Supply-Chain Attack Strikes The Largest Discord Bot Community Top.gg

The Top.gg Discord bot community, boasting over 170,000 members, finds itself reeling from the aftermath of a supply-chain attack, aimed at infiltrating developers with malware designed to steal sensitive information.
Perpetrated by a threat actor employing a spectrum of tactics, techniques, and procedures (TTPs), this campaign has been a culmination of years-long efforts, including the hijacking of GitHub accounts, the distribution of malicious Python packages, the establishment of a fake Python infrastructure, and intricate social engineering endeavors.
One of the latest casualties of this assailant’s onslaught is Top.gg, a prominent search-and-discovery platform catering to Discord servers, bots, and assorted social utilities, primarily tailored for gaming communities, enhancing engagement, and refining functionality.
The campaign came to light courtesy of Checkmarx researchers, who uncovered a meticulously orchestrated scheme, with the primary objective likely being data theft and subsequent monetization through the sale of pilfered information.
Hijacking top.gg
Initiating their activity as far back as November 2022, the attacker commenced by uploading malevolent packages onto the Python Package Index (PyPI). Over subsequent years, the malevolent payload expanded, masquerading as popular open-source tools with alluring descriptions designed to elevate their prominence in search engine results.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
March of the current year saw the introduction of “yocolor,” the latest package in the malicious arsenal.
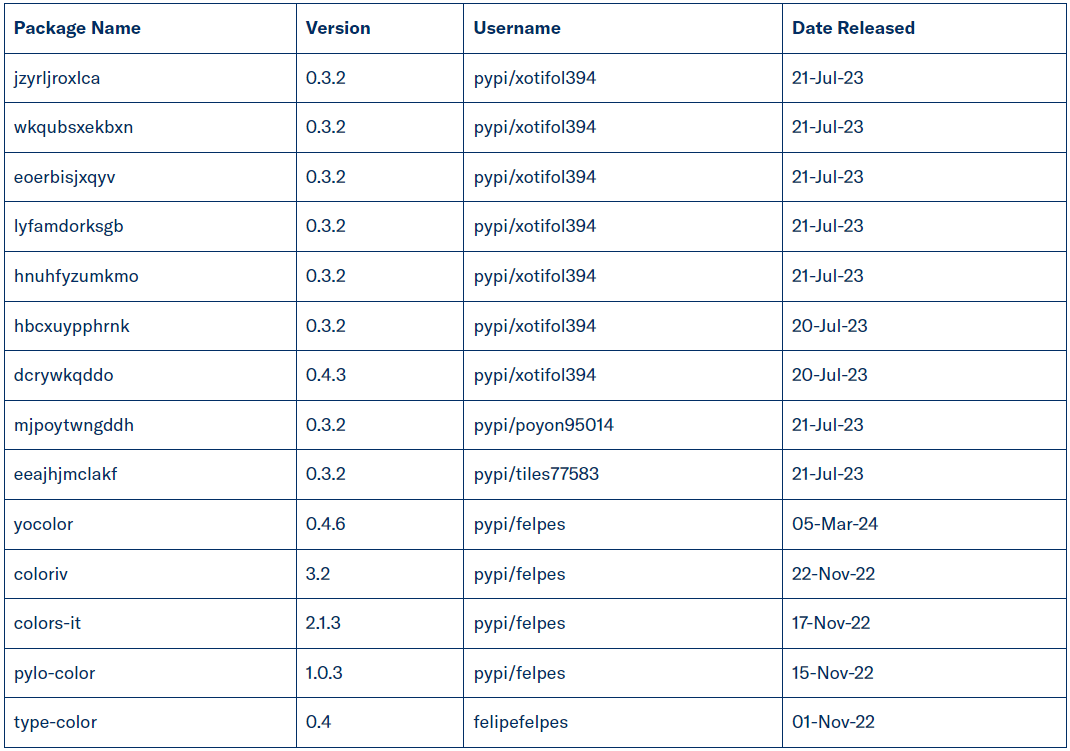 Packages used in the campaign (Checkmarx)
Packages used in the campaign (Checkmarx)
In early 2024, the assailants erected a counterfeit Python package mirror at “files[.]pypihosted[.]org,” a blatant typosquatting ploy mimicking the authentic “files.pythonhosted.org,” the repository for PyPI package artifacts. This deceptive mirror served as a conduit for hosting tainted versions of legitimate packages, such as a tampered iteration of the widely-used “colorama” package, deceiving unsuspecting users and development systems into inadvertently sourcing from this malevolent source.
The malevolent packages disseminated via PyPI served as the initial vector for compromising systems. Upon successful compromise or the hijacking of privileged GitHub accounts, the attackers manipulated project files to reference dependencies hosted on the counterfeit mirror.
Checkmarx underscores a notable incident from March wherein the attackers compromised the account of a top.gg maintainer, “editor-syntax,” wielding substantial write access privileges to the platform’s GitHub repositories.
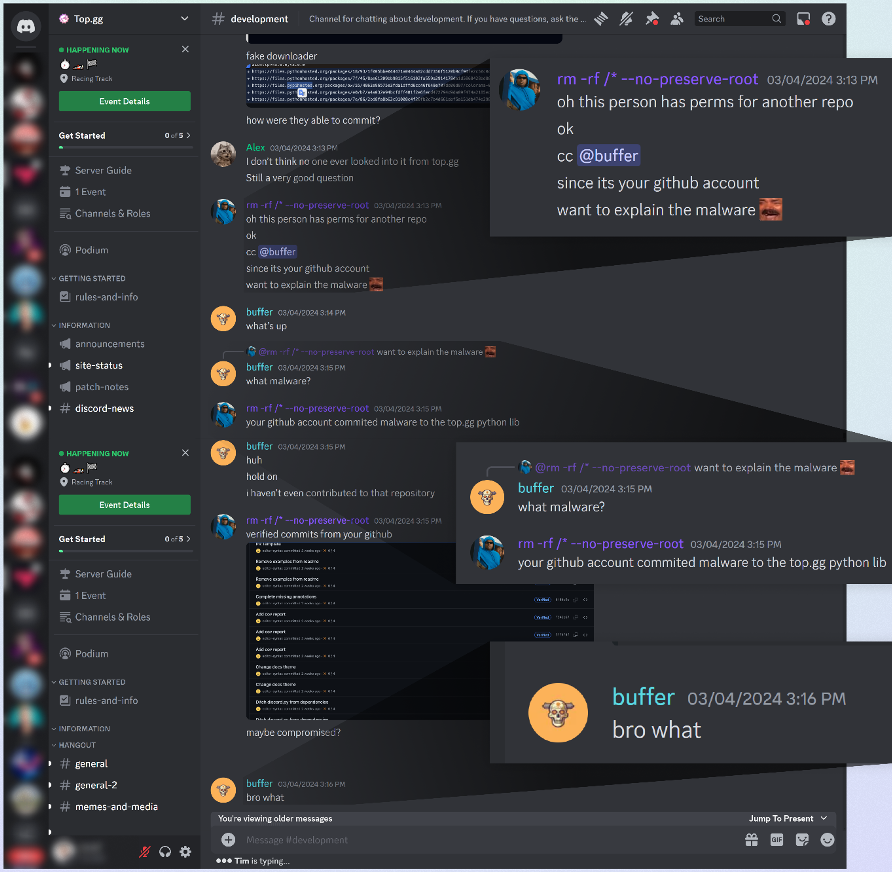 Discussion on Discord about the hacked account (Checkmarx)
Discussion on Discord about the hacked account (Checkmarx)
The attacker utilized this compromised account to perpetrate malicious commits to Top.gg’s python-sdk repository, incorporating a dependency on the tainted version of “colorama” and housing additional malevolent repositories, thus bolstering their visibility and credibility.
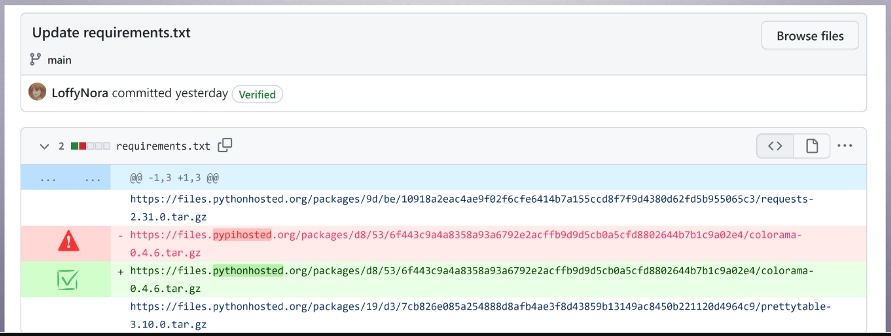 Malicious commit to modify the requirements.txt file (Checkmarx)
Malicious commit to modify the requirements.txt file (Checkmarx)
Trending: Digital Forensics Tool: mailMeta


