The Deceptive Tactics of the New Linux Bifrost RAT Variant

In a recent discovery, cybersecurity experts have uncovered a new variant of the infamous Bifrost remote access trojan (RAT) tailored specifically for Linux systems. This sophisticated malware employs a series of innovative evasion techniques, including the utilization of a deceptive domain cleverly disguised to resemble a legitimate VMware entity.
Having plagued digital landscapes for two decades, Bifrost stands as one of the enduring threats in the realm of RATs. Typically disseminated through malicious email attachments or compromised websites, Bifrost infiltrates systems to pilfer sensitive data.
Researchers from Palo Alto Networks’ Unit 42 have noticed a surge in Bifrost’s activities, prompting an in-depth investigation that led to the revelation of this new, more elusive variant.
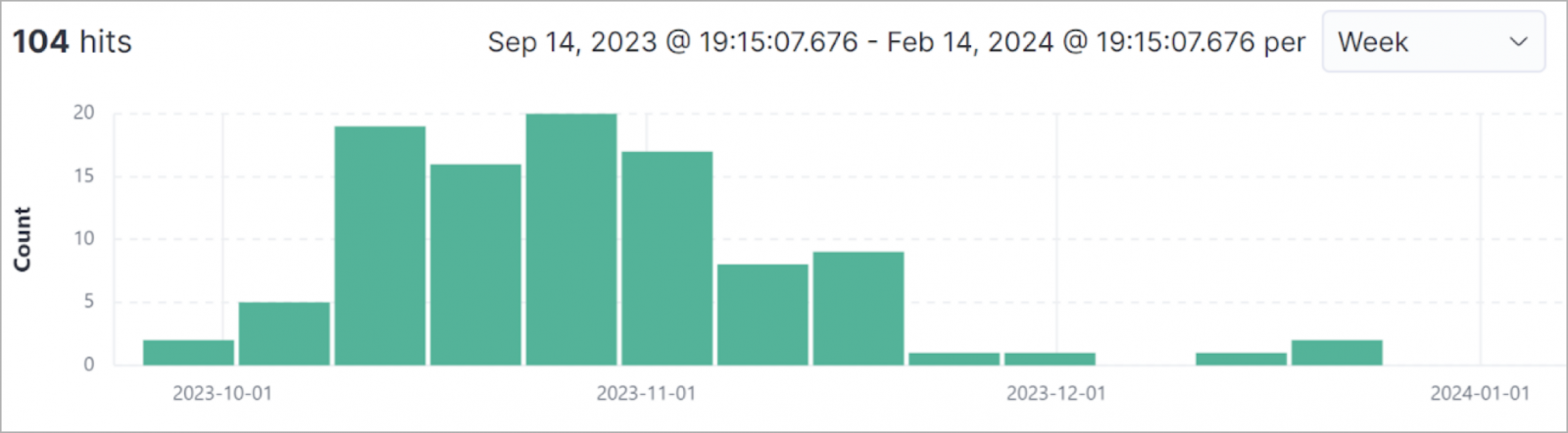 104 new Bitfrost samples captured since October (Unit 42)
104 new Bitfrost samples captured since October (Unit 42)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Enhanced Tactics of the New Bifrost Variant:
Upon scrutinizing the latest Bifrost samples, Unit 42 researchers have uncovered a series of noteworthy updates designed to bolster the malware’s operational efficiency and evade detection.
The malware establishes communication with a command and control (C2) server through the “download.vmfare[.]com” domain, a cunning ruse reminiscent of legitimate VMware domains, thus slipping under the radar of routine inspections. Moreover, the deceptive domain’s resolution involves a Taiwan-based public DNS resolver, further complicating tracing and blocking efforts.
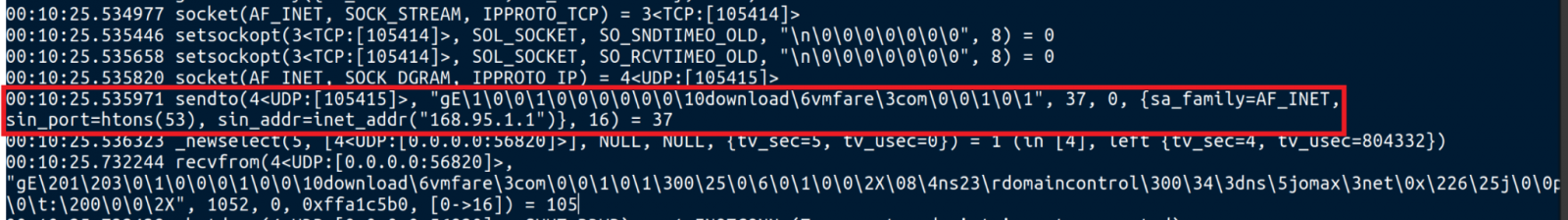 DNS query to resolve the C2 address (Unit 42)
DNS query to resolve the C2 address (Unit 42)
From a technical standpoint, the malware’s binary is compiled in a stripped form devoid of debugging information or symbol tables, rendering analysis more challenging.
Bifrost covertly harvests crucial system information including the victim’s hostname, IP address, and process IDs, encrypting the data with RC4 encryption before transmitting it to the C2 via a newly established TCP socket.
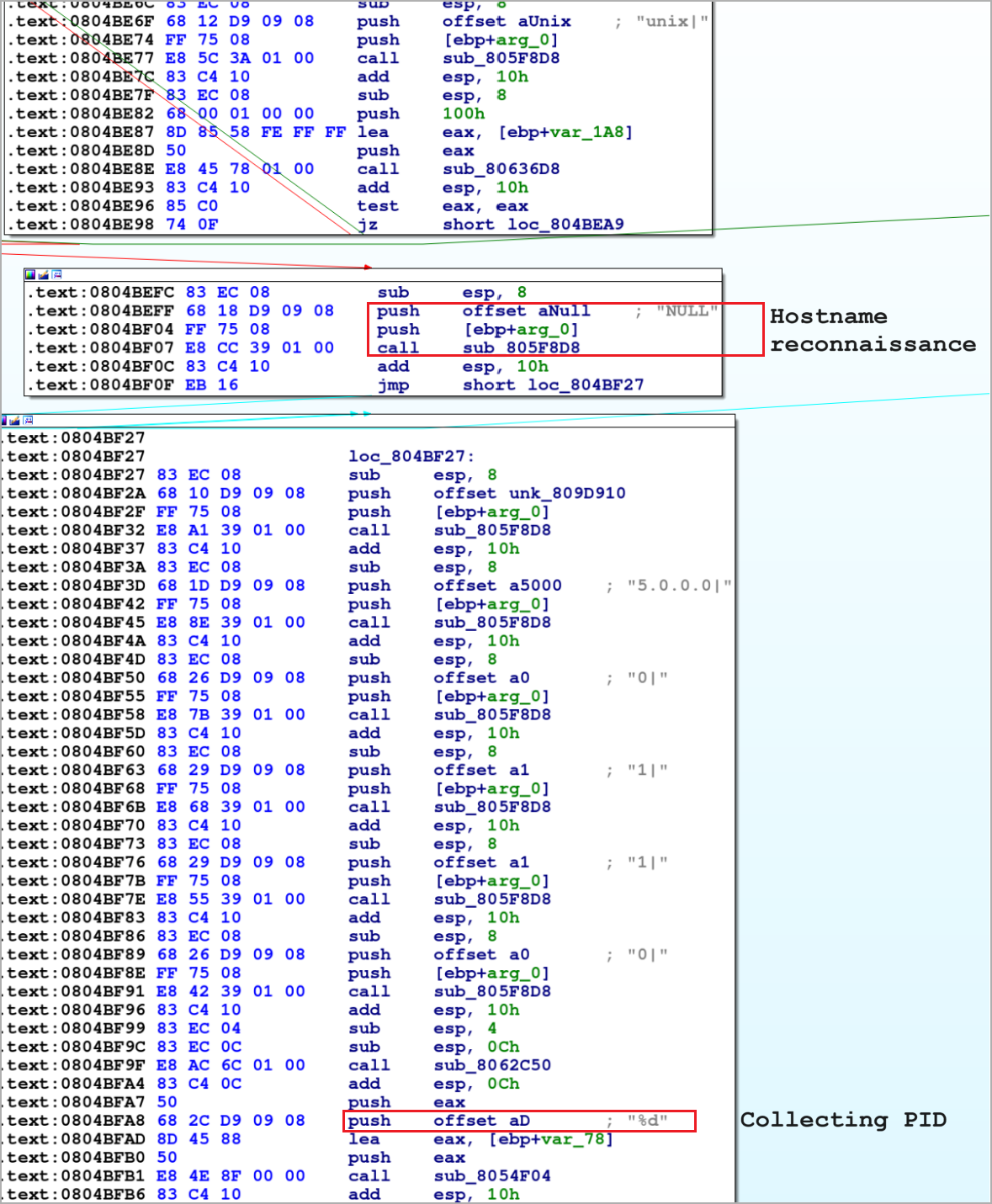 Victim data collection (Unit 42)
Victim data collection (Unit 42)
Trending: Major Cyber Attacks that shaped 2023


