Telegram-Linked Gitloker Attacks Leave GitHub Repositories Compromised

See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
In light of previous attacks, GitHub has recommended users change their passwords to enhance account security against unauthorized access. This step is essential to prevent malicious actions, such as adding new SSH keys, authorizing new apps, or modifying team members.
To further safeguard GitHub accounts and detect suspicious activity, users should:
- Enable two-factor authentication.
- Add a passkey for secure, passwordless login.
- Review and revoke unauthorized access to SSH keys, deploy keys, and authorized integrations.
- Verify all email addresses associated with the account.
- Review account security logs to monitor repository changes.
- Manage webhooks on repositories.
- Check for and revoke any new deploy keys.
- Regularly review recent commits and collaborators for each repository.
This is not the first instance of GitHub accounts being compromised for data theft. In March 2020, hackers breached Microsoft’s GitHub account, stealing over 500GB of files from private repositories. While most of the stolen data consisted of code samples and test projects, there was concern that private API keys or passwords might have been exposed.
Trending: Offensive Security Tool: Genzai
Are u a security researcher? Or a company that writes articles about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing? If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


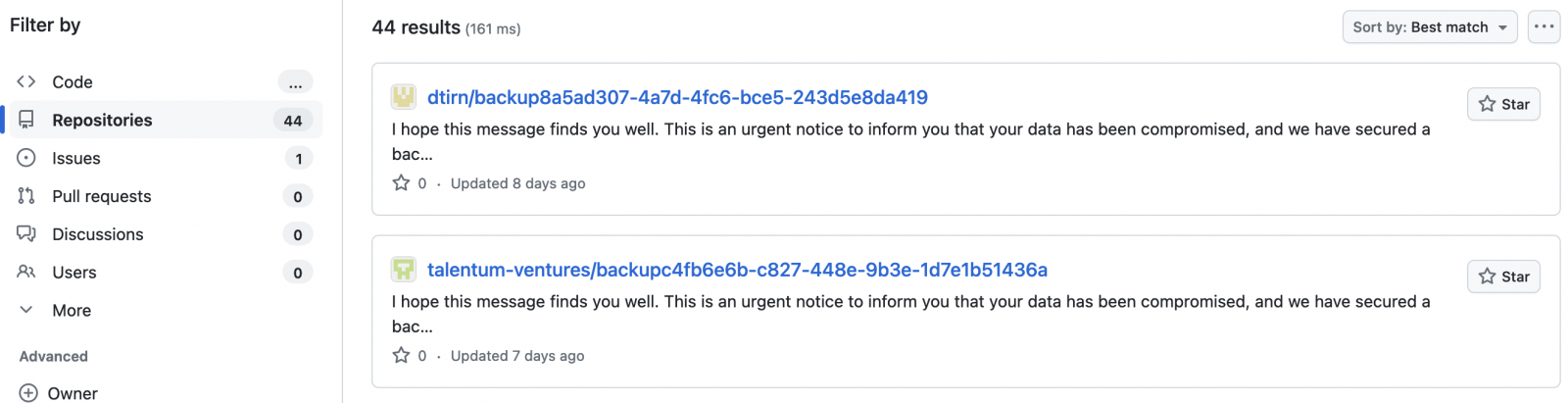 Dozens of GitHub repos already impacted (BleepingComputer)
Dozens of GitHub repos already impacted (BleepingComputer)










