Ukrainian Military Targeted in Phishing Campaign Using Drone Manuals as Lures

Ukrainian military entities have been subjected to a sophisticated phishing campaign that employs an intriguing lure – drone manuals. This campaign, known as STARK#VORTEX, has been meticulously orchestrated to target Ukrainian military personnel and organizations. The threat actor behind this campaign, tracked as UAC-0154 by CERT-UA (Computer Emergency Response Team Ukraine), has strategically crafted malicious documents designed to exploit the Ukrainian military’s reliance on Unmanned Aerial Vehicles (UAVs).
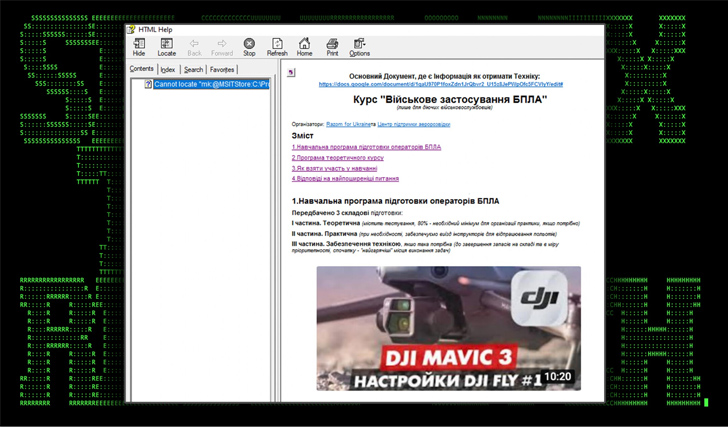
In the world of modern warfare, drones have become indispensable tools for reconnaissance, surveillance, and even offensive operations. Understanding the importance of drones in the Ukrainian military’s arsenal, the threat actor behind STARK#VORTEX has chosen a highly relevant and convincing lure – UAV service manuals.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
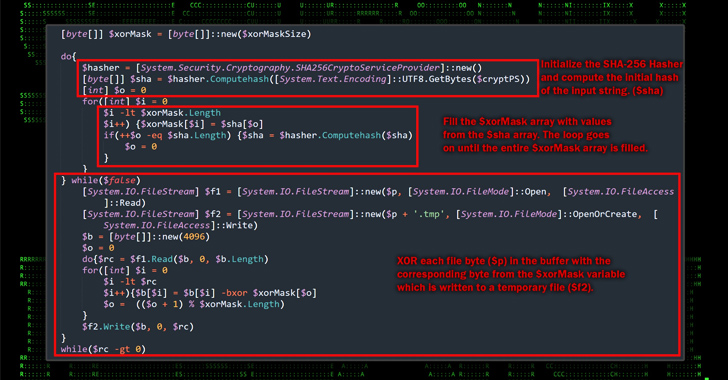
The attack begins with the delivery of a seemingly innocuous Microsoft Compiled HTML Help (CHM) file. When unsuspecting recipients open this file, it triggers a cascade of malicious actions. Hidden within one of the HTML pages is malicious JavaScript code. This JavaScript, when executed, proceeds to run PowerShell code. The primary purpose of this code is to establish a connection with a remote server from which it retrieves an obfuscated binary.
What makes this campaign particularly concerning is the fact that the files and documents utilized in the attack are adept at evading conventional security defenses. This level of sophistication suggests a well-resourced threat actor with a deep understanding of the Ukrainian military’s operations and procedures.
This campaign underscores the ever-evolving tactics employed by cyber threat actors to target not just military organizations but also critical infrastructure and sensitive sectors. As such, it serves as a stark reminder of the need for constant vigilance and robust cybersecurity measures to safeguard against these evolving threats.
Trending: Recon Tool: Goblyn
The situation also highlights the broader issue of cyber espionage, where state-sponsored threat actors target not only other nations’ military but also civilian organizations, activists, and dissidents. The importance of maintaining strong cybersecurity practices, user education, and threat intelligence sharing cannot be overstated in this complex and ever-changing landscape.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












