WiKI-Eve: Intercepting Smartphone Keystrokes via WiFi for Password Theft

A newly identified attack, named ‘WiKI-Eve,’ has the capability to intercept the cleartext transmissions of smartphones connected to modern WiFi routers. This attack can deduce individual numeric keystrokes with an accuracy rate of up to 90%, thereby enabling the theft of numeric passwords.
WiKI-Eve takes advantage of BFI (beamforming feedback information), a feature introduced with WiFi 5 (802.11ac) in 2013. BFI allows devices to send feedback about their position to routers, aiding in the precise direction of their signals.
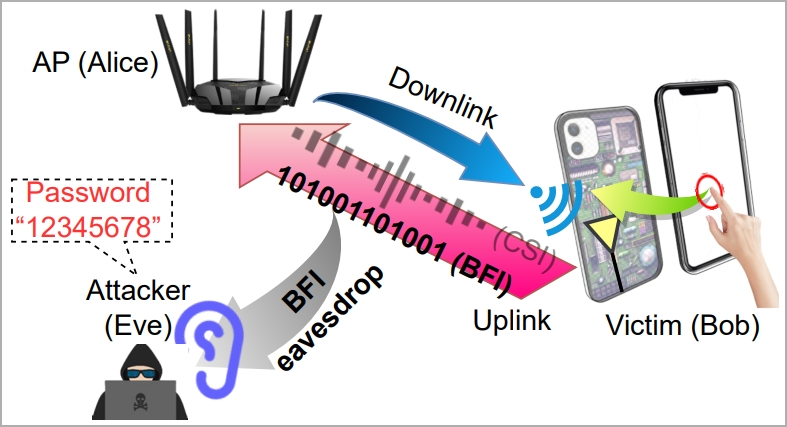 Overview of the WiKI-Eve attack (arxiv.org)
Overview of the WiKI-Eve attack (arxiv.org)
However, the vulnerability lies in the fact that BFI data is exchanged in cleartext, making it susceptible to interception and immediate use, without the need for hardware hacking or encryption key cracking.
This security gap was discovered by a group of researchers from universities in China and Singapore. They conducted tests to retrieve potential secrets from these transmissions.
Their findings revealed that it’s relatively easy to identify numeric keystrokes with an accuracy rate of 90%, decode 6-digit numeric passwords with an 85% accuracy, and discern complex app passwords with an accuracy rate of approximately 66%.
While this attack specifically targets numeric passwords, a study by NordPass showed that 16 out of the top 20 passwords are purely numeric.
WiKI-Eve Attack
The WiKI-Eve attack operates in real-time, intercepting WiFi signals during password entry. To carry out this attack, the attacker must actively monitor the target while they use their smartphone and attempt to access a specific application.
.jpg) Finger movement and taps creating BFI signal variations (arxiv.org)
Finger movement and taps creating BFI signal variations (arxiv.org)
Identification of the target is crucial, and the attacker may use an identity indicator on the network, such as a MAC address, requiring some preparatory work.
In the attack’s primary phase, the attacker captures the victim’s BFI time series during password entry using a traffic monitoring tool like Wireshark. Each time the user presses a key, it affects the WiFi antennas behind the screen, generating a distinct WiFi signal.
See Also: So you want to be a hacker?
Offensive Security, Bug Bounty Courses
However, the recorded BFI series may blur the boundaries between keystrokes. To address this, the researchers developed an algorithm to parse and restore usable data.
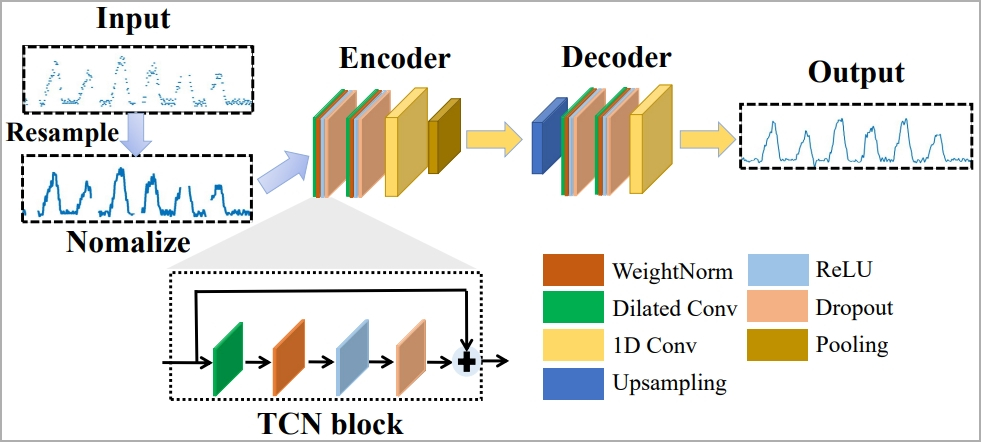 Neural model to parse captured data (arxiv.org)
Neural model to parse captured data (arxiv.org)
To filter out factors that could interfere with results, such as typing style, speed, adjacent keystrokes, and more, machine learning in the form of a “1-D Convolutional Neural Network” is employed.
The researchers used this system to consistently recognize keystrokes, regardless of typing styles, through a concept called “domain adaptation,” which includes a feature extractor, a keystroke classifier, and a domain discriminator.
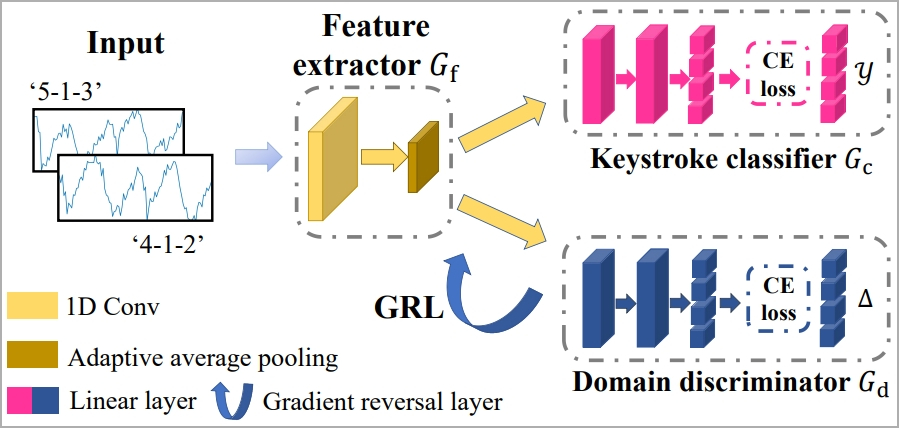 Training of ML framework for WiKI-Eve (arxiv.org)
Training of ML framework for WiKI-Eve (arxiv.org)
Ultimately, a “Gradient Reversal Layer” (GRL) is applied to suppress domain-specific features, allowing the model to learn consistent keystroke representations across domains.
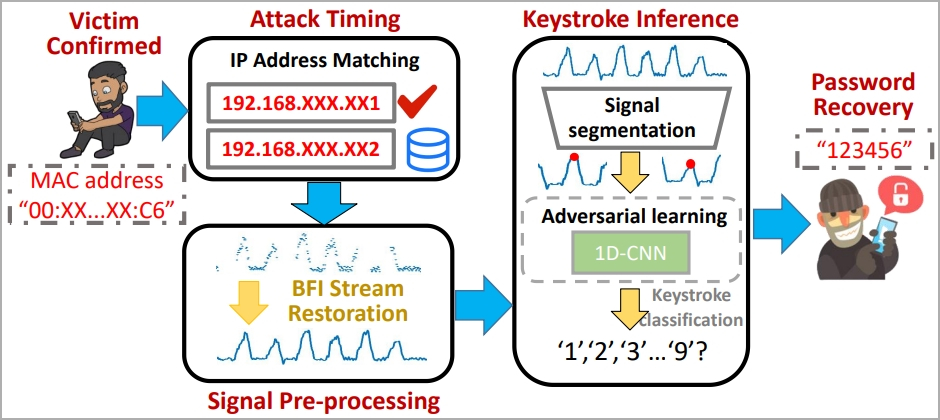 WiKI-Eve attack steps (arxiv.org)
WiKI-Eve attack steps (arxiv.org)
Results of the Attack
In experiments with WiKI-Eve using a laptop and WireShark, the researchers also noted that a smartphone could be used as an attacking device, although it may have limitations regarding the number of supported WiFi protocols.
The experiments, which involved 20 participants using various phone models and typing different passwords, showed that WiKI-Eve’s keystroke classification accuracy remained stable at 88.9% when employing sparse recovery algorithms and domain adaptation.
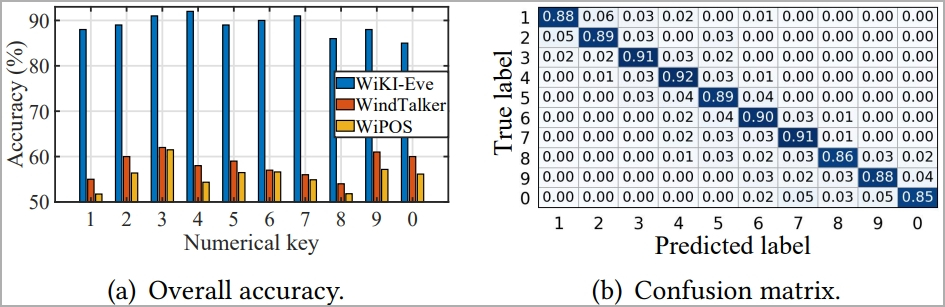 Overall accuracy of WiKI-Eve compared to CSI-targeting models (arxiv.org)
Overall accuracy of WiKI-Eve compared to CSI-targeting models (arxiv.org)
Trending: OSINT Tool: Photon
For six-digit numerical passwords, WiKI-Eve successfully inferred them with an 85% success rate in under a hundred attempts, maintaining a success rate of over 75% in all tested environments.
However, the distance between the attacker and the access point is crucial. Increasing the distance from 1 meter to 10 meters resulted in a 23% decrease in the success rate.
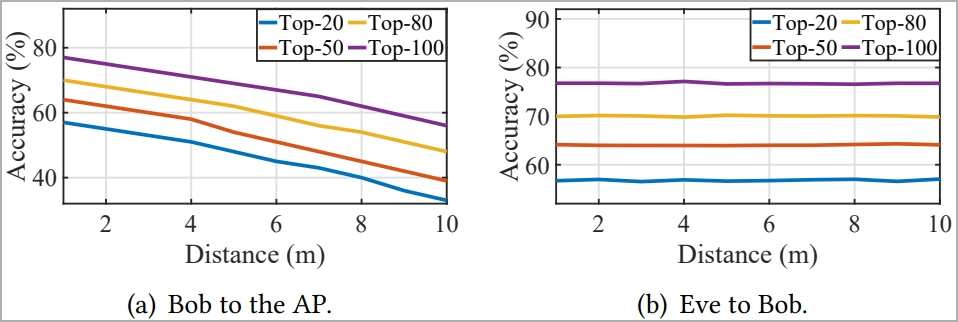 Effect of distance in guessing performance (arxiv.org)
Effect of distance in guessing performance (arxiv.org)
In a scenario emulating a real attack, WiKI-Eve deduced user passwords for WeChat Pay with an accuracy rate of 65.8%. The model consistently predicted the correct password within its top 5 guesses in over 50% of the tests, indicating a 50% chance for an attacker to gain access before reaching the security threshold of five incorrect password attempts.
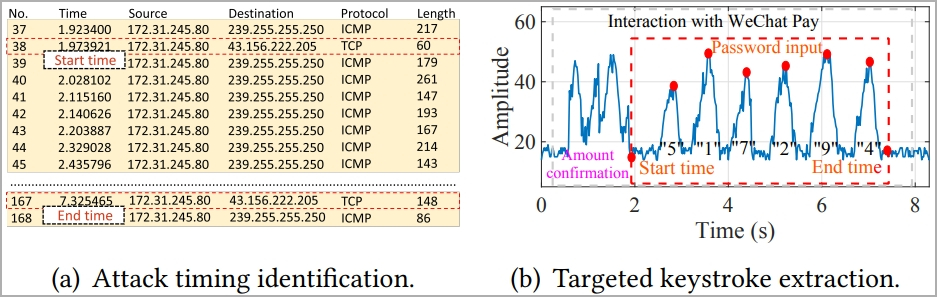 Attack on WeChat password (arxiv.org)
Attack on WeChat password (arxiv.org)
In conclusion, the research highlights the capability of adversaries to deduce secrets without hacking access points, simply by using network traffic monitoring tools and machine learning frameworks. This underscores the need for enhanced security measures in WiFi access points and smartphone apps, including features such as keyboard randomization, data traffic encryption, signal obfuscation, CSI scrambling, WiFi channel scrambling, and more.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com












