Winbox in favor of SSH, and configure SSH to use public/private keys instead of passwords. Failure to address the vulnerability could lead to disastrous consequences, as threat actors may attempt to exploit it rapidly.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












