Widespread ‘I Can’t Believe He Is Gone’ Facebook Phishing Scam Targets Users Through Hacked Accounts

A pervasive Facebook phishing campaign, employing a heart-wrenching message – “I can’t believe he is gone. I’m gonna miss him so much,” is luring unsuspecting users into a web of deceit by redirecting them to a site designed to steal Facebook credentials.
This ongoing phishing attack, widely disseminated on Facebook through compromised accounts of friends, serves as a breeding ground for a substantial inventory of stolen accounts, strategically amassed for potential exploitation in further scams on the social media platform.
Given that the phishing posts originate from hacked accounts of friends, they carry an air of authenticity, making them more convincing and thereby tricking numerous users into falling prey to the scam.
See Also: So, you want to be a hacker?
Offensive Security, Bug Bounty Courses
The campaign, which commenced approximately a year ago, poses a persistent challenge for Facebook to thwart as it continues to circulate. Although Facebook deactivates the redirect links in reported posts, new ones keep emerging.
The ‘I can’t believe he is gone’ scam manifests in two variants. The first straightforwardly presents the message and includes a Facebook redirect link. The second, while sharing the same text, displays what seems to be a BBC News video depicting a car accident or crime scene.
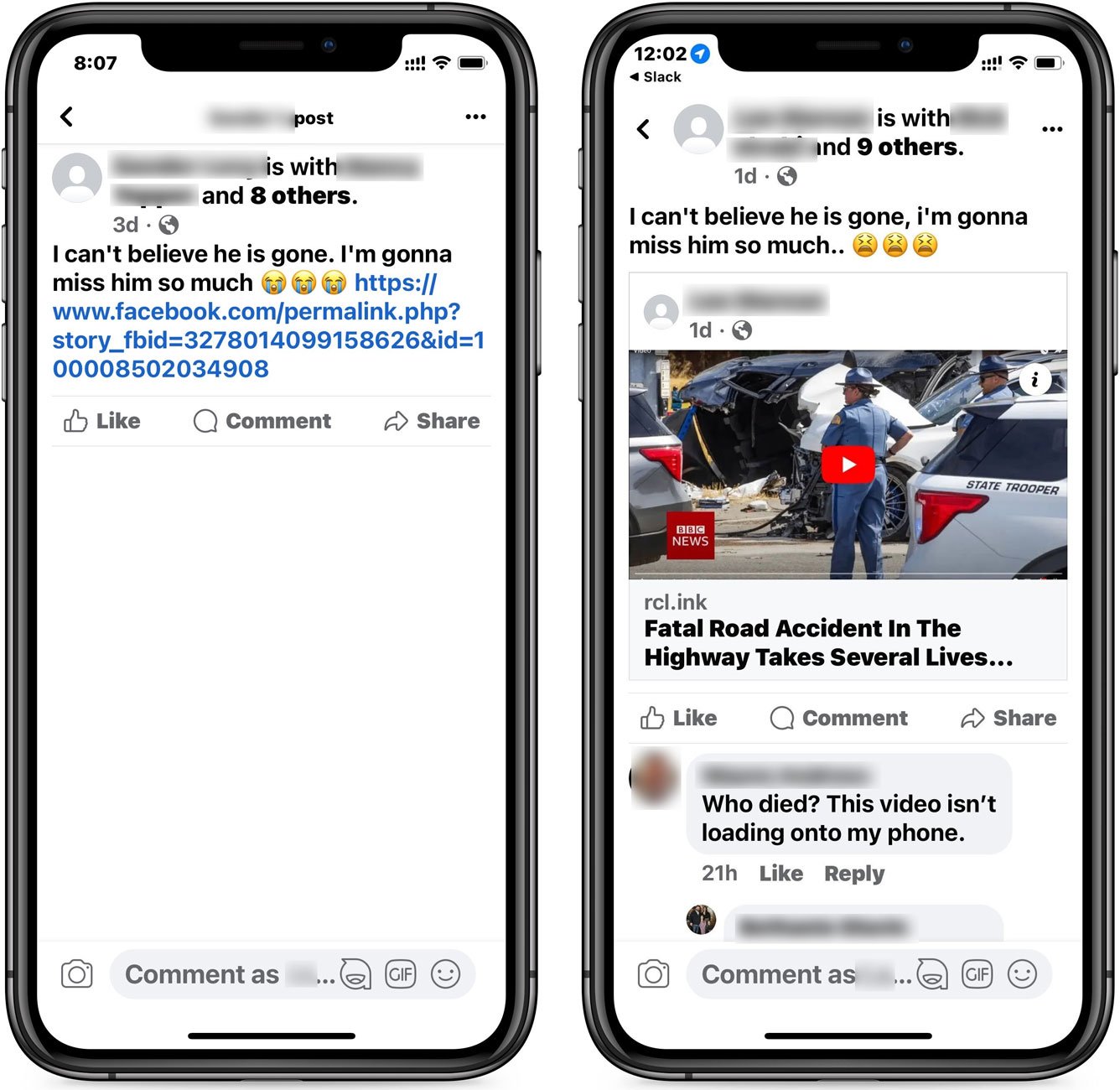 Facebook “I’m gonna miss him so much” phishing posts
Facebook “I’m gonna miss him so much” phishing posts
Source: BleepingComputer
Upon testing the links, users clicking from the Facebook app on mobile devices are directed to a deceptive news site named ‘NewsAmericaVideos.’ Here, visitors are prompted to enter their Facebook credentials under the guise of confirming their identity to watch the video. The background displays a blurred-out video, an illusion created with an image downloaded from Discord.
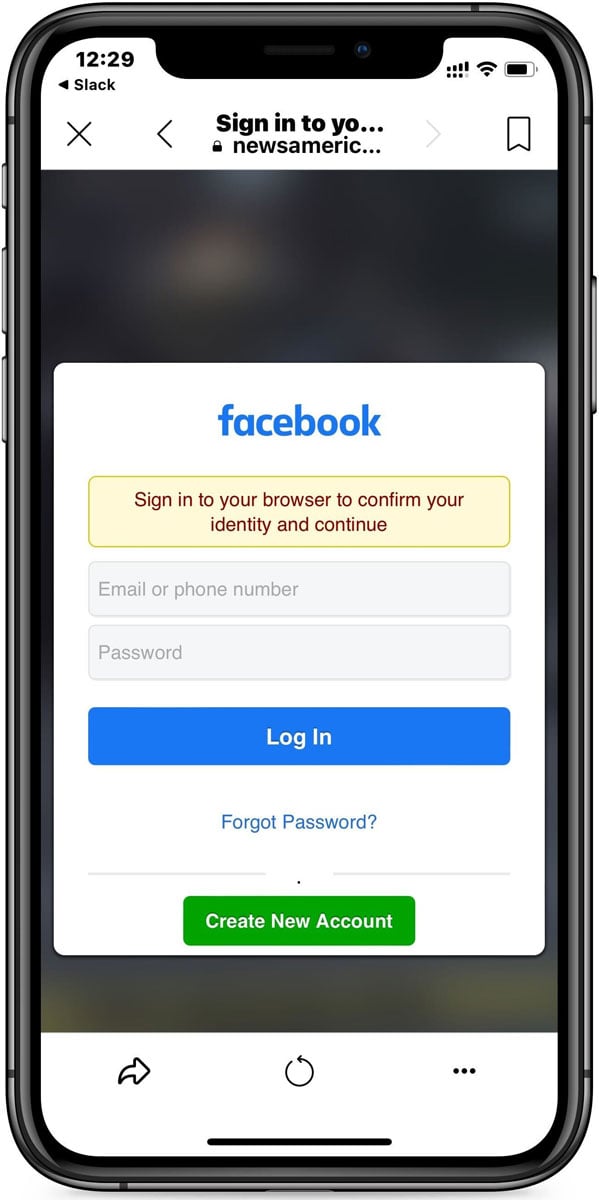 Facebook phishing page
Facebook phishing page
Source: BleepingComputer
Entering credentials on this fraudulent site empowers threat actors to pilfer them, subsequently redirecting users to Google. While the ultimate purpose of the stolen credentials remains unknown, it is suspected that threat actors leverage them to perpetuate the same phishing posts through compromised accounts.
Trending: Jeff Foley – OWASP Amass Founder
Trending: OSINT Tool: apk2url
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: info@blackhatethicalhacking.com
Source: bleepingcomputer.com













