Twilio hackers hit over 130 orgs in massive Okta phishing attack

Hackers responsible for a string of recent cyberattacks, including those on Twilio, MailChimp, and Klaviyo, compromised over 130 organizations in the same phishing campaign.
This phishing campaign utilized a phishing kit codenamed ‘0ktapus’ to steal 9,931 login credentials that the hackers then used to gain access to corporate networks and systems through VPNs and other remote access devices.
According to a Group-IB report, the 0ktapus campaign has been underway since at least March 2022, aiming to steal Okta identity credentials and 2FA codes and use them to carry out subsequent supply chain attacks.
These attacks were very successful, leading to a series of reported data breaches at Twilio, MailChimp, and Klaviyo, and an attempted attack against Cloudflare that was thwarted.
In addition, these breaches also led to supply-chain attacks on customers using these services, such as Signal and DigitalOcean.
Based on the phishing domains created in this campaign, the threat actors targeted companies in multiple industries, including cryptocurrency, technology, finance, and recruiting.
Some of the targeted companies include T-Mobile, MetroPCS, Verizon Wireless, AT&T, Slack, Twitter, Binance, KuCoin, CoinBase, Microsoft, Epic Games, Riot Games, Evernote, AT&T, HubSpot, TTEC, and Best Buy.
.png)
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
The many arms of the 0ktapus
The attack begins with an SMS message and a link to a phishing page impersonating an Okta login page where victims are prompted to enter their account credentials and the 2FA codes.
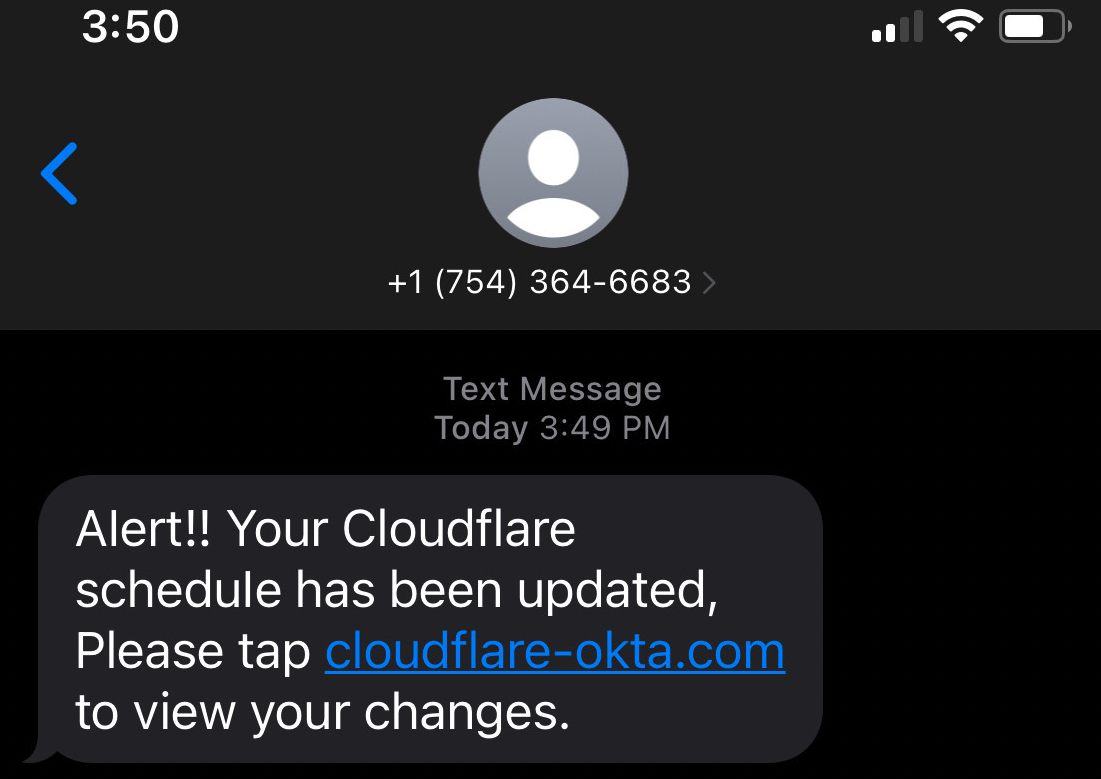
Okta is an identity-as-a-service (IDaaS) platform enabling employees to use a single login to access all software assets in their company.
Researchers discovered 169 unique phishing domains supporting the 0ktapus campaign, using the keywords “OKTA,” “HELP,” “VPN,” and “SSO,” such as the examples below.
t-mobile-okta[.]org
att-citrix[.]com
vzwcorp[.]co
mailchimp-help[.]com
slack-mailchimp[.]com
kucoin-sso[.]comThese sites feature the specific theming of the target companies, so they appear exactly like the genuine portals the employees are used to seeing in their daily login procedure.
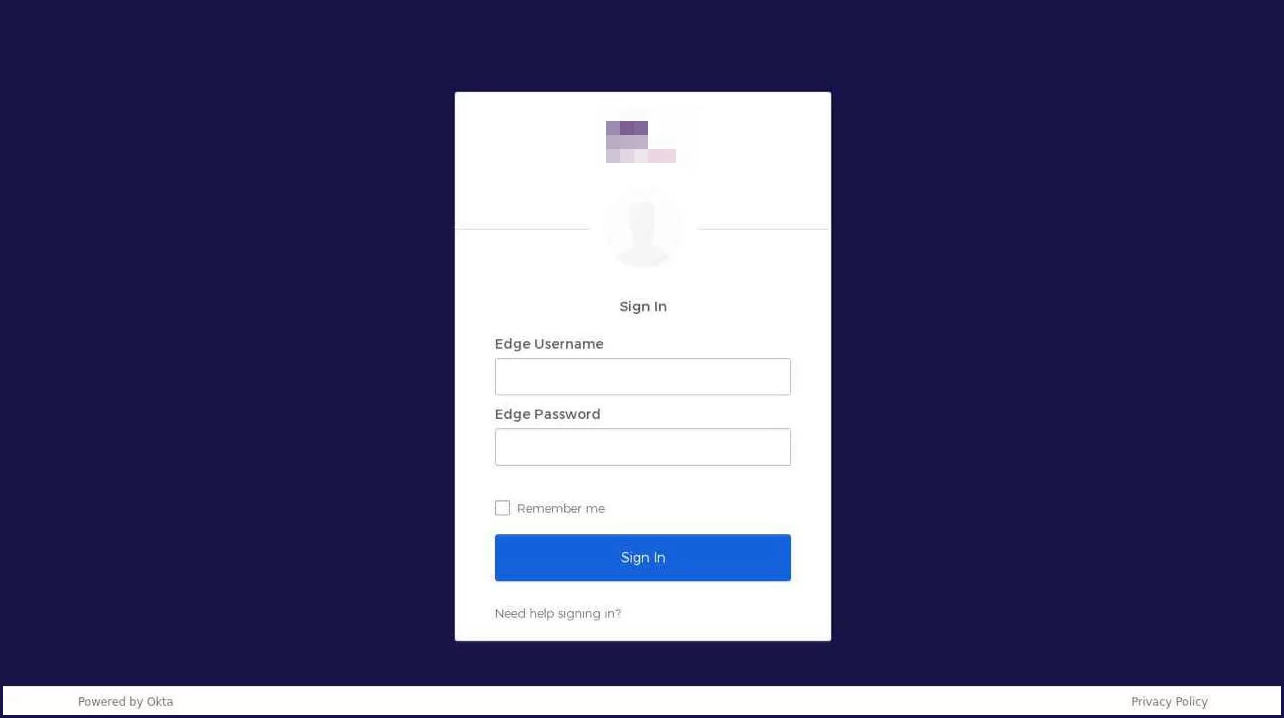
When victims enter their credentials and 2FA codes, the sites transmit them to a private Telegram channel where the threat actors can retrieve them.
The hackers then used these login credentials to gain access to corporate VPNs, networks, and internal customer support systems to steal customer data. This customer data was then used to perform further supply-chain attacks, as we saw with DigitalOcean and Signal.
Based on the disclosures of past victims, the threat actors commonly targeted data belonging to companies in the cryptocurrency industry.
Group-IB says that the threat actors managed to steal 9,931 user credentials from 136 companies, 3,129 records with emails, and 5,441 records with MFA codes, with the majority of the compromised organizations located in the U.S.
.jpg)
Of those, almost half belong to the software and telecom sector, while finance, business services, education, and retail also had significant shares.
See Also: So you want to be a hacker?
Find Hidden Info using Google Dorking manually, and Automated using Pagodo
See Also: So you want to be a hacker?
Recon Tool: Is it alive?
Unmasking user “X”
Group-IB’s investigators leveraged the little info “hiding” in the phishing kit to find the admin account of the Telegram channel used for account data exfiltration.
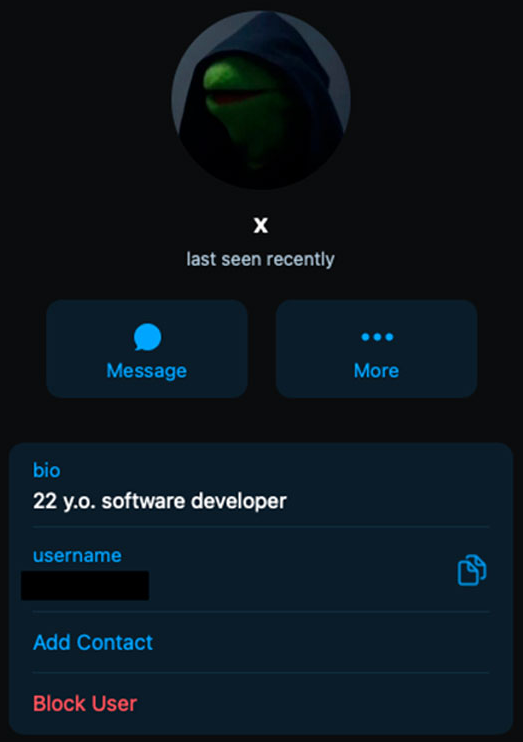
Tracing back the user’s activity, the threat intelligence firm found that in 2019, the user named “X,” posted something pointing to their Twitter account.
From there, the analysts found a GitHub account linked to the hacker, who used the nickname “Subject X” at the time. Group-IB says this account had a location of North Carolina, United States, associated with it.
Group-IB claims to have more information about the alleged identity of the threat actor, but it reserved further details for law enforcement agencies.
See Also: So you want to be a hacker?
Apple security updates fix 2 zero-days used to hack iPhones
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com













