TeamsPhisher Exploits Microsoft Teams Security Issue for File Delivery

A member of the U.S. Navy’s red team has developed a tool called TeamsPhisher, which takes advantage of an unresolved security flaw in Microsoft Teams. This flaw allows the tool to bypass restrictions for incoming files from external users, known as external tenants.
Last month, security services company Jumpsec highlighted a problem in Microsoft Teams that could be exploited to deliver malware from an external account. By manipulating the ID in a POST request, an attacker can trick the application’s client-side protections into treating an external user as an internal one.
Teams Attacks
To streamline the attack process, the developer of TeamsPhisher integrated the research conducted by Jumpsec, the techniques developed by Andrea Santese, and the authentication and helper functions from Bastian Kanbach’s ‘TeamsEnum’ tool. This Python-based tool automates the attack, requiring users to have a valid Microsoft Business account with Teams and Sharepoint licenses, which is common among major companies.
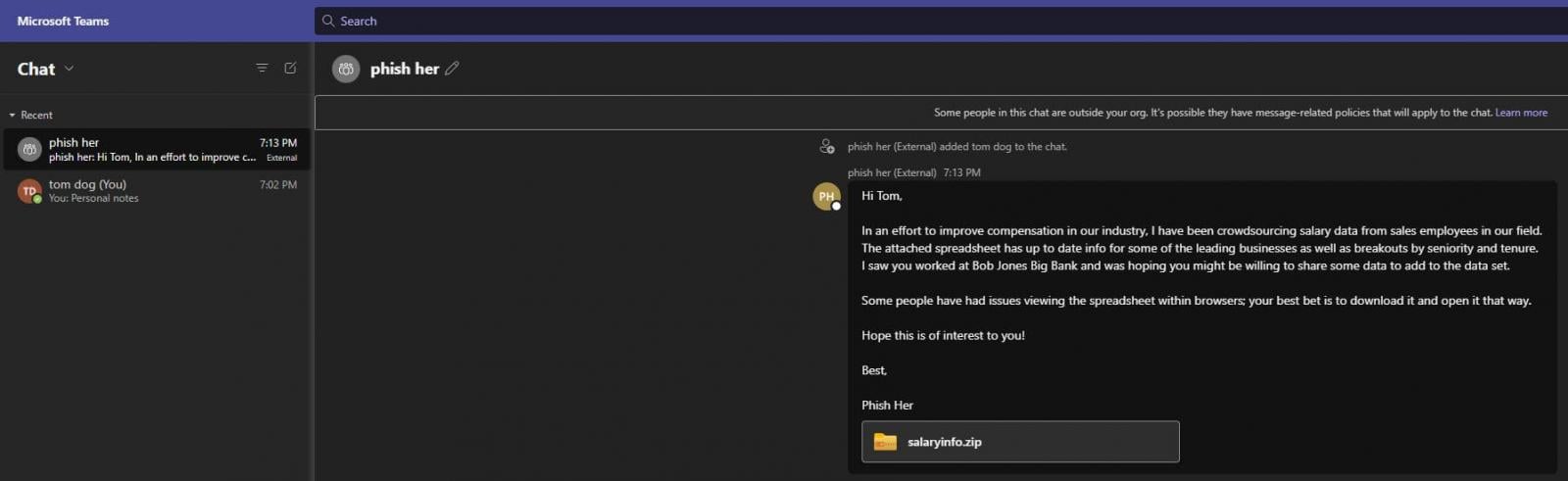 Phishing message as seen by the recipient (github.com/Octoberfest7)
Phishing message as seen by the recipient (github.com/Octoberfest7)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
TeamsPhisher performs various tasks, including verifying the existence of the target user and their ability to receive external messages. It then initiates a new thread with the target and sends them a message containing a Sharepoint attachment link. The tool also offers a “preview mode” to help users verify target lists and check the appearance of messages from the recipient’s perspective.
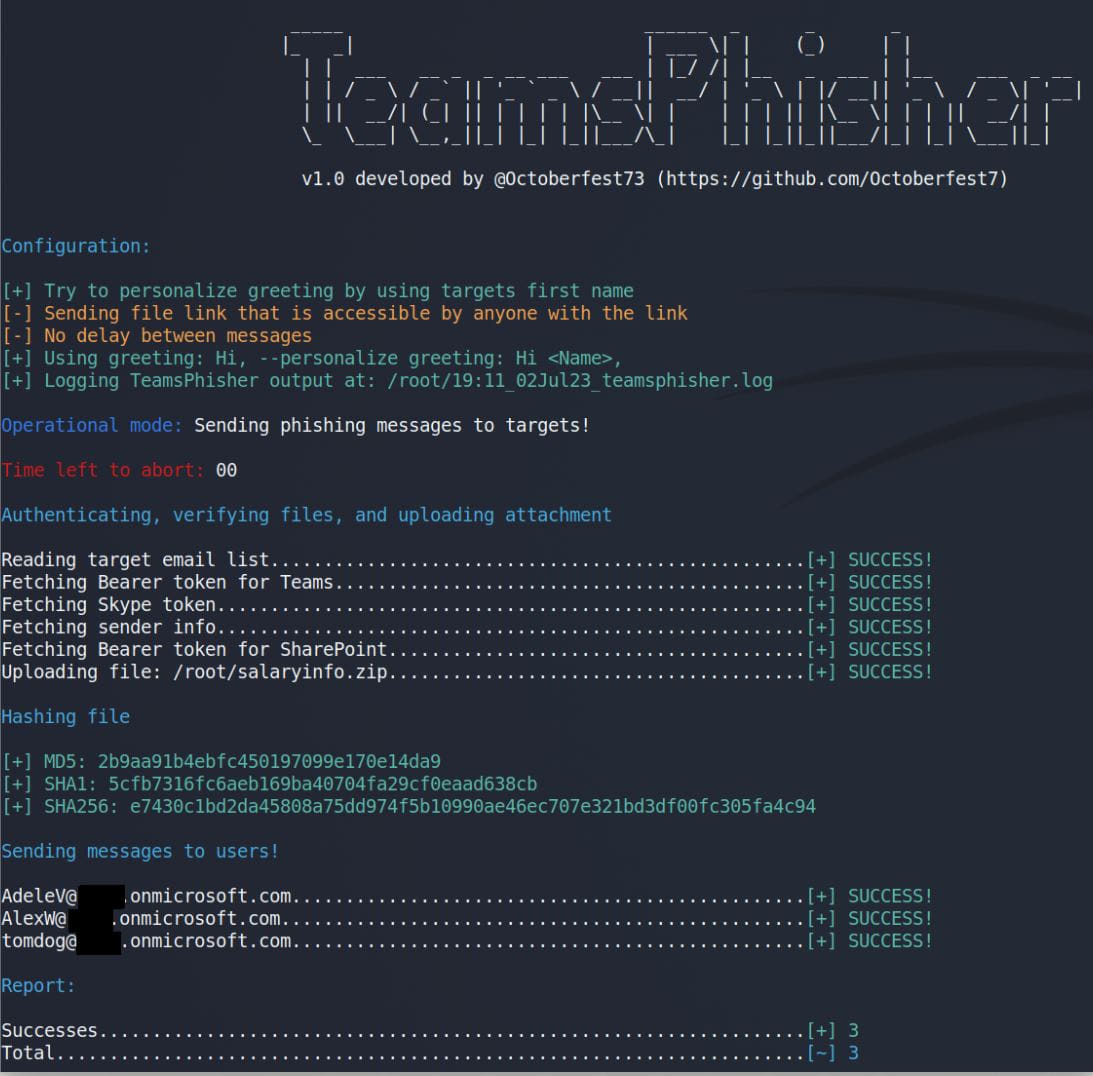 TeamsPhisher output (github.com/Octoberfest7)
TeamsPhisher output (github.com/Octoberfest7)
Additional features and optional arguments further refine the attack, such as sending secure file links limited to the intended recipient and setting delays between message transmissions to bypass rate limiting.
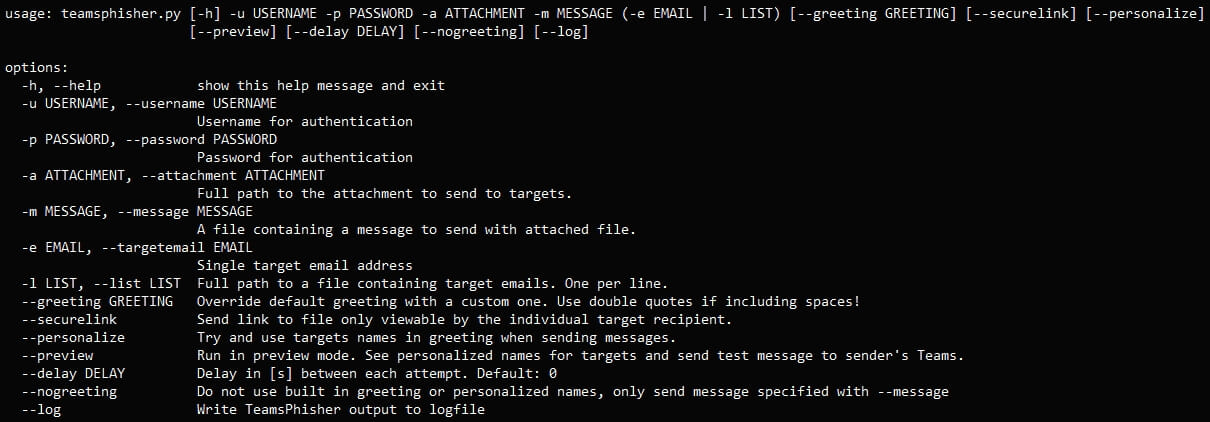 All options and arguments supported by the tool (github.com/Octoberfest7)
All options and arguments supported by the tool (github.com/Octoberfest7)
While the tool was originally developed for authorized red team operations, it has raised concerns regarding potential misuse by threat actors. The underlying security issue exploited by TeamsPhisher remains unaddressed, as Microsoft stated that it did not meet the threshold for immediate servicing. BleepingComputer reached out to Microsoft for comment but did not receive a response at the time of publishing.
Trending: Recon Tool: Logsensor
Mitigations
To mitigate the risk associated with this security flaw, organizations are strongly advised to disable communication with external tenants if not necessary. Implementing an allow-list of trusted domains can also help limit the potential for exploitation. It is important to note that until Microsoft takes action to resolve this issue, the delivery of malware to target organizations using TeamsPhisher could go undetected.
Update: In response to the report, a Microsoft spokesperson stated that the success of the attack relies on social engineering. They emphasized the importance of practicing good computing habits online, such as being cautious when clicking on links, opening unknown files, or accepting file transfers. Vigilance remains key in mitigating potential risks.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












