UAC-0184 Employed Steganography for Covert Deployment of Remcos RAT in Targeted Operations

A hacking group identified as ‘UAC-0184’ has recently been detected employing sophisticated tactics, including steganography, to distribute the Remcos remote access trojan (RAT) to the systems of a Ukrainian entity operating in Finland.
This latest activity marks an expansion of UAC-0184’s targeting beyond Ukraine, with their strategic focus extending to organizations affiliated with their primary objectives.
The utilization of steganographic image files serves as a notable departure from conventional attack methods, allowing malicious code to be concealed within the pixel data of images, thus evading detection by signature-based security solutions. Although this tactic may distort the appearance of the image, its effectiveness lies in bypassing automated security measures, particularly those relying on signature-based rules.
Morphisec analysts, who identified the recent activity of UAC-0184, refrained from disclosing specific details about the victim for confidentiality reasons but provided insights into the attack methodology employed.
 Malicious PNG image containing embedded code (Morphisec)
Malicious PNG image containing embedded code (Morphisec)
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
Attack details
The attack chain begins with carefully crafted phishing emails purportedly originating from Ukraine’s 3rd Separate Assault Brigade or the Israel Defense Forces. Recipients deceived into opening the attached shortcut file trigger an infection chain, initiating the execution of an executable file (DockerSystem_Gzv3.exe), which subsequently activates a modular malware loader named ‘IDAT.’
Described by Morphisec as possessing a modular architecture, IDAT distinguishes itself through unique features such as code injection and execution modules, enabling evasion of conventional detection mechanisms. Employing sophisticated techniques including dynamic loading of Windows API functions and process blocklists, IDAT remains elusive to detection efforts.
To maintain stealthiness, API calls within IDAT are resolved at runtime using a decryption key integrated into the attack chain. The malware loader then extracts the encoded payload embedded within the malicious PNG image file, decrypts it, and executes it in memory through multiple stages involving injection into legitimate processes and DLL files.
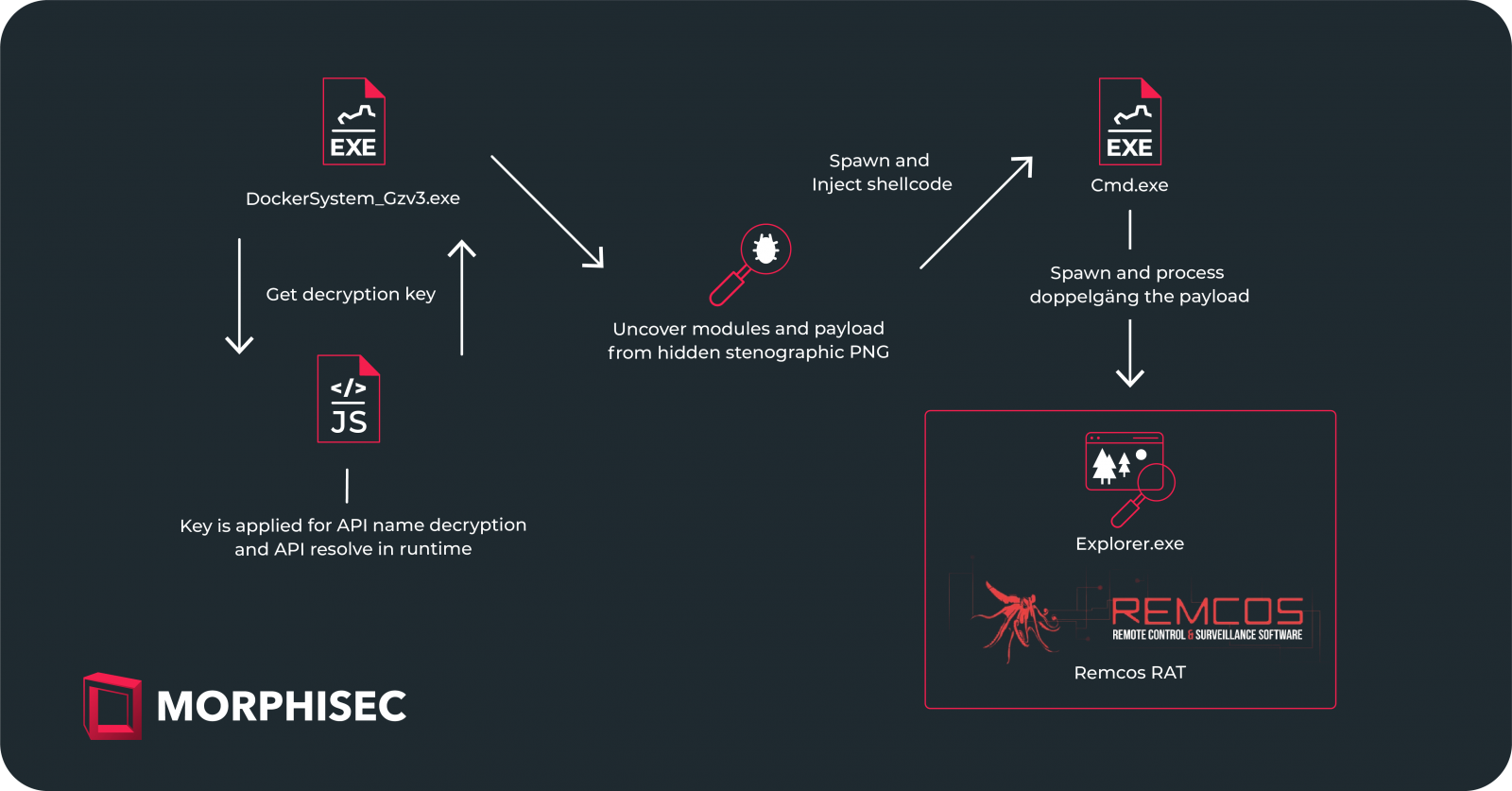 Overview of the UAC-0184 attack (Morphisec)
Overview of the UAC-0184 attack (Morphisec)
Trending: Major Cyber Attacks that shaped 2023


