TeamViewer Abused for Unauthorized Access and Deploying LockBit Ransomware

Ransomware actors are resurfacing their use of TeamViewer to gain initial access to organization endpoints and attempt to deploy encryptors, particularly those based on the leaked LockBit ransomware builder.
This recurrence echoes a similar case reported in March 2016, where TeamViewer was exploited to encrypt files with the Surprise ransomware. At that time, compromised accounts were attributed to credential stuffing rather than a zero-day vulnerability in the software.
A recent report from Huntress reveals that cybercriminals are still leveraging these tactics, taking over devices via TeamViewer to deploy ransomware. Log files analyzed by Huntress indicate connections from the same source, suggesting a common attacker.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Examination of log files (connections_incoming.txt) demonstrated connections originating from the same source in both instances, suggesting a shared attacker. In the first compromised endpoint, multiple accesses logged indicated active usage by employees for legitimate administrative tasks. On the second endpoint, which has been operational since 2018, a lack of activity in the logs over the past three months suggested infrequent monitoring, potentially making it a more appealing target for attackers.
In both cases, attackers sought to deploy ransomware using a DOS batch file (PP.bat) placed on the desktop, triggering the execution of a DLL file (payload) through a rundll32.exe command.
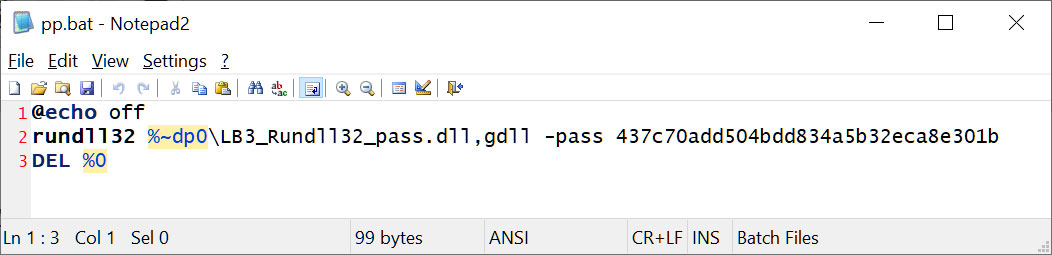 The PP.bat file used to execute ransomware encryptor
The PP.bat file used to execute ransomware encryptor
Source: BleepingComputer
The first endpoint experienced a successful attack that was subsequently contained. However, on the second endpoint, the antivirus product intervened, leading to repeated attempts at payload execution with no success.
While Huntress has not definitively attributed these attacks to any known ransomware gangs, the tactics employed bear similarities to LockBit encryptors generated using a leaked LockBit Black builder. In 2022, the ransomware builder for LockBit 3.0 was leaked, leading to the rapid deployment of campaigns by the Bl00dy and Buhti gangs utilizing the builder’s capabilities.
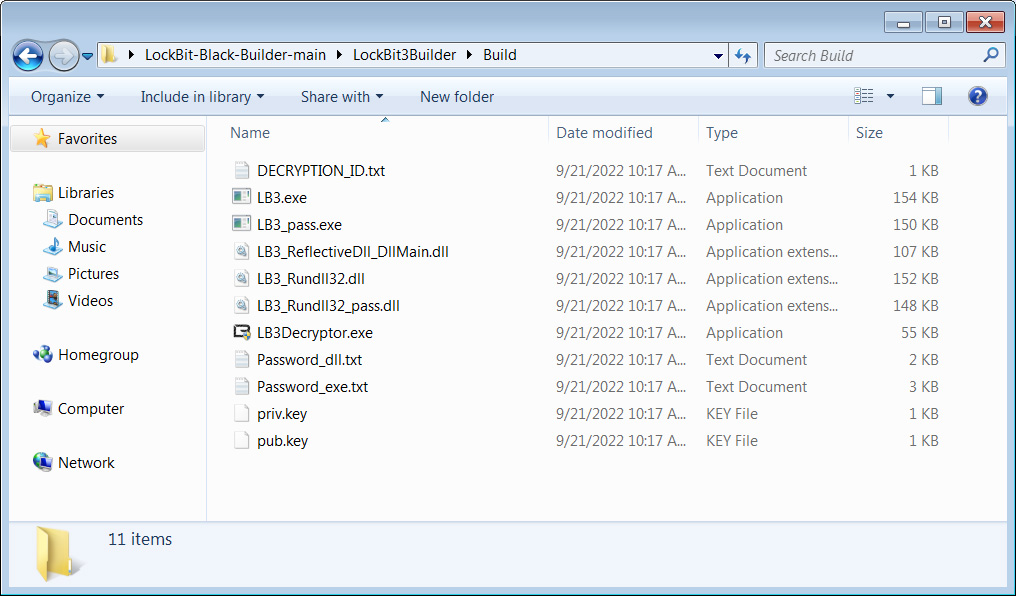 Leaked LockBit 3.0 build
Leaked LockBit 3.0 build
Source: BleepingComputer
The leaked builder enables the creation of different encryptor versions, including an executable, a DLL, and an encrypted DLL requiring a password for proper launch. According to Indicators of Compromise (IOCs) identified by Huntress, the attacks leveraging TeamViewer seem to involve the use of the password-protected LockBit 3 DLL.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













