Windows vulnerable driver blocklist sync issue patched

Reading Time: 3 Minutes
Microsoft says it addressed an issue preventing the Windows kernel vulnerable driver blocklist from being synced to systems running older Windows versions.
This blocklist (stored in the DriverSiPolicy.p7b file) is designed to block threat actors from dropping legitimate but vulnerable drivers on targets’ systems in Bring Your Own Vulnerable Driver (BYOVD) attacks on HVCI-enabled Windows machines or those running Windows in S Mode.
The flawed drivers are then exploited to escalate privileges in the Windows kernel and execute malicious code, disabling security solutions and taking control of the device.
This is a well-known and popular attack technique amongst threat actors of all skill levels, from ransomware gangs to state-sponsored hacking groups.
Although Microsoft has been advertising its driver blocklist as capable of hardening Windows systems against vulnerable third-party drivers, ANALYGENCE security analyst Will Dormann found that wasn’t the case.
As Dormann discovered, unlike Windows 11 devices, even up-to-date Windows 10 and Windows Server systems were being provided with an outdated list of vulnerable drivers from December 2019, exposing customers who thought they were protected to BYOVD attacks.
Microsoft reluctantly acknowledged his findings and promised to address this issue and update its misleading online support docs.
Thanks for all the feedback. We have updated the online docs and added a download with instructions to apply the binary version directly. We're also fixing the issues with our servicing process which has prevented devices from receiving updates to the policy.
— Jeffrey Sutherland (@j3ffr3y1974) October 6, 2022
See Also: So you want to be a hacker?
Complete Offensive Security and Ethical Hacking Course
Driver blocklist sync finally fixed
More than a month after Dormann revealed that the list of vulnerable drivers wasn’t kept up to date on Windows 10 and some Windows Server systems, Microsoft has now finally addressed this issue.
“The vulnerable driver list is regularly updated, however we received feedback there has been a gap in synchronization across OS versions,” a Microsoft spokesperson told BleepingComputer.
“We have corrected this and it will be serviced in upcoming and future Windows Updates. The documentation page will be updated as new updates are released.”
Unfortunately, this “gap” meant that the driver blocklist was not synced with any Windows 10 systems since 2019 even though Microsoft kept updating on their end, effectively breaking the feature.
Redmond has addressed the driver blocklist sync issue with the October 2022 preview updates, ensuring that the blocklist is the same across Windows 10 and 11.
Trending: Offensive Security Tool: Monkey365
Disabling the driver blocklist
Microsoft also says that starting with the Windows 11 2022 update (version 22H2), the blocklist is enabled by default on all devices.
“Blocking drivers can cause devices or software to malfunction. In rare cases, it leads to a stop error,” Microsoft warned on Tuesday. “There is no guarantee that the blocklist will block every driver that has weaknesses.”
For Windows 10 and Windows 11 21H2, you can disable the driver blocklist by turning off ‘Memory Integrity’ in the ‘Core Isolation’ settings, or if using Windows Defender Application Control (WDAC), disabling it in your configuration.
However, as the driver blocklist is enabled by default in Windows 11 22H2, even when Memory Integrity is disabled, it’s unclear how to disable the blocklist in the latest version of the operating system.
Furthermore, Microsoft provides instructions for disabling the driver blocklist using a settings toggle, which does not exist in the production release of Windows 11 22H2, and only exists in Windows Insider builds.
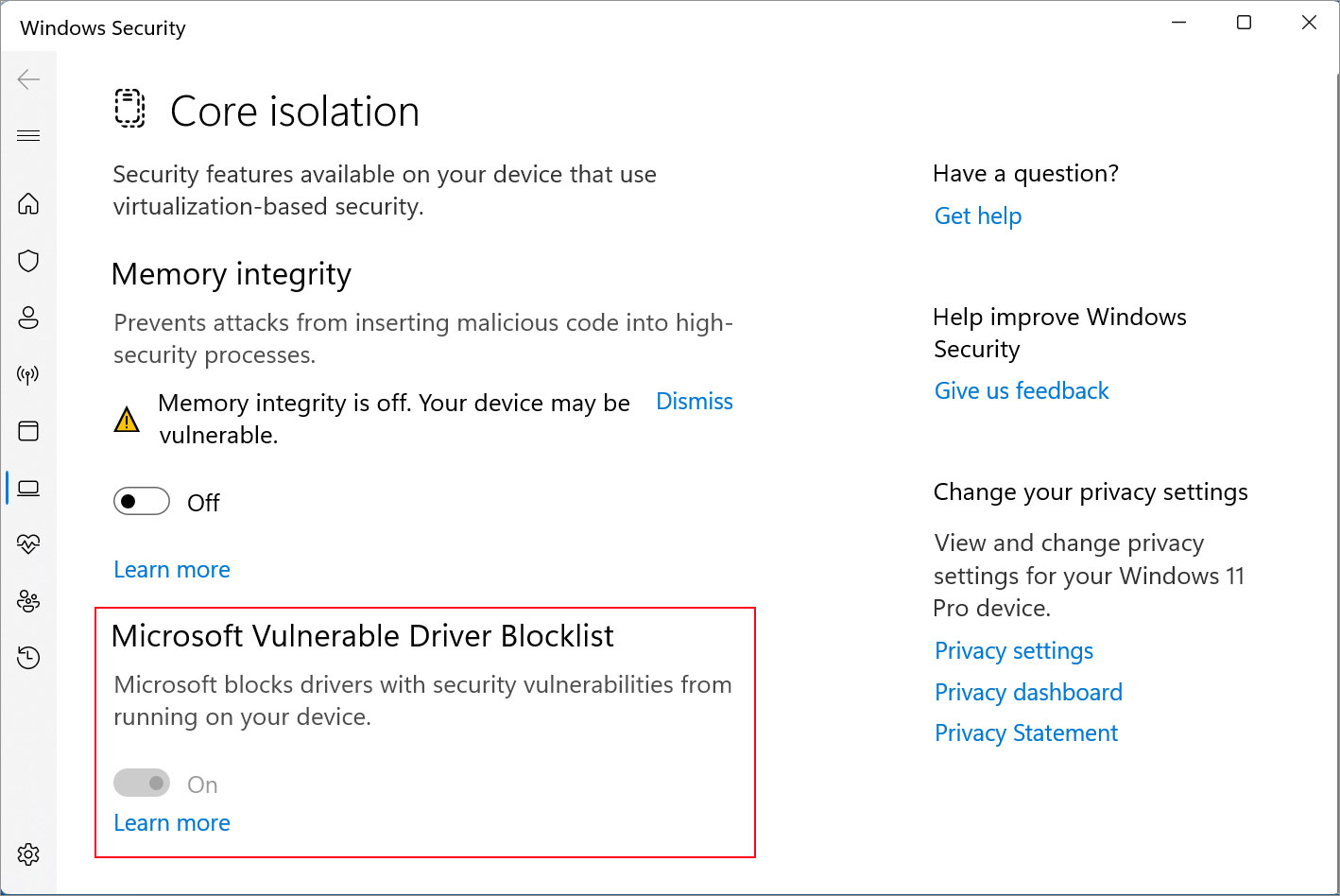
Even in Windows 11 22H2 Insider builds, BleepingComputer could not figure out a way to actually use that toggle to disable the blocklist, so it may be an in-development feature.
Dormann told BleepingComputer it is possible to disable the blocklist using an undocumented Registry value. However, as there is no official documentation on this Registry setting from Microsoft, it should be used with caution.
Are u a security researcher? Or a company that writes articles or write ups about Cyber Security, Offensive Security (related to information security in general) that match with our specific audience and is worth sharing?
If you want to express your idea in an article contact us here for a quote: [email protected]
Source: bleepingcomputer.com