Uber hacked, internal systems breached and vulnerability reports stolen

Reading Time: 3 Minutes
Uber suffered a cyberattack Thursday afternoon with a hacker gaining access to vulnerability reports and sharing screenshots of the company’s internal systems, email dashboard, and Slack server.
The screenshots shared by the hacker and seen by BleepingComputer show what appears to be full access to many critical Uber IT systems, including the company’s security software and Windows domain.
Other systems the hacker accessed include the company’s Amazon Web Services console, VMware ESXi virtual machines, Google Workspace email admin dashboard, and Slack server, to which the hacker posted messages.
Uber has since confirmed the attack, tweeting that they are in touch with law enforcement and will post additional information as it becomes available.
“We are currently responding to a cybersecurity incident. We are in touch with law enforcement and will post additional updates here as they become available,” tweeted the Uber Communications account.
The New York Times, which first reported on the breach, said they spoke to the threat actor, who said they breached Uber after performing a social engineering attack on an employee and stealing their password.
The threat actor then gained access to the company’s internal systems using the stolen credentials.
Social engineering has become a very popular tactic in recent attacks against well-known companies, including Twitter, MailChimp, Robinhood, and Okta.
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
HackerOne vulnerability reports exposed
While it’s possible that the threat actor stole data and source code from Uber during this attack, they also had access to what could be an even more valuable asset.
According to Yuga Labs security engineer Sam Curry, the hacker also had access to the company’s HackerOne bug bounty program, where they commented on all of the company’s bug bounty tickets.
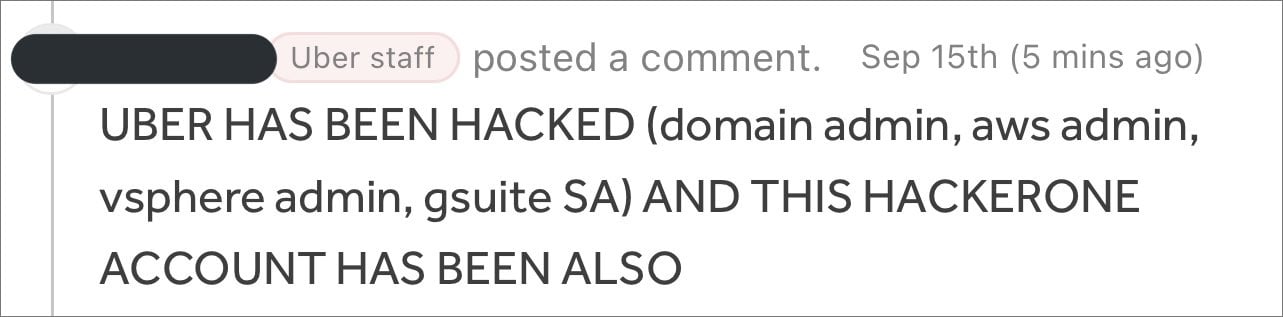
Source: Curry
Curry told BleepingComputer that he first learned of the breach after the attacker left the above comment on a vulnerability report he submitted to Uber two years ago.
Uber runs a HackerOne bug bounty program that allows security researchers to privately disclose vulnerabilities in their systems and apps in exchange for a monetary bug bounty reward. These vulnerability reports are meant to be kept confidential until a fix can be released to prevent attackers from exploiting them in attacks.
Curry further shared that an Uber employee said the threat actor had access to all of the company’s private vulnerability submissions on HackerOne.
BleepingComputer was also told by a source that the attacker downloaded all vulnerability reports before they lost access to Uber’s bug bounty program. This likely includes vulnerability reports that have not been fixed, presenting a severe security risk to Uber.
Trending: Security Engineer vs. Software Engineer
Trending: Recon Tool: ZenBuster
HackerOne has since disabled the Uber bug bounty program, cutting off access to the disclosed vulnerabilities.
However, it would not be surprising if the threat actor had already downloaded the vulnerability reports and would likely sell them to other threat actors to cash out on the attack quickly.
BleepingComputer has reached out to Uber with further questions about the attack but has not heard back at this time.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












