The Evolution of a Cryptomining Threat on macOS: What You Need to Know

Reading Time: 3 Minutes
Evolution of a macOS threat
Security researchers at Jamf Threat Labs have uncovered a new macOS threat that has been targeting users for some time. Disguised as a malicious version of Final Cut Pro, the threat remains largely undetected by antivirus engines, and is distributed over torrent sites. It is believed that the threat was introduced to the platform in 2019, with several other macOS apps also containing a payload for cryptocurrency mining.
Deeper Analysis of the Cryptomining Malware
Further analysis of the malware revealed that it had undergone three major development stages, with each stage introducing increasingly complex evasion techniques. While security tools consistently detect the first generation of the malware, which stopped circulating in April 2021, subsequent generations have largely gone undetected. The second generation of the malware briefly appeared between April and October 2021, and the third and current generation emerged in October 2021.
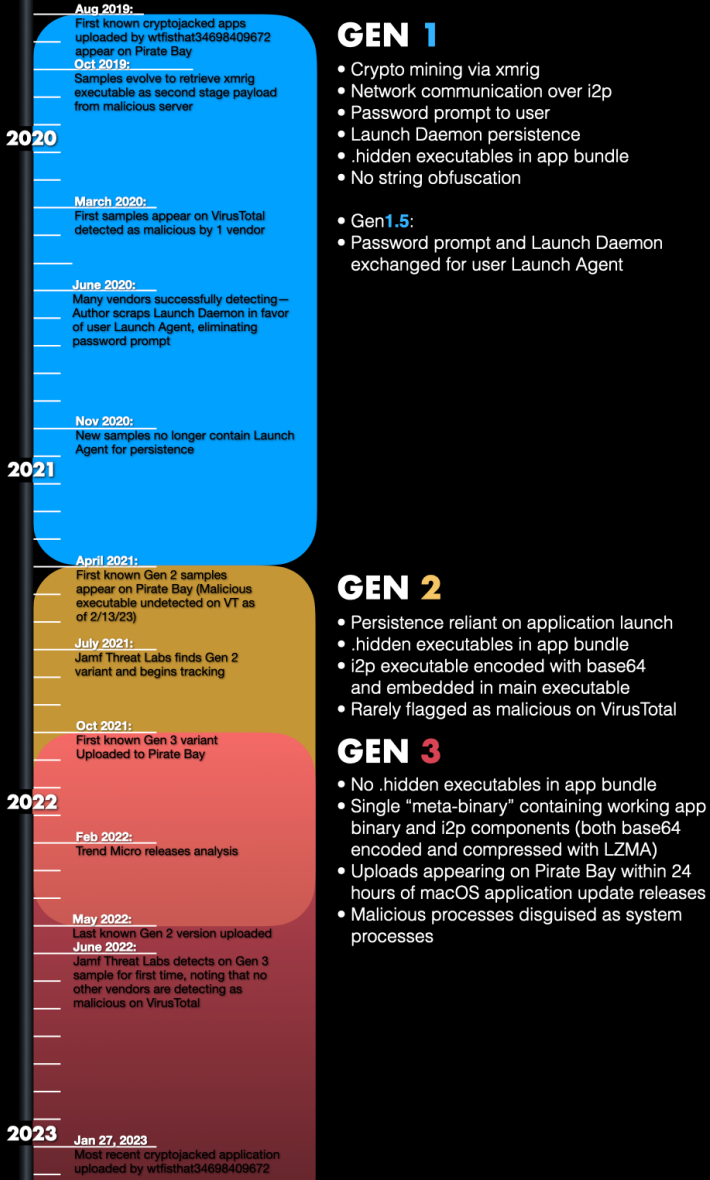 The three generations of the macOS malware (Jamf)
The three generations of the macOS malware (Jamf)
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
Ventura and the Road Ahead
With the release of macOS Ventura, Apple has introduced more stringent code-signing checks that aim to make it difficult to hide and launch malware from inside user-launched apps, particularly pirated ones. Despite this, the pirates behind this malware family have modified Final Cut Pro only partially, and kept the original code-signing certificate intact. This led to Ventura invalidating the legitimate application from running, but not the cryptocurrency miner.
Recommendations for Users
The best way to avoid being affected by this threat is to avoid downloading pirated software from peer-to-peer networks, which are often ridden with malware or adware. While Apple is working on targeted XProtect updates to effectively block the malware, it is important for users to exercise caution when downloading software from untrusted sources. The Mac App Store is the safest place to get software for the Mac, and for software downloaded outside the store, Apple uses industry-leading technical mechanisms to detect and block malware.
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: TerminatorZ
Apple Responds to Cryptomining Malware Targeting macOS
In response to the discovery of this threat, an Apple spokesperson has confirmed that the malware is on their radar, and they are working on targeted XProtect updates to effectively block it. While this malware family isn’t able to bypass Gatekeeper protections, it is still important for users to exercise caution when downloading software from untrusted sources. The Mac App Store provides the safest place to get software for the Mac, and for software downloaded outside the store, Apple uses industry-leading technical mechanisms to detect and block malware.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












