Supermicro’s BMCs Under Siege, Critical Vulnerabilities Open Doors to Attackers

A series of critical vulnerabilities has rocked the Intelligent Platform Management Interface (IPMI) firmware for Supermicro baseboard management controllers (BMCs), sending shockwaves through the server management community. These seven flaws, ranging from High to Critical severity and tracked from CVE-2023-40284 to CVE-2023-40290, have raised alarms as they pave the way for privilege escalation and the execution of malicious code on vulnerable systems.
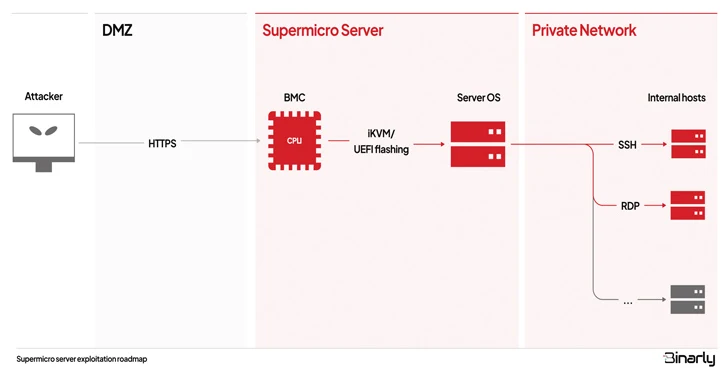
BMCs, or baseboard management controllers, are specialized processors integrated into server motherboards, designed to facilitate remote management. Administrators rely on these controllers to monitor crucial hardware metrics, such as temperature, fan speed, and UEFI system firmware updates. An intriguing feature of BMC chips is their ability to remain operational even when the host operating system is offline, making them a potentially lucrative target for deploying persistent malware.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Let’s delve into the specifics of each vulnerability:
CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288 (CVSS scores: 9.6): These three cross-site scripting (XSS) vulnerabilities allow remote, unauthenticated attackers to execute arbitrary JavaScript code within the context of a logged-in BMC user.
CVE-2023-40285 and CVE-2023-40286 (CVSS score: 8.6): Two more XSS flaws open doors for remote, unauthenticated attackers to execute JavaScript code in the context of the logged-in BMC user, either by poisoning browser cookies or local storage.
CVE-2023-40289 (CVSS score: 9.1): This flaw enables operating system command injection, granting attackers the capability to execute malicious code with administrative privileges. It is deemed critical because it allows authenticated attackers to gain root access, essentially compromising the entire BMC system.
CVE-2023-40290 (CVSS score: 8.3): A cross-site scripting (XSS) vulnerability that permits remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user. Notably, this flaw is effective when using Internet Explorer 11 on Windows.
The gravity of CVE-2023-40289, classified as “critical” by security experts, cannot be overstated. It provides authenticated attackers with a path to root access, thereby comprehensively compromising the BMC system. This level of privilege opens the door to persistent attacks, even during BMC component reboots, enabling lateral movement within the compromised infrastructure and potential infection of other endpoints.
The other six vulnerabilities, particularly CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288, serve as stepping stones for attackers to establish accounts with admin privileges in the web server component of the BMC IPMI software. When combined with CVE-2023-40289, attackers could execute code injection, potentially triggered by malicious links or phishing emails, setting the stage for server takeover.
Trending: Recon Tool: Mantra
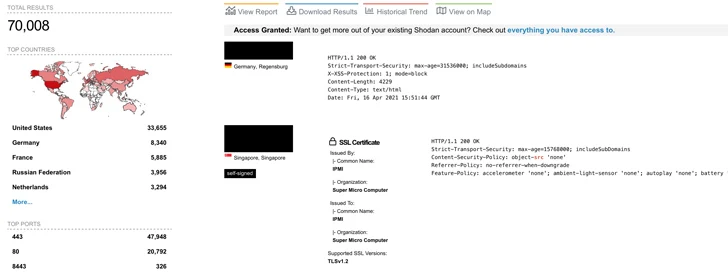
While there is no concrete evidence of malicious exploitation of these vulnerabilities in the wild, the number of internet-exposed Supermicro IPMI web interfaces exceeded 70,000 at the start of October 2023, signaling the urgency of addressing this threat.
In summary, these vulnerabilities expose Supermicro servers to significant risks, including remote compromise of the BMC system. Subsequent access to the server’s operating system could be achieved through legitimate remote control BMC functionality or by installing malicious firmware. This scenario raises concerns about lateral movement within internal networks and the compromise of other vulnerable hosts.
This situation echoes similar vulnerabilities discovered earlier this year in AMI MegaRAC BMCs, underscoring the critical importance of securing BMC firmware in server environments.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












