Unveiling the First Undetectable Cloud-Based Cryptocurrency Miner on Microsoft Azure
Reading Time: 3 Minutes
Cybersecurity researchers at SafeBreach have made a groundbreaking discovery, developing the world’s first fully undetectable cloud-based cryptocurrency miner that leverages the power of Microsoft Azure Automation. This innovative miner operates without incurring any charges, raising serious concerns about the security implications it poses.
SafeBreach’s security researcher, Ariel Gamrian, emphasized the significance of this research, stating that while its impact on cryptocurrency mining is noteworthy, the techniques employed could have far-reaching consequences in various domains. The ability to execute code on Azure without attracting attention opens the door to achieving any task that requires code execution.
The study’s primary objective was to identify the “ultimate crypto miner” that offers unlimited access to computational resources, requires minimal maintenance, incurs no costs, and remains undetectable. This is where Azure Automation, a cloud-based automation service developed by Microsoft, comes into play. It enables users to automate the creation, deployment, monitoring, and maintenance of resources within Azure.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
SafeBreach uncovered a bug in the Azure pricing calculator, allowing for the execution of an infinite number of jobs without any charges. However, it’s important to note that this bug only affects the attacker’s environment. Microsoft has promptly addressed the issue by issuing a fix.
Another method discovered by SafeBreach involves creating a test job for mining, marking it as “Failed,” and subsequently creating a dummy test job, taking advantage of the limitation that only one test can run at a time. This clever approach effectively conceals code execution within the Azure environment.
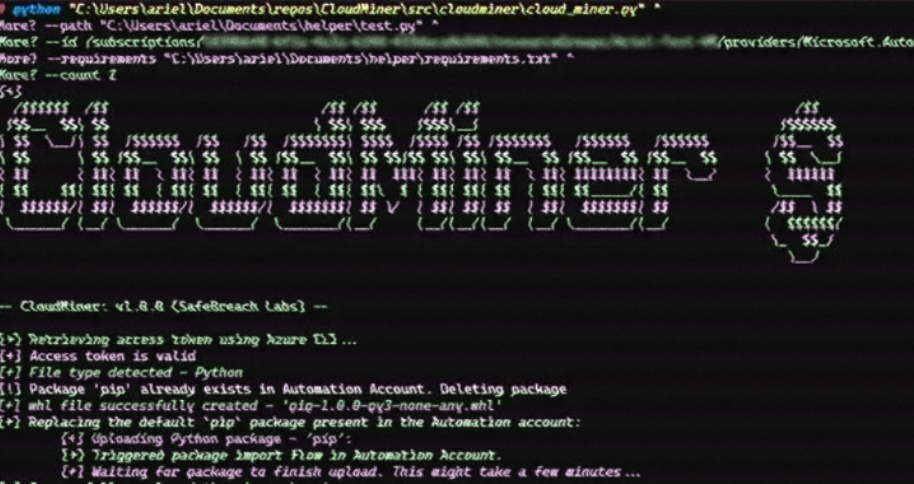
To achieve code execution, threat actors can leverage Azure Automation’s feature that allows users to upload custom Python packages. By creating a malicious package named ‘pip’ and uploading it to the Automation Account, the attacker can replace the legitimate ‘pip’ and gain control over the package upload mechanism.
Trending: Offensive Security Tool: o365sprayer
SafeBreach has developed a proof-of-concept called CloudMiner, which demonstrates how free computing power can be obtained within the Azure Automation service using the Python package upload mechanism. Microsoft, in response to these findings, has characterized the behavior as “by design,” indicating that the method can still be exploited without incurring charges.
While the focus of this research is on the abuse of Azure Automation for cryptocurrency mining, SafeBreach warns that threat actors could repurpose these techniques to achieve any task requiring code execution on Azure. As a result, organizations utilizing cloud services must proactively monitor their resources and actions within their environment to detect and prevent such malicious behavior.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: thehackernews.com












